太极
给了提示
部分flag组成: wucup tieny-
太极生两仪-两仪生四象-四象生八卦-八卦定吉凶-吉凶生大业,可以看出是拼音,顺序取每个字的1,2,3,4,5个字母,超出长度的就取余得到flag
tieny-lieig-sieau-bunig-jieay
原神启动
直接lsb拿到第一个压缩包密码

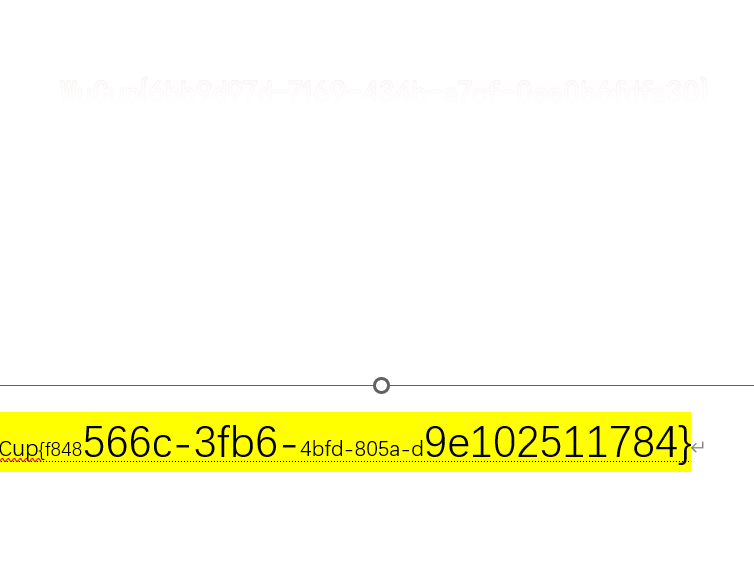
解压拿到world,找到一个图片也有一段flag 在这个图片下面有隐藏的flag
 之后解压压缩包即可拿到flag
之后解压压缩包即可拿到flag
misc 签到
直接cyberchef hex解密即可拿到flag
旋转木马
编写脚本53轮base64解密即可拿16进制的字符直接cyberchef解密得到flag
1 | import base64 |
Sign
签到题,蚁剑连接即可
Easy
丢给gpt,直接出脚本:
1 | # Flag.txt 中的密文 |
HotDog
进入程序后我们可以看见有按钮,所以我们用jadx逆向一下看看有没有onclick,来到onclick可以看见有verify函数
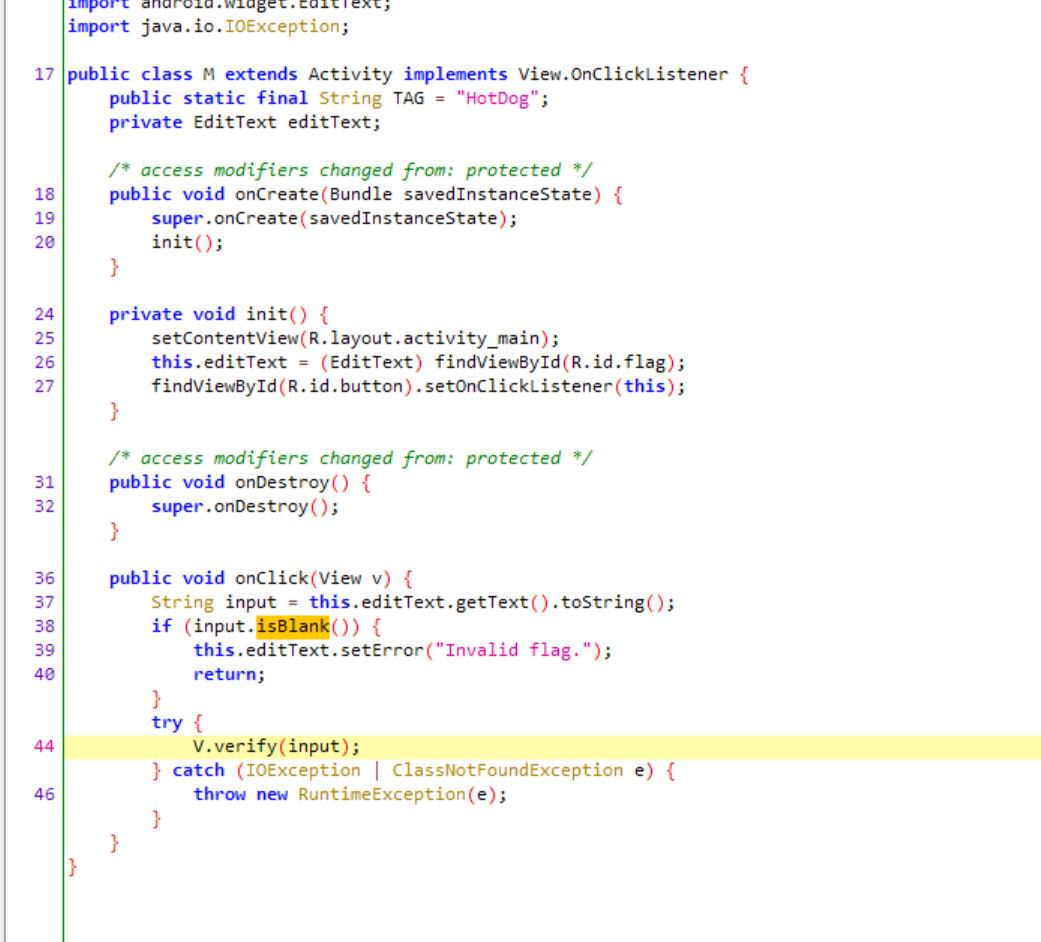
但是verify里面是空的
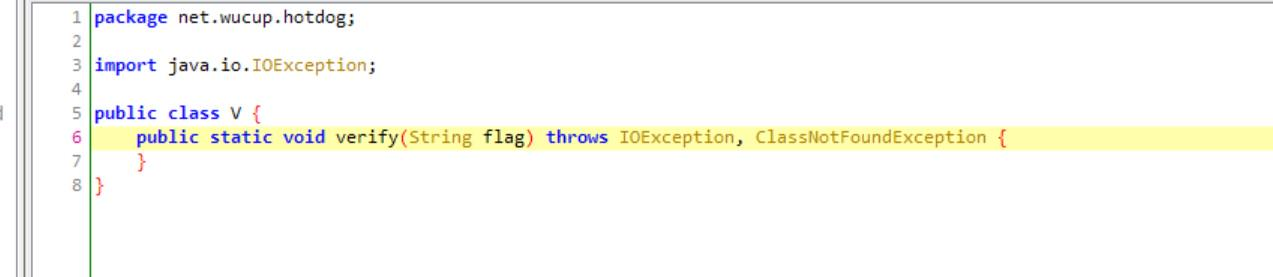
我们在另一个类里可以看见其引用类动态链接库,我们去动态链接库里看一看
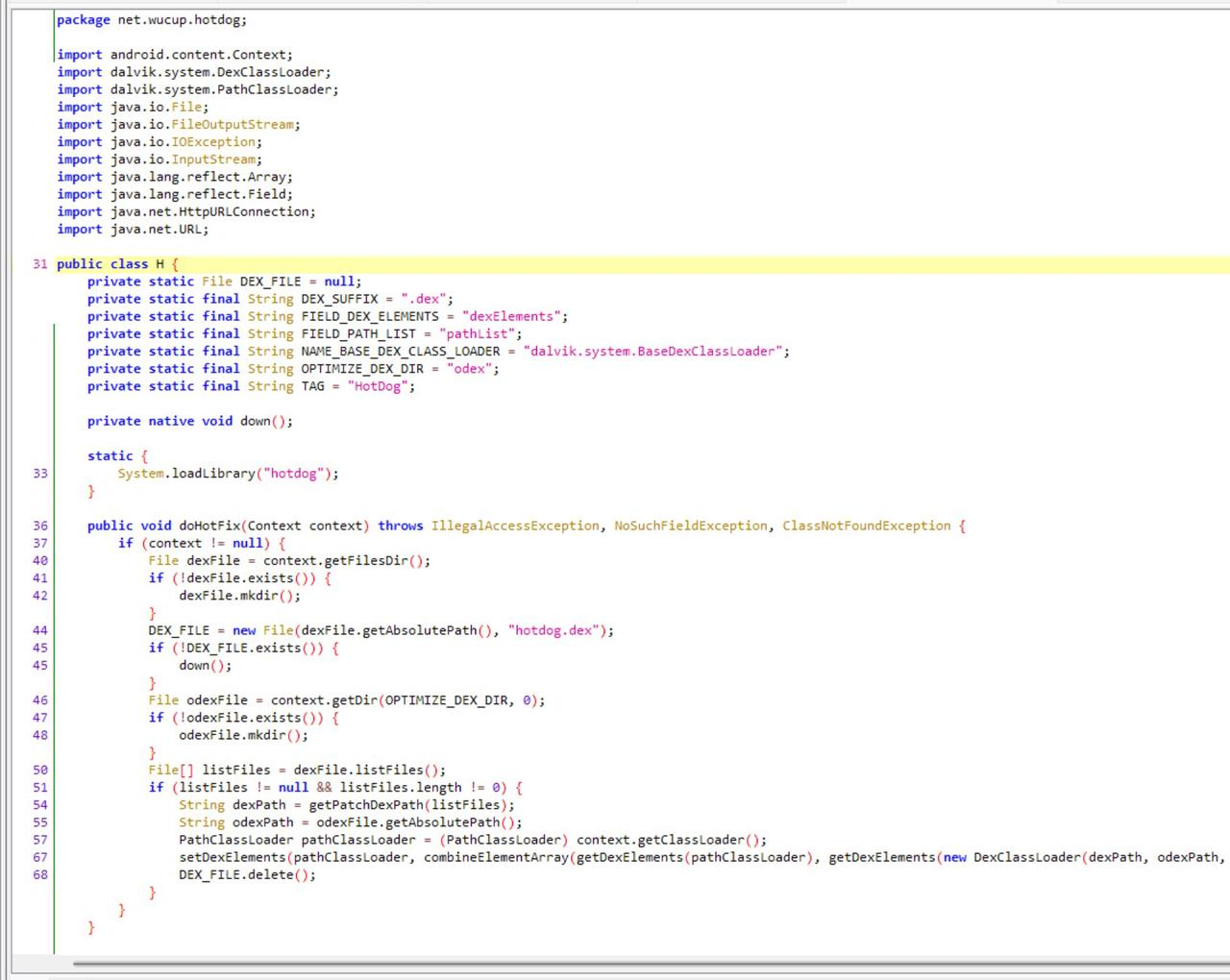
然后我们看一下so文件发现有个解密函数我们解密一下
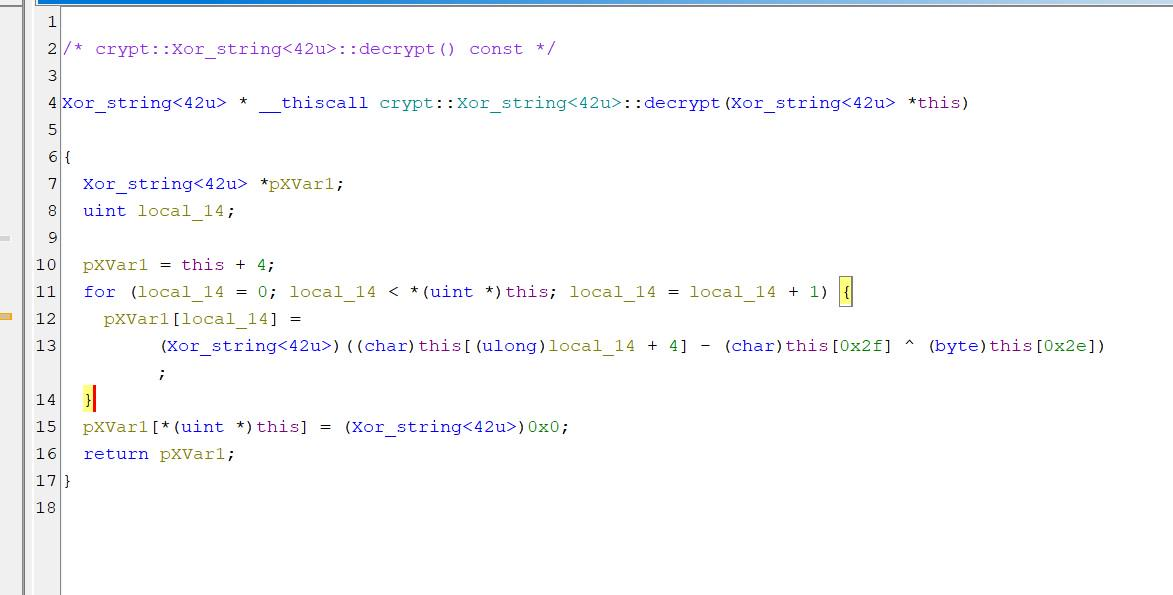
1 | key1= 0x7b |
解出来是一个网址,可以下载补全apk的dex文件,然后我们打开dex文件进行分析
在encryptCbc中,实现了3des加密,然后key和iv都是从data里面读取的。
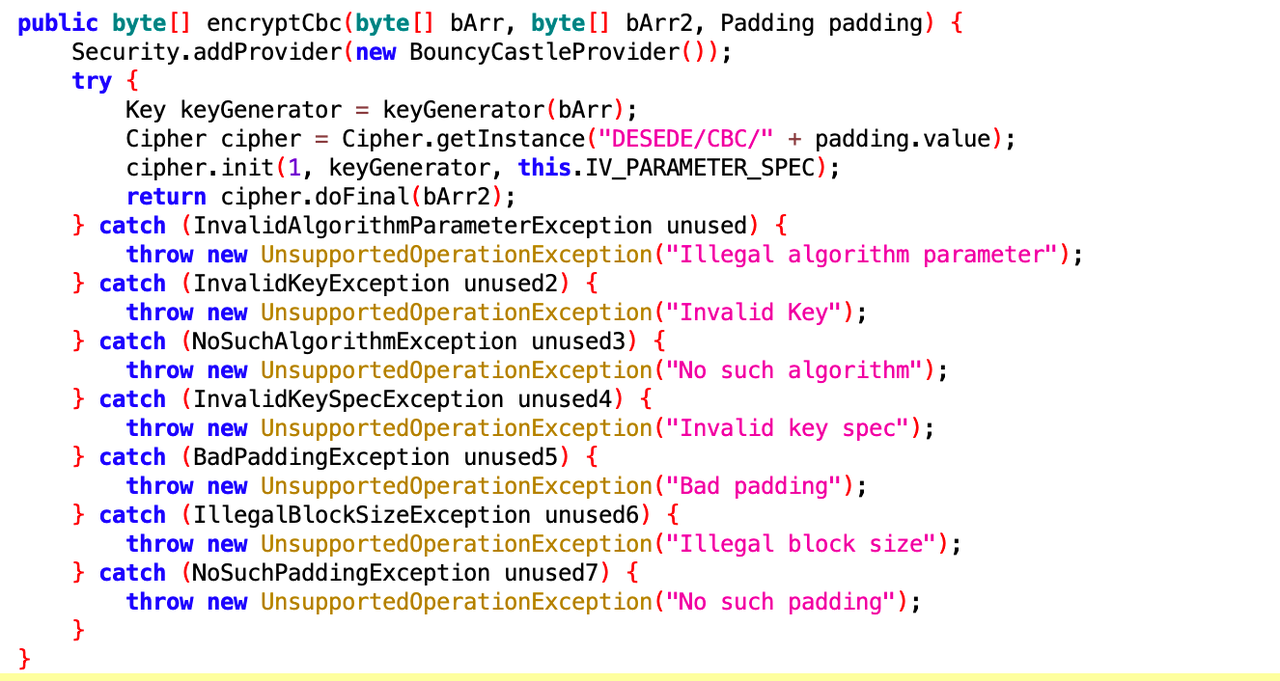
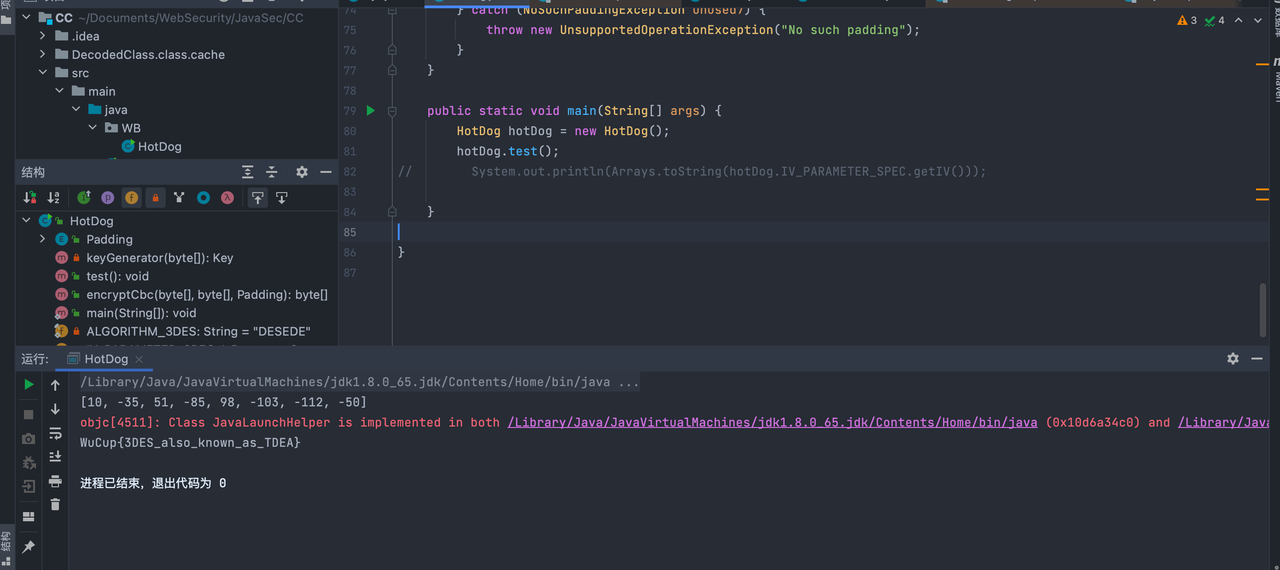
由于不清楚一段长数据如何转化为IV和key,所以直接把他代码拿来用:
1 | package WB; |
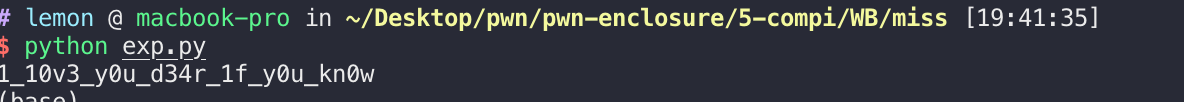
If you know
程序有upx的壳,去壳后:
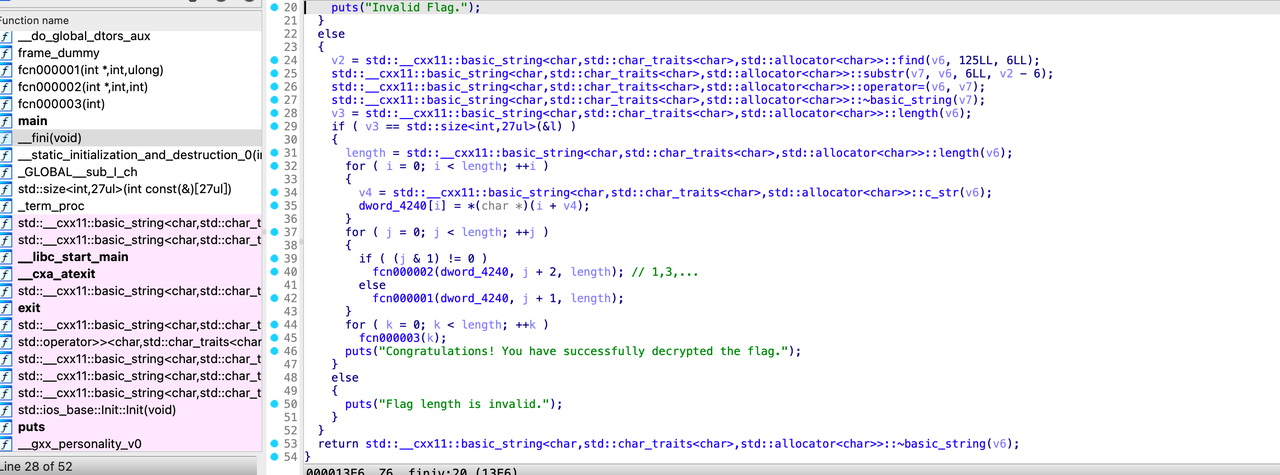
在fini中有flag加密逻辑:
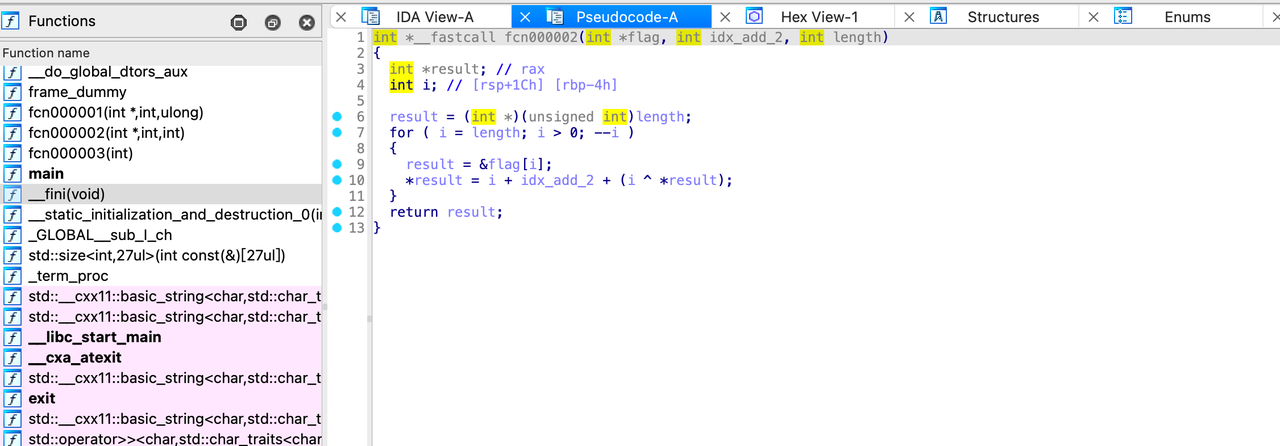
加密2:
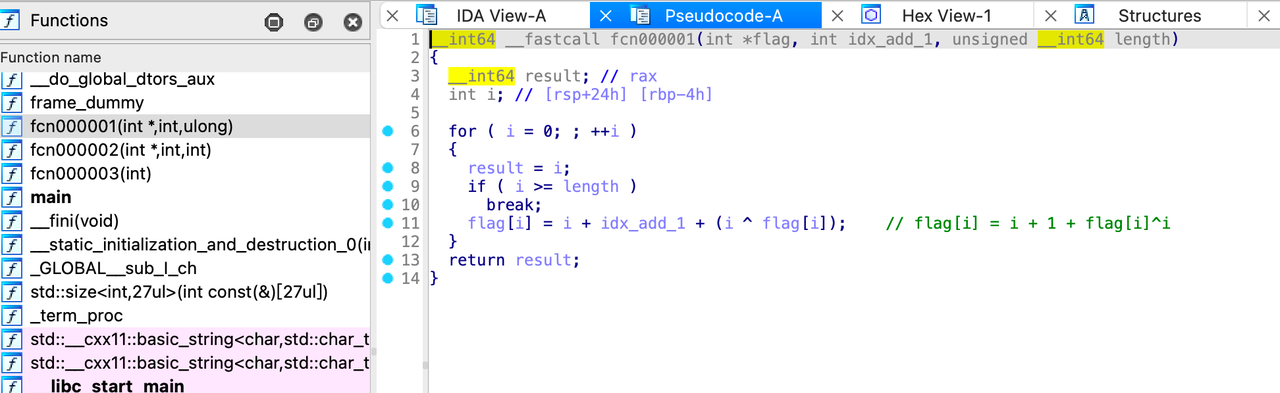
加密1:
简单的异或后偏移,解密脚本:
1 | l = [ |